taibeihacker
Moderator
MISC
签到题
八道網絡安全選擇題,百度都能搜索到答案,這裡如果只知道部分題目答案,可以通過枚舉測試fuzz答案,獲得flag
flag:
flag{a236b34b-8040-4ea5-9e1c-97169aa3f43a}
RE
re693
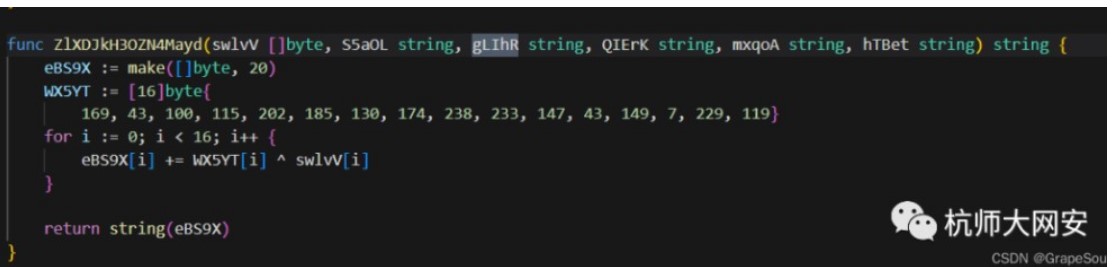
直接下載附件用golang打開看main函數可以發現會打印兩句話,要求輸入有六個參數並且第三個為gLIhR的函數、被調用三次並且會調用到cHZv5op8rOmlAkb6的函數
Input the first function, which has 6 parameters and the third named gLIhR:
輸入第一個函數,它有6 個參數,第三個名為gLIhR:
Input the second function, which has 3 callers and invokes the function named cHZv5op8rOmlAkb6:
輸入第二個函數,它有3 個調用者並調用名為cHZv5op8rOmlAkb6 的函數:
直接全局搜索,第一個函數為,ZlXDJkH3OZN4Mayd,有6個參數
func main() {
var nFAzj, CuSkl string
jjxXf :=[]byte{
37, 73, 151, 135, 65, 58, 241, 90, 33, 86, 71, 41, 102, 241, 213, 234, 67, 144, 139, 20, 112, 150, 41, 7, 158, 251, 167, 249, 24, 129, 72, 64, 83, 142, 166, 236, 67, 18, 211, 100, 91, 38, 83, 147, 40, 78, 239, 113, 232, 83, 227, 47, 192, 227, 70, 167, 201, 249, 156, 101, 216, 159, 116, 210, 152, 234, 38, 145, 198, 58, 24, 183, 72, 143, 136, 234, 246}
KdlaH :=[]byte{
191, 140, 114, 245, 142, 55, 190, 30, 161, 18, 200, 7, 21, 59, 17, 44, 34, 181, 109, 116, 146, 145, 189, 68, 142, 113, 0, 33, 46, 184, 21, 33, 66, 99, 124, 167, 201, 88, 133, 20, 211, 67, 133, 250, 62, 28, 138, 229, 105, 102, 125, 124, 208, 180, 50, 146, 67, 39, 55, 240, 239, 203, 230, 142, 20, 90, 205, 27, 128, 136, 151, 140, 222, 92, 152, 1, 222, 138, 254, 246, 223, 224, 236, 33, 60, 170, 189, 77, 124, 72, 135, 46, 235, 17, 32, 28, 245}
fmt.Print(MPyt9GWTRfAFNvb1(jjxXf))
fmt.Scanf('%20s', nFAzj)
fmt.Print(kZ2BFvOxepd5ALDR(KdlaH))
fmt.Scanf('%20s', CuSkl)
vNvUO :=GwSqNHQ7dPXpIG64(nFAzj)
YJCya :=''
mvOxK :=YI3z8ZxOKhfLmTPC(CuSkl)
if mvOxK !=nil {
YJCya=mvOxK()
}
if YJCya !='' vNvUO !='' {
fmt.Printf('flag{%s%s}\n', vNvUO, YJCya)
}
}
flag分為兩段,第一段為vNvUO,第二段為YJCya
第一段函數
func GwSqNHQ7dPXpIG64(cJPTR string) string {
YrXQd :=hex.EncodeToString([]byte(cJPTR))
return fmt.Sprintf('%c%c%c%c%c%c%c%c%c%c%c%c%c%c%c%c', YrXQd[22], YrXQd[19], YrXQd[20], YrXQd[21], YrXQd[28], YrXQd[10], YrXQd[20], YrXQd[7], YrXQd[29], YrXQd[14], YrXQd[0], YrXQd[18], YrXQd[3], YrXQd[24], YrXQd[27], YrXQd[31])
}
第一段exp
YrXQd=bytes.hex('ZlXDJkH3OZN4Mayd'.encode())
print(YrXQd[22], YrXQd[19], YrXQd[20], YrXQd[21], YrXQd[28], YrXQd[10], YrXQd[20], YrXQd[7], YrXQd[29], YrXQd[14], YrXQd[0], YrXQd[18], YrXQd[3], YrXQd[24], YrXQd[27], YrXQd[31],sep='')
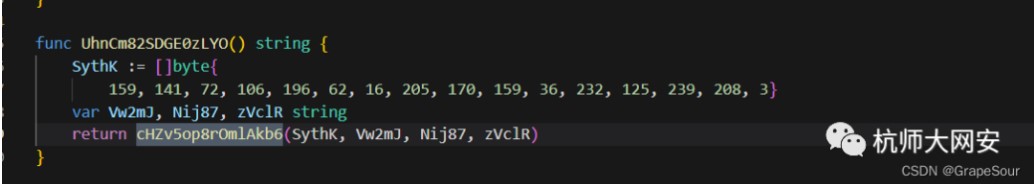
第二段涉及函數
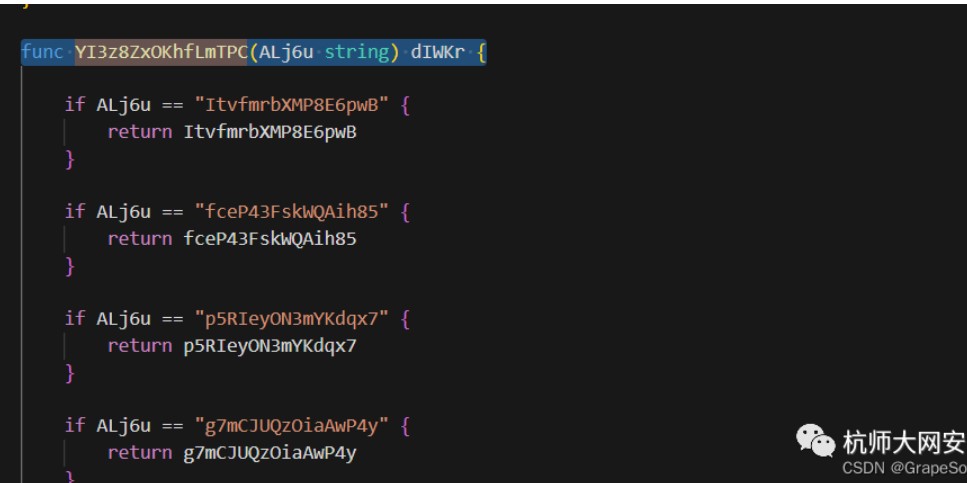
func UhnCm82SDGE0zLYO() string {
SythK :=[]byte{
159, 141, 72, 106, 196, 62, 16, 205, 170, 159, 36, 232, 125, 239, 208, 3}
var Vw2mJ, Nij87, zVclR string
return cHZv5op8rOmlAkb6(SythK, Vw2mJ, Nij87, zVclR)
}
func cHZv5op8rOmlAkb6(HIGXt []byte, VGvny string, ZOkKV string, eU0uD string) string {
QTk4l :=make([]byte, 20)
Ek08m :=[16]byte{
167, 238, 45, 89, 160, 95, 34, 175, 158, 169, 20, 217, 68, 137, 231, 54}
for i :=0; i 16; i++ {
QTk4l +=Ek08m ^ HIGXt
}
return string(QTk4l)
}
其中後面幾個Vw2mJ, Nij87, zVcl,參數為無效參數
exp:
QTk4l=[0]*16
SythK=[159, 141, 72, 106, 196, 62, 16, 205, 170, 159, 36, 232, 125, 239, 208, 3]
Ek08m=[167, 238, 45, 89, 160, 95, 34, 175, 158, 169, 20, 217, 68, 137, 231, 54]
for i in range(16):
QTk4l=chr(Ek08m ^ SythK)
for i in QTk4l:
print(i,end='')
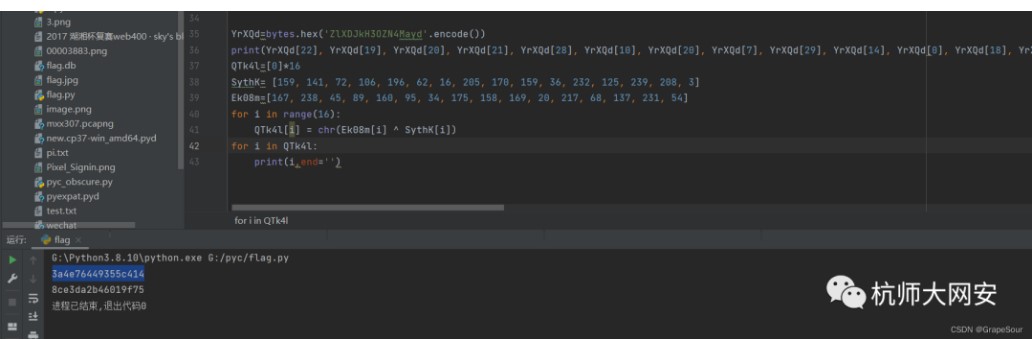
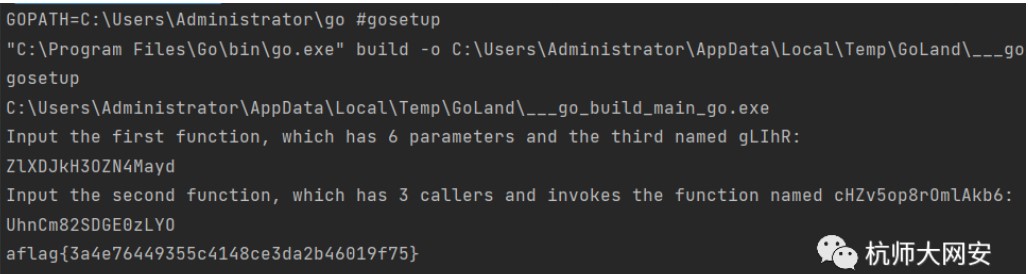
flag{3a4e76449355c4148ce3da2b46019f75}
re694
IDA打開,找關鍵字符串,再定位到關鍵函數
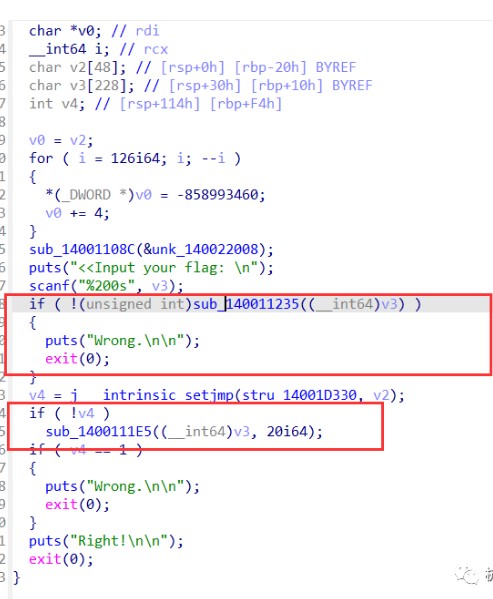
兩個關鍵的判斷函數,第一個進去發現判斷是否為20長,然後再輸入的值異或上0x66
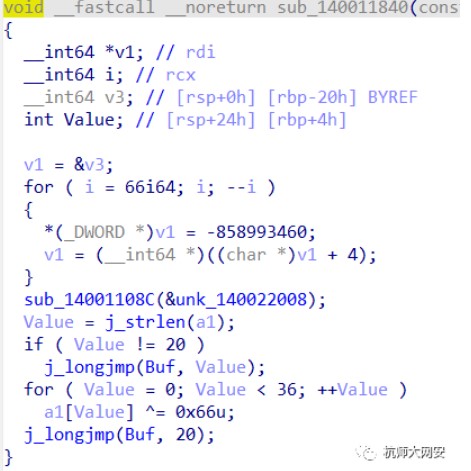
第二個判斷函數,是將第一個判斷後的值加上10再異或0x50,再和dword_14001D000裡的數比較
即是$flag=((enc \oplus0x50)-10)\oplus0x66$
x=['4B', '48', '79', '13', '45', '30', '5C', '49', '5A', '79', '13', '70', '6D', '78', '13', '6F', '48', '5D', '64', '64']
for i in x:
print(chr(((int(i, 16) ^0x50) - 10) ^0x66), end='')
flag:
flag{why_m0dify_pUx_SheLL}
CRYPTO
crypto091
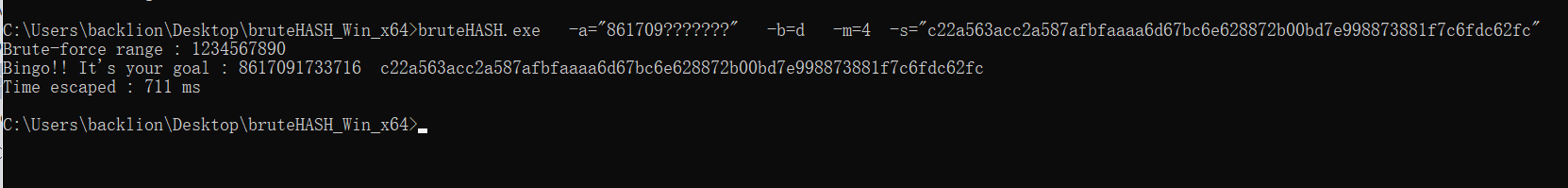
根據描述和其中提到的論文,Hash值為電話號碼的sha256170號段首批放號的聯通號碼以1709開頭,直接爆破即可:
x='c22a563acc2a587afbfaaaa6d67bc6e628872b00bd7e998873881f7c6fdc62fc'
import hashlib
n=b'861709'
s=list('0123456789'.strip())
import itertools
for i in itertools.product(s,repeat=7):
d=''.join(i).encode()
g=n+d
if hashlib.sha256(g).hexdigest()==x:
print(g)
break
# b'8617091733716'
或者
crypto162
from secret import flagfrom hashlib import md5,sha256
from Crypto.Cipher import AES
cof_t=[[353, -1162, 32767], [206, -8021, 42110], [262, -7088, 31882], [388, -6394, 21225], [295, -9469, 44468], [749, -3501, 40559], [528, -2690, 10210], [354, -5383, 18437], [491, -8467, 26892], [932, -6984, 20447], [731, -6281, 11340], [420, -5392, 44071], [685, -6555, 40938], [408, -8070, 47959], [182, -9857, 49477], [593, -3584, 49243], [929, -7410, 31929], [970, -4549, 17160], [141, -2435, 36408], [344, -3814, 18949], [291, -7457, 40587], [765, -7011, 32097], [700, -8534, 18013], [267, -2541, 33488], [249, -8934, 12321], [589, -9617, 41998], [840, -1166, 22814], [947, -5660, 41003], [206, -7195, 46261], [784, -9270, 28410], [338, -3690, 19608], [559, -2078, 44397], [534, -3438, 47830], [515, -2139, 39546], [603, -6460, 49953], [234, -6824, 12579], [805, -8793, 36465], [245, -5886, 21077], [190, -7658, 20396], [392, -7053, 19739], [609, -5399, 39959], [479, -8172, 45734], [321, -7102, 41224], [720, -4487, 11055], [208, -1897, 15237], [890, -4427, 35168], [513, -5106, 45849], [666, -1137, 23725], [755, -6732, 39995], [589, -6421, 43716], [866, -3265, 30017], [416, -6540, 34979], [840, -1305, 18242], [731, -6844, 13781], [561, -2728, 10298], [863, -5953, 23132], [204, -4208, 27492], [158, -8701, 12720], [802, -4740, 16628], [491, -6874, 29057], [531, -4829, 29205], [363, -4775, 41711], [319, -9206, 46164], [317, -9270, 18290], [680, -5136, 12009], [880, -2940, 34900], [162, -2587, 49881], [997, -5265, 20890], [485, -9395, 23048], [867, -1652, 18926], [691, -7844, 11180], [355, -5990, 13172], [923, -2018, 23110], [214, -4719, 23005], [921, -9528, 29351], [349, -7957, 20161], [470, -1889, 46170], [244, -6106, 23879], [419, -5440, 43576], [930, -1123, 29859], [151, -5759, 23405], [843, -6770, 36558], [574, -6171, 33778], [772, -1073, 44718], [932, -4037, 40088], [848, -5813, 27304], [194, -6016, 39770], [966, -6789, 14217], [219, -6849, 40922], [352, -6046, 18558], [794, -8254, 29748], [618, -5887, 15535], [202, -9288, 26590], [611, -4341, 46682], [155, -7909, 16654], [935, -5739, 39342], [998, -6538, 24363], [125, -5679, 36725], [507, -7074, 15475], [699, -5836, 47549]]
defcal(i,cof):
if i 3:
return i+1
else:
return cof[2]*cal(i-3,cof)+cof[1]*cal(i-2,cof)+cof[0]*cal(i-1,cof)
s=0
for i inrange(100):
s +=cal(200000,cof_t)
print(s)
s=str(s)[-2000:-1000]
key=md5(s).hexdigest().decode('hex')
check=sha256(key).hexdigest()
verify='2cf44ec396e3bb9ed0f2f3bdbe4fab6325ae9d9ec3107881308156069452a6d5'
assert(check==verify)
aes=AES.new(key,AES.MODE_ECB)
data=flag + (16-len(flag)%16)*'\x00'
print (aes.encrypt(data).encode('hex'))
#4f12b3a3eadc4146386f4732266f02bd03114a404ba4cb2dabae213ecec451c9d52c70dc3d25154b5af8a304afafed87
根據題目提示,想到將遞歸公式轉換成矩陣(參考線性代數求解遞推形式數列的通項公式_wdq347的博客-CSDN博客)
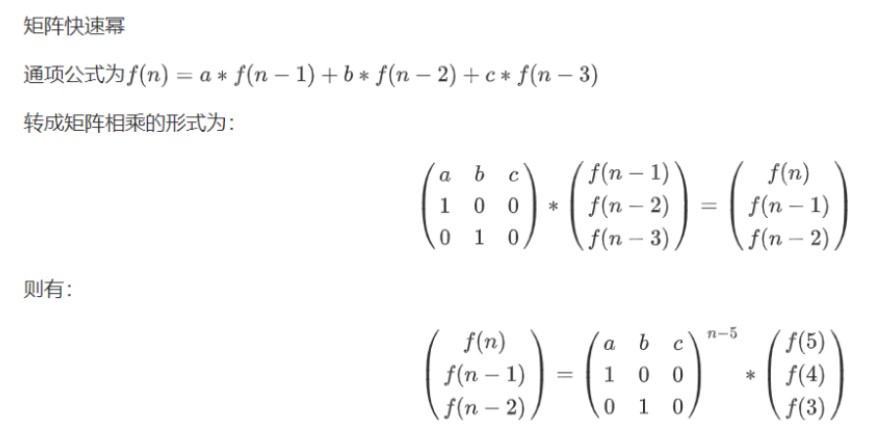
from hashlib import md5, sha256
from Crypto.Cipher import AES
cof_t=[[353, -1162, 32767], [206, -8021, 42110], [262, -7088, 31882], [388, -6394, 21225], [295, -9469, 44468], [749, -3501, 40559], [528, -2690, 10210], [354, -5383, 18437], [491, -8467, 26892], [932, -6984, 20447], [731, -6281, 11340], [420, -5392, 44071], [685, -6555, 40938], [408, -8070, 47959], [182, -9857, 49477], [593, -3584, 49243], [929, -7410, 31929], [970, -4549, 17160], [141, -2435, 36408], [344, -3814, 18949], [291, -7457, 40587], [765, -7011, 32097], [700, -8534, 18013], [267, -2541, 33488], [249, -8934, 12321], [589, -9617, 41998], [840, -1166, 22814], [947, -5660, 41003], [206, -7195, 46261], [784, -92

