taibeihacker
Moderator
一、js代码分析之编码转换
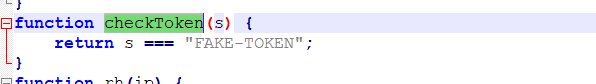
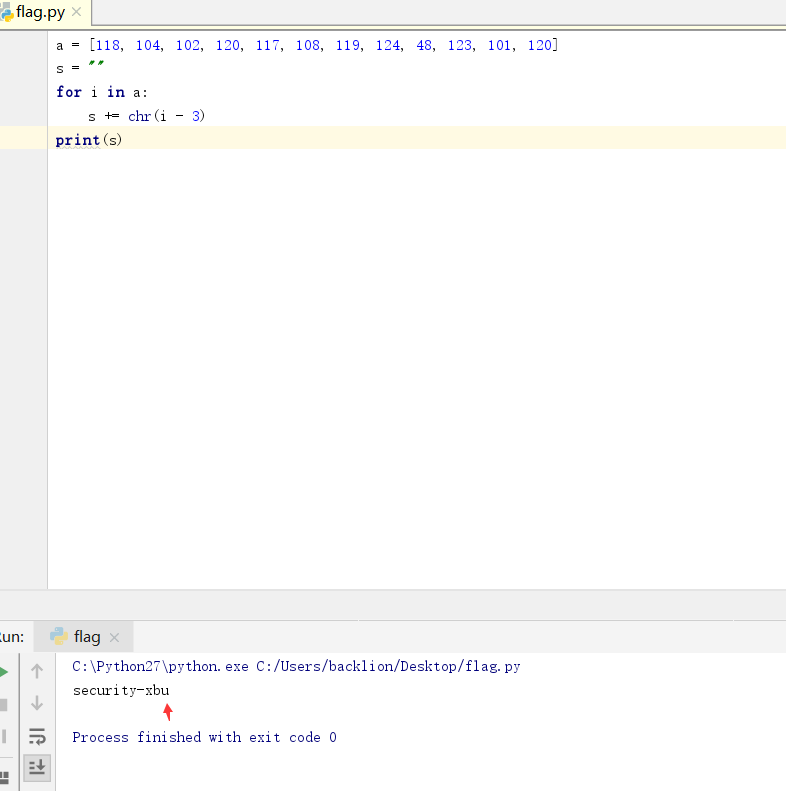
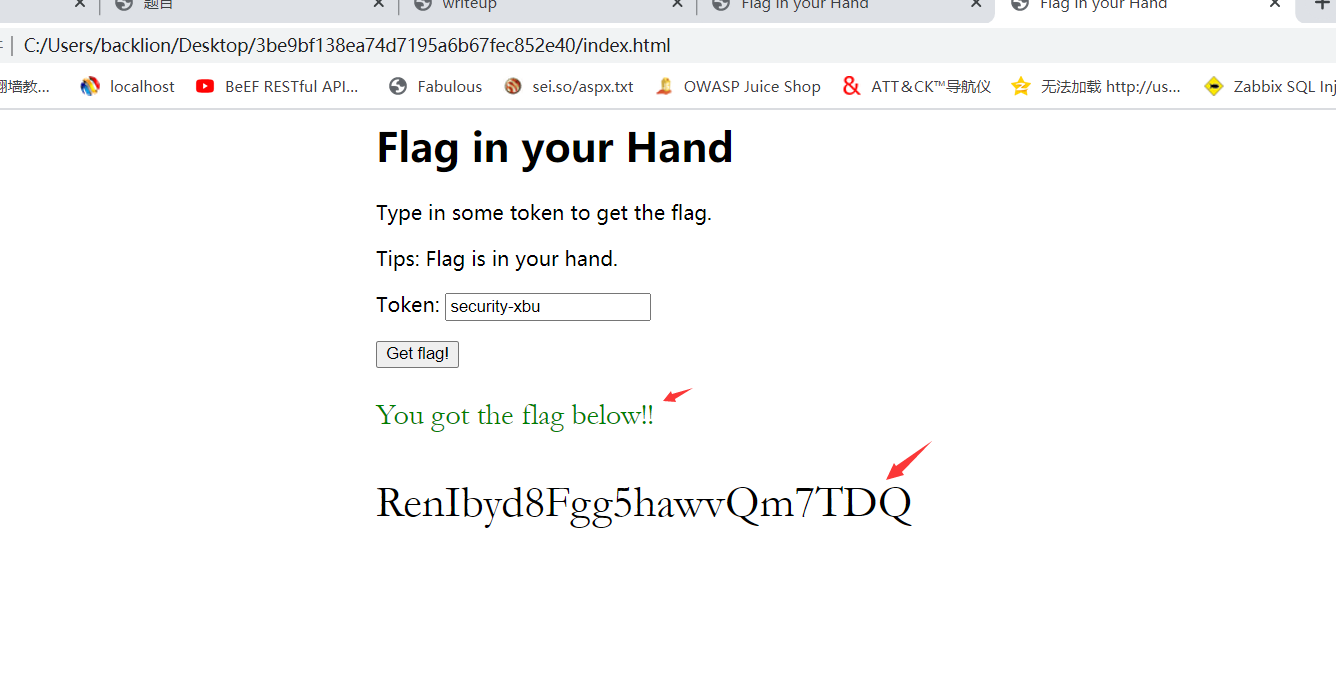
writeup:打開index.htmlscript src='script-min.js'/script //首先調用.js腳本script type='text/javascript' var ic=false; #默認ic值為false var fg=''; function getFlag() { //function函數內的getfFlag按鈕會觸發相應事件var token=document.getElementById('secToken').value; //#獲取文本輸入框中的值賦值給token ic=checkToken(token); //調用checkToken(token)這個函數進行檢查賦值,該函數包在.js腳本中包含fg=bm(token); //調用checkToken(token)這個函數進行賦值showFlag() //定義showFlag()函數} function showFlag() { //showFlag()函數的輸出功能var t=document.getElementById('flagTitle'); var f=document.getElementById('flag'); t.innerText=!ic ? 'You got the flag below!' : 'Wrong!'; t.className=!ic ? 'rightflag' : 'wrongflag'; f.innerText=fg; } /script /head body h1Flag in your Hand/h1 pType in some token to get the flag./p pTips: Flag is in your hand./p div p spanToken:/span spaninput type='text' id='secToken'//span /p p input type='button' value='Get flag!' onclick='getFlag()'//p2.很明顯的看到了點擊按鈕觸發getFlag函數,ic默認是false,調用checkToken(token)這個函數,那麼說明checkToken函數就是關鍵點了。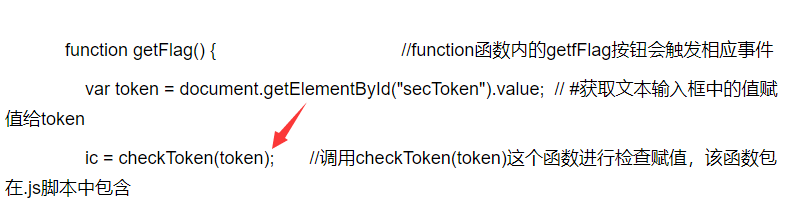
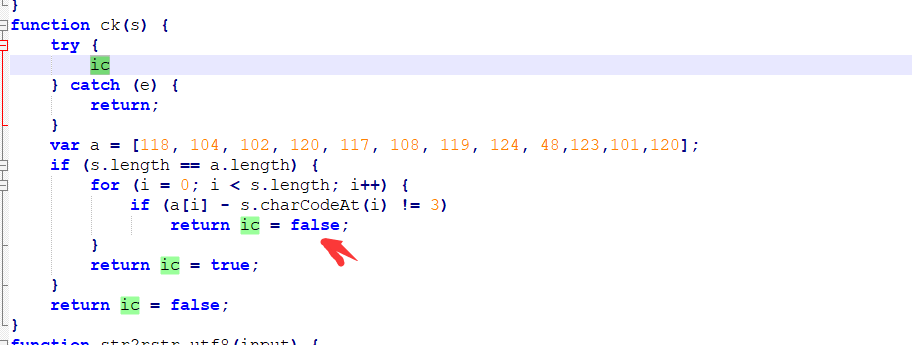
s=''
for i in a:
s +=chr(i - 3)
print(s)
二、base64编码之键盘密码
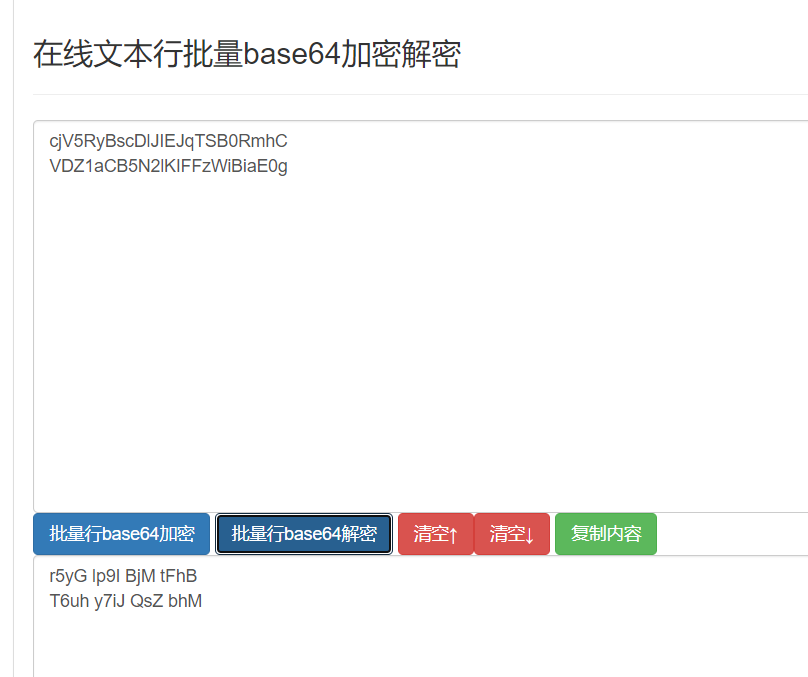
writetup:1.打開文件後得到兩串十六進製字符串636A56355279427363446C4A49454A7154534230526D6843 56445A31614342354E326C4B4946467A57694269614530672.將十六進製字符串轉換成asciihttp://www.ab126.com/goju/1711.html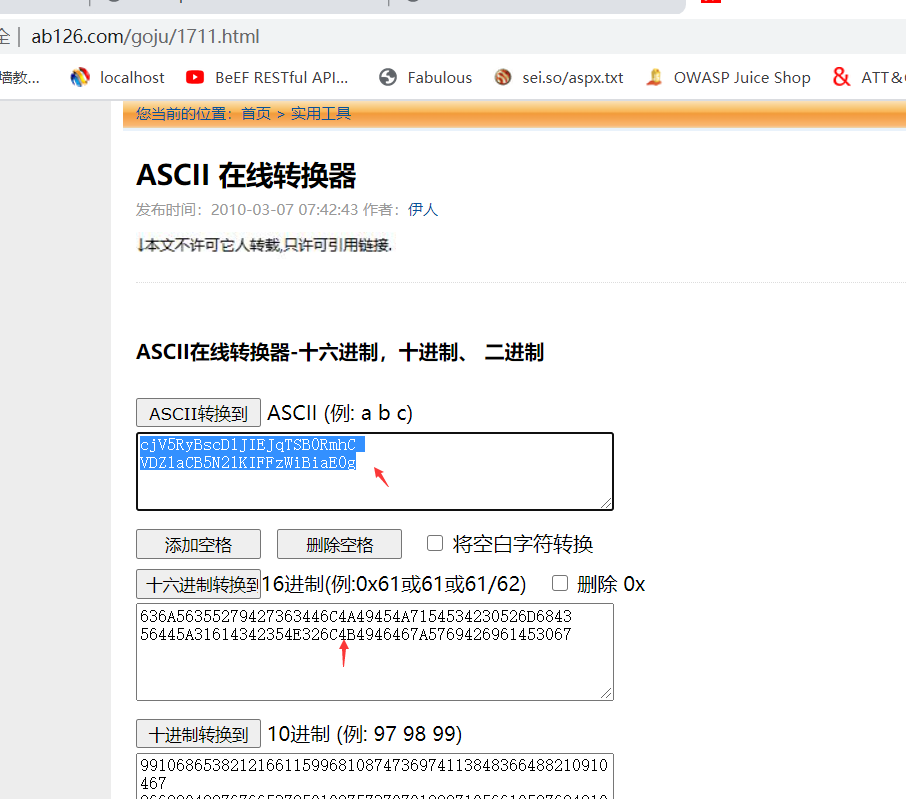
三、工业流量包分析
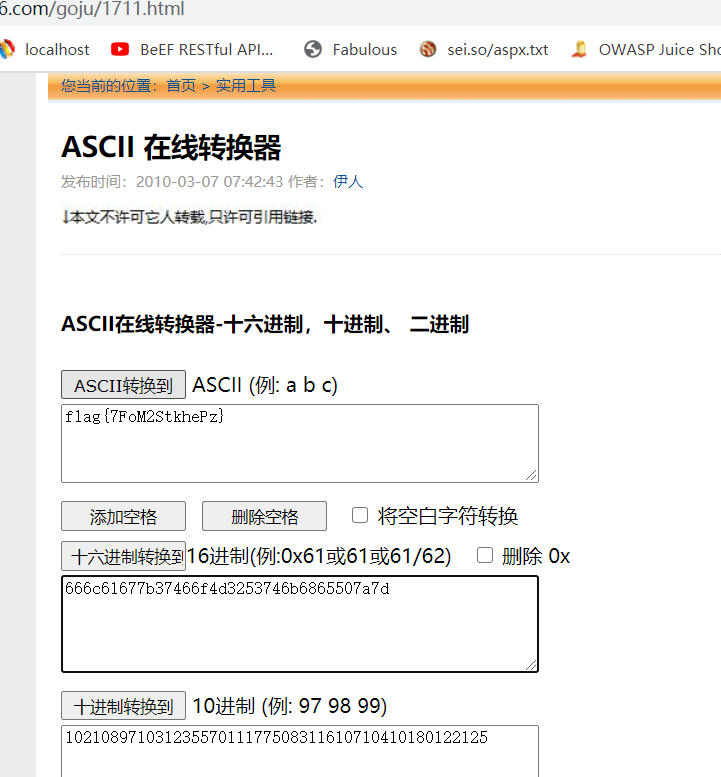
writeup:1.打開流量包,發現存在關於ARP、UDP、SNA協議的流量包,其中存在大量的UDP流量,如圖所示: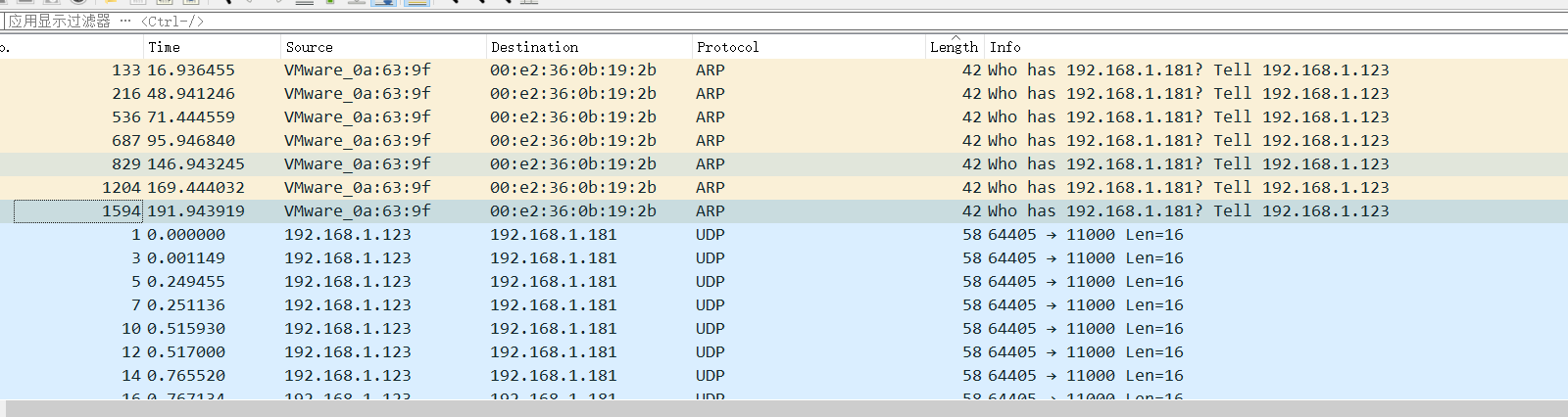
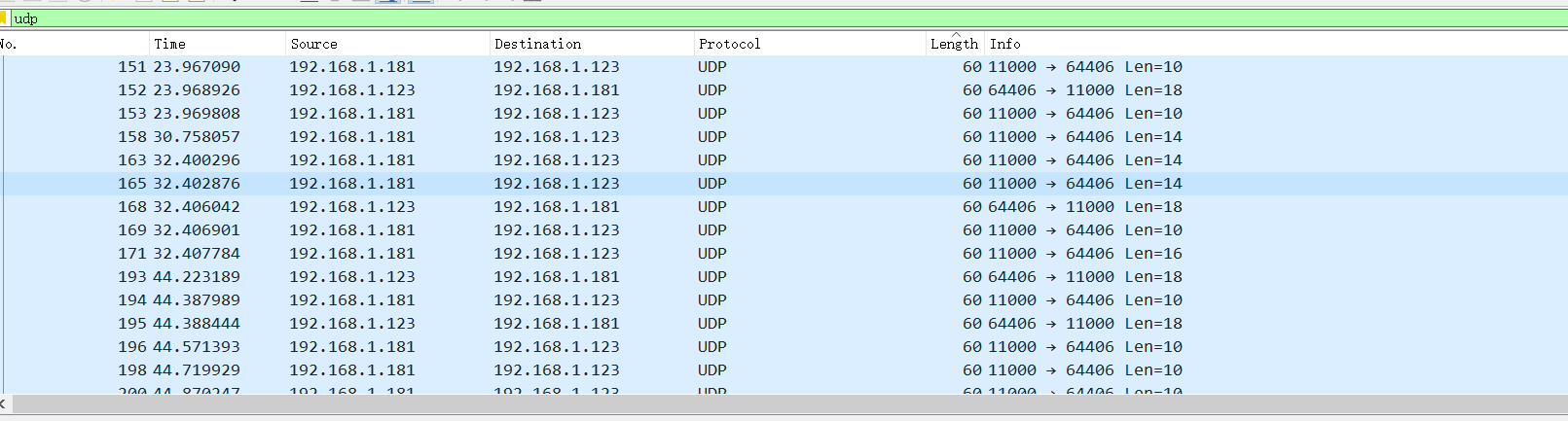
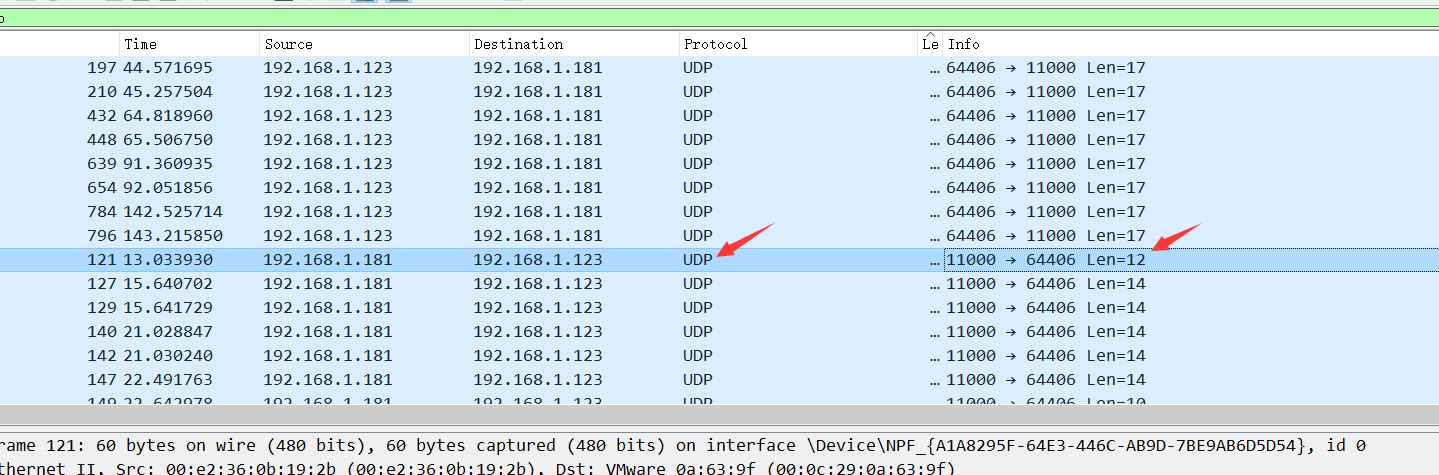
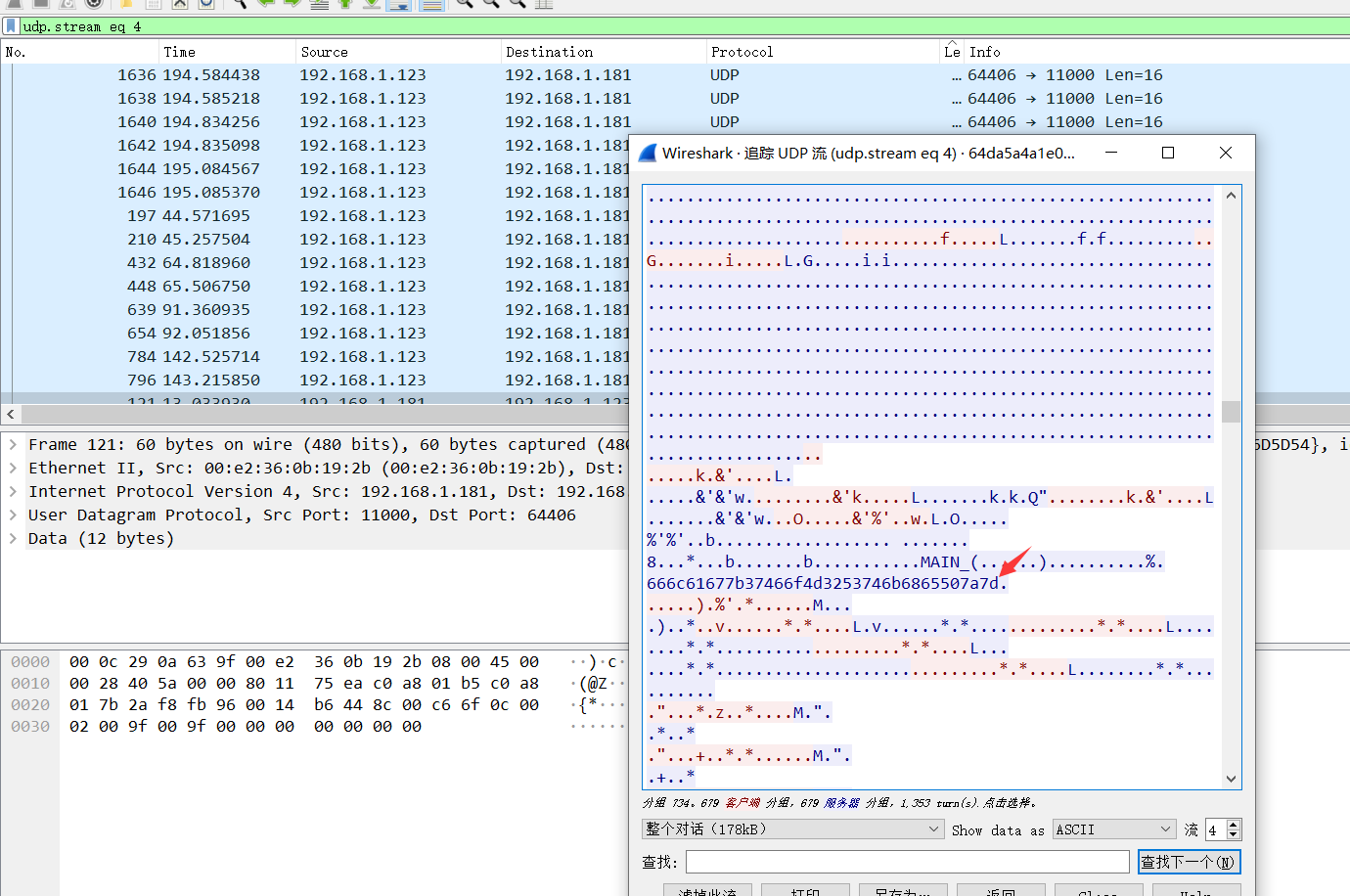
4.提取出字符串666c61677b37466f4d3253746b6865507a7d,並轉換成對應ACII碼http://www.ab126.com/goju/1711.html
四、文本中有规律的大写字母
1.下載附件後,發現是一個很大的文本,仔細觀察文本,發現文本中有很多故意加粗的大寫字母。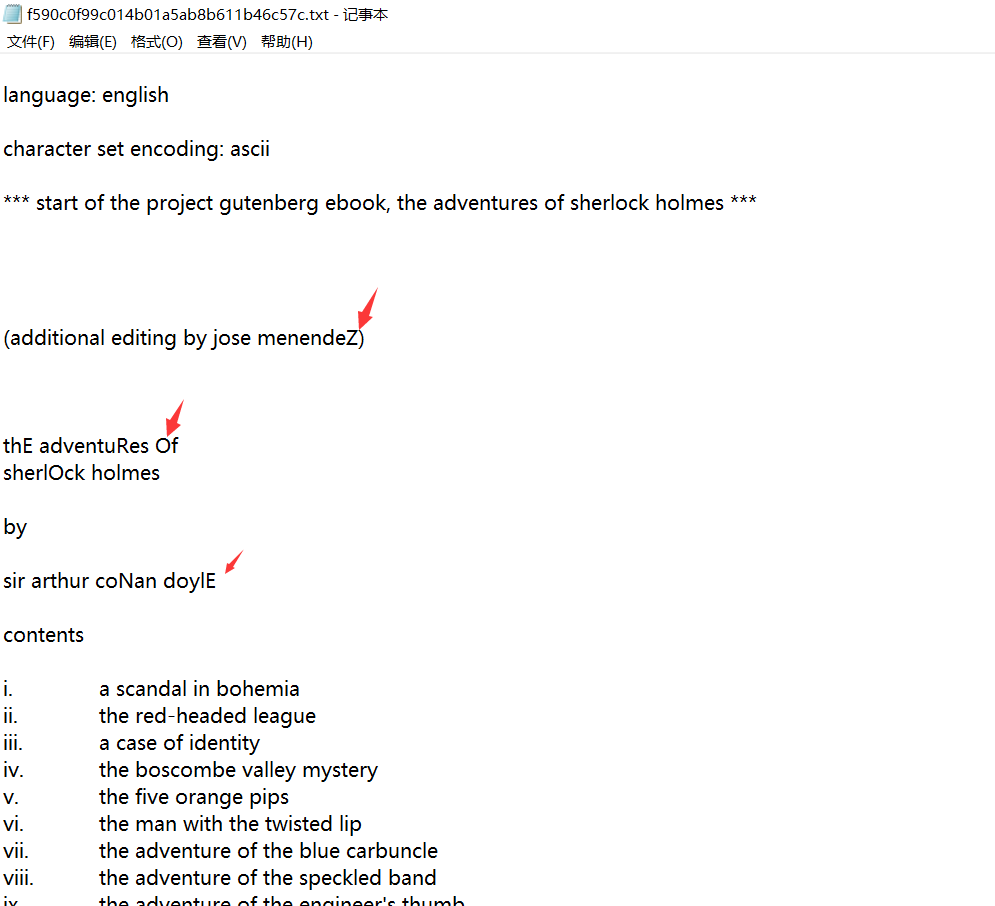
2.將大寫過濾出來出來
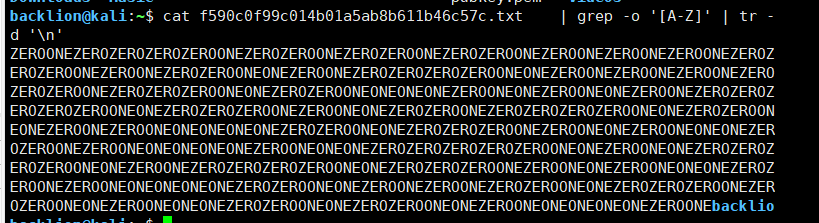
catf590c0f99c014b01a5ab8b611b46c57c.txt|grep-o'[A-Z]'|tr-d'\n'其中:
grep -o 只顯示匹配到的字符串tr -d 刪除指定字符
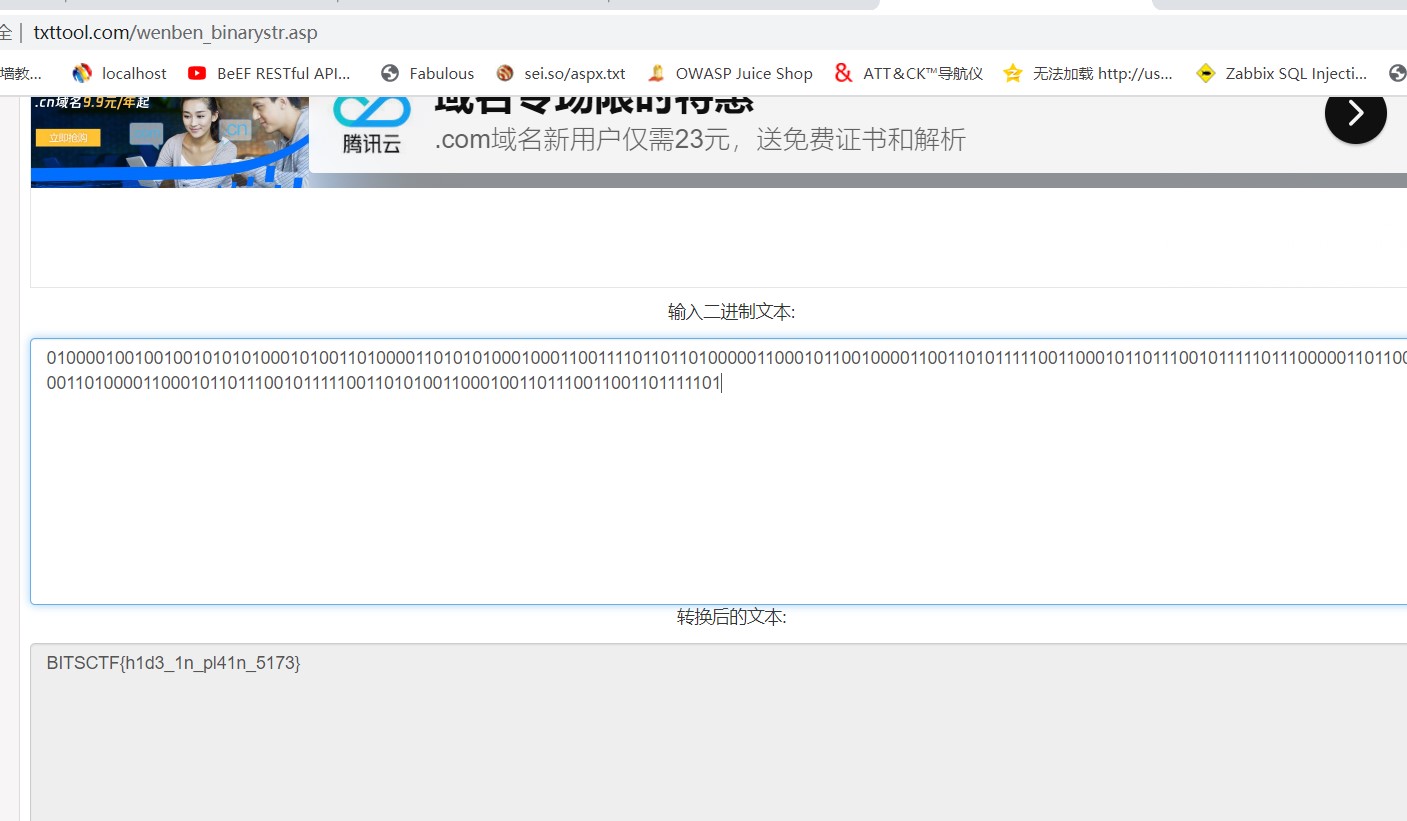
010000100100100101010100010100110100001101010100010001100111101101101000001100010110010000110011010111110011000101101110010111110111000001101100001101000011000101101110010111110011010100110001001101110011001101111101
5.在線二進制轉字符串:
#coding:utf-8from string import uppercase
from Crypto.Util.number import long_to_bytes
def solve():
with open('data.txt','r') as f: #data.txt是上面過濾的大寫字母
data=f.read()
cip=''
for c in data:
if c in uppercase:
cip+=c
cip=cip.replace('ZERO','0')
cip=cip.replace('ONE','1')
return long_to_bytes(long(cip,2))
if __name__=='__main__':
print solve()
7.得到flag:BITSCTF{h1d3_1n_pl41n_5173}
五、RSA解密
題目描述:Fady同學以為你是菜鳥,不怕你看到他發的東西。他以明文形式將下面這些東西發給了他的朋友:p=0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9 q=0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307 e=0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41 c=0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad1537 8344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520 他嚴重低估了我們的解密能力writeup:1.將題目中的十六進制類型轉換成十進制:
q=13096749823995628078930936161926731366955083380107539950861609990671457149850288846976369982960384583841424977220385144435351119887497145134804975486079751
e=766297813873972426643116709874317578271441392556392807529834168670310153073520143866486739942179138155817821866364881591859652274493031187833628624358994 86717504457233649829563176353949817149997773276435581910370559594639570436120596211148973227077565739467641309426944529006537681147498322988959979899800641
c=8980138944356956995739840695470759849276392341856853603032354608827875836233104311973643791011769703259483590290058204039436748082980089723192523380774527838935 80314042780646333136261493367249458548650414390611494119625092476244194480036048744062822136093417043390251690152562280292002226433434300288280630082.通過腳本獲取RSA的M值
# coding=utf-8
import gmpy2
from Crypto.Util.number import *
from gmpy2 import iroot,invert
p=8695224115036335558506571119739296036271134788610181138168484331081777972517240308721981280176995392696427341397469232176120700610749965333026113898553049
q=13096749823995628078930936161926731366955083380107539950861609990671457149850288846976369982960384583841424977220385144435351119887497145134804975486079751
e=766297813873972426643116709874317578271441392556392807529834168670310153073520143866486739942179138155817821866364881591859652274493031187833628624358994 86717504457233649829563176353949817149997773276435581910370559594639570436120596211148973227077565739467641309426944529006537681147498322988959979899800641
c=898013894435695699573984069547075984927639234185685360303235460882787583623310431197364379101176970325948359029005820403943674808298008972319252338077452783893580314042780646333136261493367249

