taibeihacker
Moderator
1.Red Teaming VS Penetration Testing VS漏洞测试
基於威脅的安全測試方法可能使用多個名稱;紅隊、威脅操作、威脅評估、紫隊、對抗評估、滲透測試、漏洞測試。這些並非完全相同,安全行業定義用於建立共同理解的術語非常重要。為了解決這個問題,本文中所有基於威脅的安全測試都將被稱為Red Teaming。定義:紅色團隊是使用戰術、技術和過程(TTP)來模擬現實世界攻擊的過程,其目標是訓練和衡量用於保護系統環境的人員、過處理流程和技術的有效性。換句話說,紅隊是使用真實攻擊技術來模擬攻擊的過程,目的是培訓藍隊和/或測量整個安全操作。
紅色團隊可以深入了解自動攻擊行為者對目標的影響。使用反金字塔圖,我們可以說明紅隊,滲透測試和漏洞評估之間的關係。這將有助於進一步定義Red Teaming IS和IS NOT。
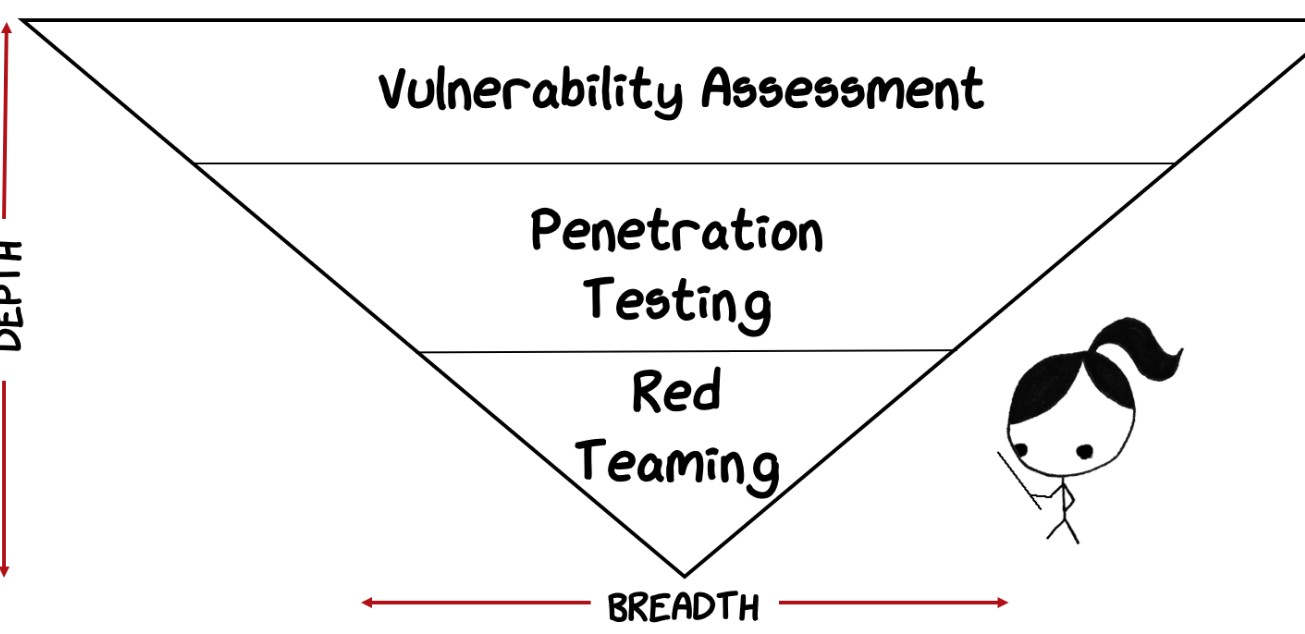
脆弱性評估:脆弱性評估往往覆蓋範圍廣。考慮對所有企業工作站進行漏洞評估。範圍很廣,但在對企業組織受到風險的背景下了解不是很深。當發現漏洞時,對漏洞風險能說明什麼呢?企業組織的總體風險可能會在很小程度上推斷,但通常會保持在該工作站級別。漏洞評估擅長減少攻擊面,但在企業組織風險方面沒有提供太多細節。
滲透測試:通過利用和證明攻擊路徑將漏洞評估提升到新的水平。滲透測試通常看起來和感覺像一個紅色團隊的參與,甚至使用一些相同的工具或技術。關鍵的區別在於目標和意圖。滲透測試的目標是對目標系統執行攻擊,以識別和測量與目標攻擊面的利用相關的風險。企業組織風險可以間接衡量,通常從某些技術攻擊中推斷出來。人員和流程怎麼樣?這就是紅隊適合的地方。紅隊注重整體安全操作,包括人員、流程和技術。紅隊特別關注與培訓藍隊或衡量安全操作如何影響威脅的操作能力相關的目標。技術缺陷是理解威脅如何影響組織的操作或安全操作如何影響威脅的操作能力的次要因素。
3.红队参考
描述地址紅隊:如何像敵人一樣思考- Micha Zenko
Red Team
Read excerpts from Red Team.Red teaming is a practice as old as the role of the Devil’s Advocate, the eleventh-century Vatican official charged with discrediting candidates for sainthood. Today, red …

Blog - Cobalt Strike
The Cobalt Strike Blog. Read new featured content, get updates on the latest patches, and insights into the future of red teaming tools.
 blog.cobaltstrike.com
blog.cobaltstrike.com

Posts By SpecterOps Team Members
Posts from SpecterOps team members on various topics relating information security.
 posts.specterops.io
posts.specterops.io
GitHub - harleyQu1nn/AggressorScripts: Collection of Aggressor scripts for Cobalt Strike 3.0+ pulled from multiple sources
Collection of Aggressor scripts for Cobalt Strike 3.0+ pulled from multiple sources - harleyQu1nn/AggressorScripts
GitHub - bluscreenofjeff/AggressorScripts: Aggressor scripts for use with Cobalt Strike 3.0+
Aggressor scripts for use with Cobalt Strike 3.0+. Contribute to bluscreenofjeff/AggressorScripts development by creating an account on GitHub.
GitHub - yeyintminthuhtut/Awesome-Red-Teaming: List of Awesome Red Teaming Resources
List of Awesome Red Teaming Resources. Contribute to yeyintminthuhtut/Awesome-Red-Teaming development by creating an account on GitHub.
2.1 红队基础设施
有關構建紅隊基礎架構的提示和技巧描述地址紅隊基礎設施文庫
GitHub - bluscreenofjeff/Red-Team-Infrastructure-Wiki: Wiki to collect Red Team infrastructure hardening resources
Wiki to collect Red Team infrastructure hardening resources - bluscreenofjeff/Red-Team-Infrastructure-Wiki
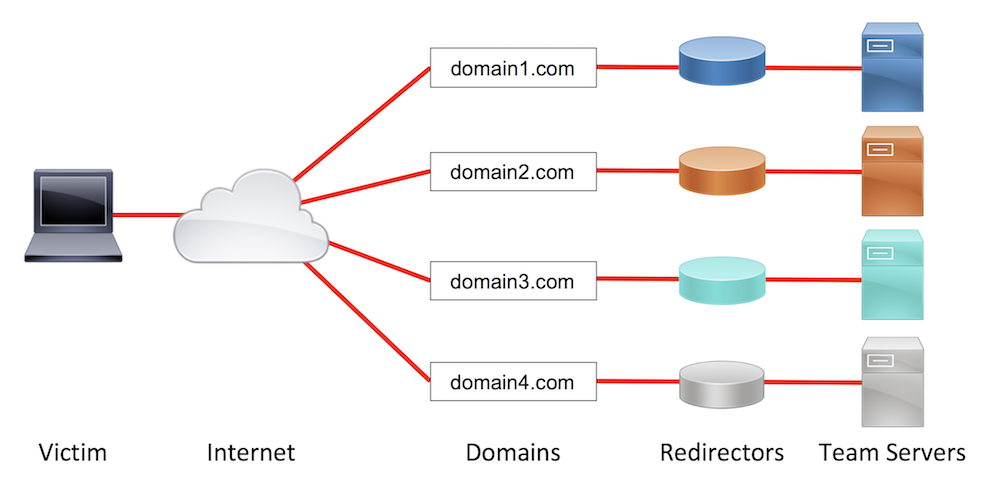
Designing Effective Covert Red Team Attack Infrastructure
Covert red team attack infrastructure is a topic I’ve covered many times before, but always only in part. I’ve wanted to write about the thought process behind the design process of attack infrastructure for a while. In October, I had the privilege of covering that very topic at ArcticCon in...

Cobalt Strike HTTP C2 Redirectors with Apache mod_rewrite
Imagine you are performing a Red Team engagement. So far it’s been very hard, fighting tooth and nail to get each step closer to totally owning their network. You finally get internal network access and things are stable. Everything looks good on your end, but on the Blue side of things IT is...
SSL證書安裝/透明度報告
SSL證書安裝/透明度報告
Google Transparency Report
2.2.红队工具
基於Get In,Stay In和Act基礎以及Cyber Kill Chain的重要紅隊工具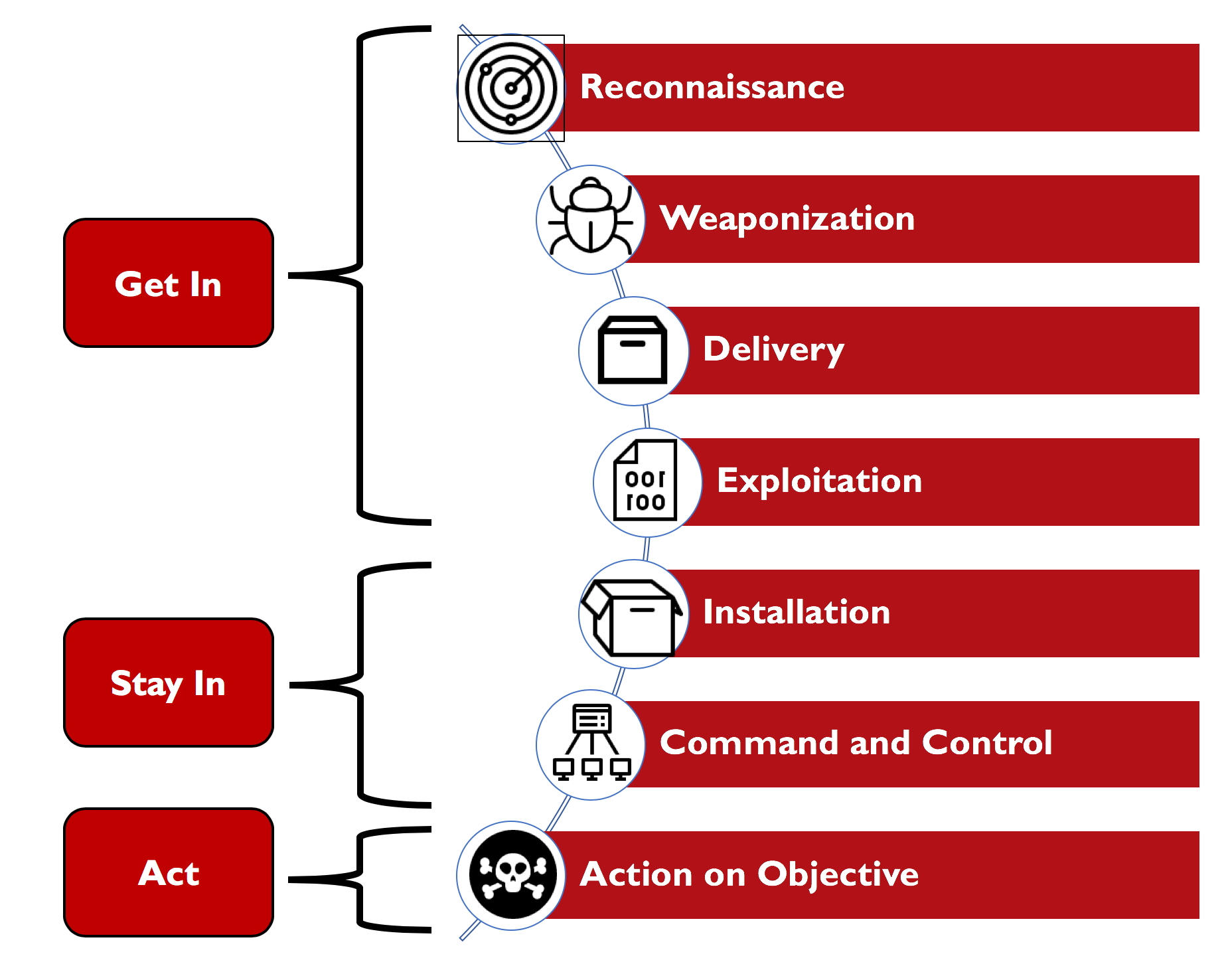
2.3.获得权限
偵察信息收集工具
描述地址BloodHound
GitHub - SpecterOps/BloodHound-Legacy: Six Degrees of Domain Admin
Six Degrees of Domain Admin. Contribute to SpecterOps/BloodHound-Legacy development by creating an account on GitHub.
GitHub - threatexpress/domainhunter: Checks expired domains for categorization/reputation and Archive.org history to determine good candidates for phishing and C2 domain names
Checks expired domains for categorization/reputation and Archive.org history to determine good candidates for phishing and C2 domain names - threatexpress/domainhunter
GitHub - ChrisTruncer/EyeWitness: EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible.
EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. - ChrisTruncer/EyeWitness
GitHub - dafthack/MailSniper: MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It can be used as a non-admi
MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It ca...
Nmap: the Network Mapper - Free Security Scanner
Nmap Free Security Scanner, Port Scanner, & Network Exploration Tool. Download open source software for Linux, Windows, UNIX, FreeBSD, etc.
Shodan
OPSEC對Beacon命令的注意事項

Blog - Cobalt Strike
The Cobalt Strike Blog. Read new featured content, get updates on the latest patches, and insights into the future of red teaming tools.
 blog.cobaltstrike.com
blog.cobaltstrike.com
用於創建有效payload的工具
描述地址CACTUSTORCH
GitHub - mdsecactivebreach/CACTUSTORCH: CACTUSTORCH: Payload Generation for Adversary Simulations
CACTUSTORCH: Payload Generation for Adversary Simulations - mdsecactivebreach/CACTUSTORCH
GitHub - secretsquirrel/the-backdoor-factory: Patch PE, ELF, Mach-O binaries with shellcode new version in development, available only to sponsors
Patch PE, ELF, Mach-O binaries with shellcode new version in development, available only to sponsors - secretsquirrel/the-backdoor-factory
GitHub - trustedsec/unicorn: Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber's powershell attacks and the powershell bypass technique presented by David Kennedy (Tru
Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber's powershell attacks and the powershell bypass technique pre...
The Veil-Framework
The Veil-Framework has 6 repositories available. Follow their code on GitHub.
Ten process injection techniques: A technical survey of common and trending process injection techniques
Process injection is a widespread defense evasion technique employed often within malware and fileless adversary tradecraft, and entails running custom code within the address space of another process...
初始訪問和有效payload交付的工具
描述地址Social Engineering Toolkit
GitHub - trustedsec/social-engineer-toolkit: The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here. - trustedsec/social-engineer-toolkit
GitHub - Raikia/FiercePhish: FiercePhish is a full-fledged phishing framework to manage all phishing engagements. It allows you to track separate phishing campaigns, schedule sending of emails, and much more.
FiercePhish is a full-fledged phishing framework to manage all phishing engagements. It allows you to track separate phishing campaigns, schedule sending of emails, and much more. - Raikia/FierceP...
利用工具
描述地址Burp Suite

Burp Suite - Application Security Testing Software
Get Burp Suite. The class-leading vulnerability scanning, penetration testing, and web app security platform. Try for free today.
OffSec’s Exploit Database Archive
The Exploit Database - Exploits, Shellcode, 0days, Remote Exploits, Local Exploits, Web Apps, Vulnerability Reports, Security Articles, Tutorials and more.

Metasploit | Penetration Testing Software, Pen Testing Security | Metasploit
Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the world's best penetration testing software now.
2.4.维持权限
安裝用於持久性和有效payload安裝的工具
描述地址Windows權限清單
Checklists/Windows-Privilege-Escalation.md at master · netbiosX/Checklists
Red Teaming & Pentesting checklists for various engagements - netbiosX/Checklists
PowerSploit
GitHub - PowerShellMafia/PowerSploit: PowerSploit - A PowerShell Post-Exploitation Framework
PowerSploit - A PowerShell Post-Exploitation Framework - PowerShellMafia/PowerSploit
命令和控制工具與框架
描述地址Empire
CobaltStrike
Cobalt Strike | Adversary Simulation and Red Team Operations
Cobalt Strike is an adversary simulation tool that can emulate the tactics and techniques of a quiet long-term embedded threat actor in an IT network using Beacon, a post-exploitation agent and covert channels.
 cobaltstrike.com
cobaltstrike.com
PoshC2
GitHub - nettitude/PoshC2: A proxy aware C2 framework used to aid red teamers with post-exploitation and lateral movement.
A proxy aware C2 framework used to aid red teamers with post-exploitation and lateral movement. - nettitude/PoshC2
GitHub - n1nj4sec/pupy: Pupy is an opensource, cross-platform (Windows, Linux, OSX, Android) C2 and post-exploitation framework written in python and C
Pupy is an opensource, cross-platform (Windows, Linux, OSX, Android) C2 and post-exploitation framework written in python and C - n1nj4sec/pupy
GitHub - Ne0nd0g/merlin: Merlin is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang.
Merlin is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang. - Ne0nd0g/merlin

Metasploit | Penetration Testing Software, Pen Testing Security | Metasploit
Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the world's best penetration testing software now.
GitHub - threatexpress/tinyshell
Contribute to threatexpress/tinyshell development by creating an account on GitHub.
GitHub - silentbreaksec/Throwback: HTTP/S Beaconing Implant
HTTP/S Beaconing Implant. Contribute to silentbreaksec/Throwback development by creating an account on GitHub.
GitHub - RedSiege/WMImplant: This is a PowerShell based tool that is designed to act like a RAT. Its interface is that of a shell where any command that is supported is translated into a WMI-equivalent for use on a network/remote machine. WMImplant i
This is a PowerShell based tool that is designed to act like a RAT. Its interface is that of a shell where any command that is supported is translated into a WMI-equivalent for use on a network/rem...
2.5.行动
對目標採取行動在目標上執行操作的工具
描述地址Misc PowerShell Post Exploitation Scripts
GitHub - rvrsh3ll/Misc-Powershell-Scripts: Random Tools
Random Tools. Contribute to rvrsh3ll/Misc-Powershell-Scripts development by creating an account on GitHub.
hashcat - advanced password recovery
World's fastest and most advanced password recovery utility
GhostPack
A collection of security related toolsets. GhostPack has 18 repositories available. Follow their code on GitHub.

New lateral movement techniques abuse DCOM technology
The arsenal of lateral movement techniques was expanded with new methods that abuse the DCOM functionality of Windows applications.
GitHub - gentilkiwi/mimikatz: A little tool to play with Windows security
A little tool to play with Windows security. Contribute to gentilkiwi/mimikatz development by creating an account on GitHub.
PowerSploit/Privesc/PowerUp.ps1 at master · PowerShellMafia/PowerSploit
PowerSploit - A PowerShell Post-Exploitation Framework - PowerShellMafia/PowerSploit
WMIOps
GitHub - RedSiege/WMIOps: This repo is for WMIOps, a powershell script which uses WMI for various purposes across a network.
This repo is for WMIOps, a powershell script which uses WMI for various purposes across a network. - RedSiege/WMIOps
2.6.NET
描述地址James Forshaw的OleView .NET項目
Finding Interactive User COM Objects using PowerShell
Easily one of the most interesting blogs on Windows behaviour is Raymond Chen's The Old New Thing . I noticed he'd recently posted about us...
GitHub - tyranid/DotNetToJScript: A tool to create a JScript file which loads a .NET v2 assembly from memory.
A tool to create a JScript file which loads a .NET v2 assembly from memory. - tyranid/DotNetToJScript
2.7. Windows Active Directory
描述地址利用後滲透進行攻擊和防禦Active DirectoryGitHub - infosecn1nja/AD-Attack-Defense: Attack and defend active directory using modern post exploitation adversary tradecraft activity
Attack and defend active directory using modern post exploitation adversary tradecraft activity - infosecn1nja/AD-Attack-Defense
內部模塊- 在不觸及LSASS的情況下讀取NTLM哈希值
GitHub - eladshamir/Internal-Monologue: Internal Monologue Attack: Retrieving NTLM Hashes without Touching LSASS
Internal Monologue Attack: Retrieving NTLM Hashes without Touching LSASS - eladshamir/Internal-Monologue
約束委派信息
黃金票據檢測
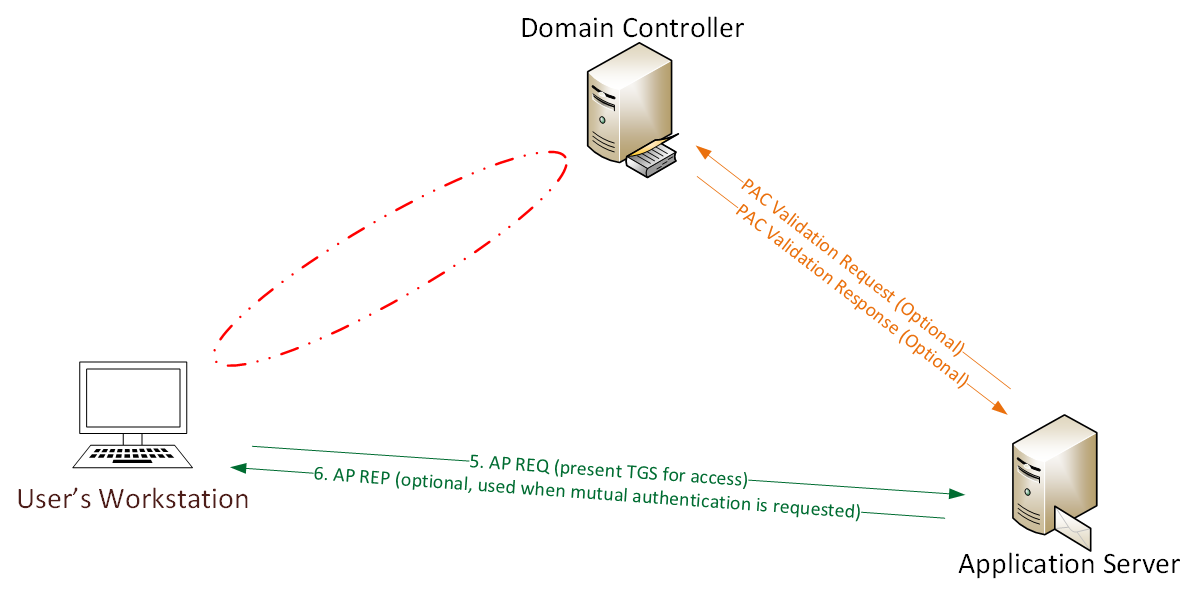
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory
Over the last 6 months, I have been researching forged Kerberos tickets, specifically Golden Tickets, Silver Tickets, and TGTs generated by MS14-068 exploit code (a type of Golden Ticket). I generated forged Kerberos tickets using Mimikatz (Mimikatz Command Reference) and MS14-068 exploits and...
adsecurity.org

Security alerts - Microsoft Defender for Identity
This article provides a list of the security alerts issued by Microsoft Defender for Identity.
docs.microsoft.com
3.MITER ATT&CK
MITRE的對抗戰術,技術和常識(ATT&CK™)是網絡對手行為的策劃知識庫和模型,反映了對手生命週期的各個階段以及他們已知的目標平台。 ATTCK有助於了解對抗已知對手行為的安全風險,規劃安全改進,並驗證防禦系統是否按預期工作。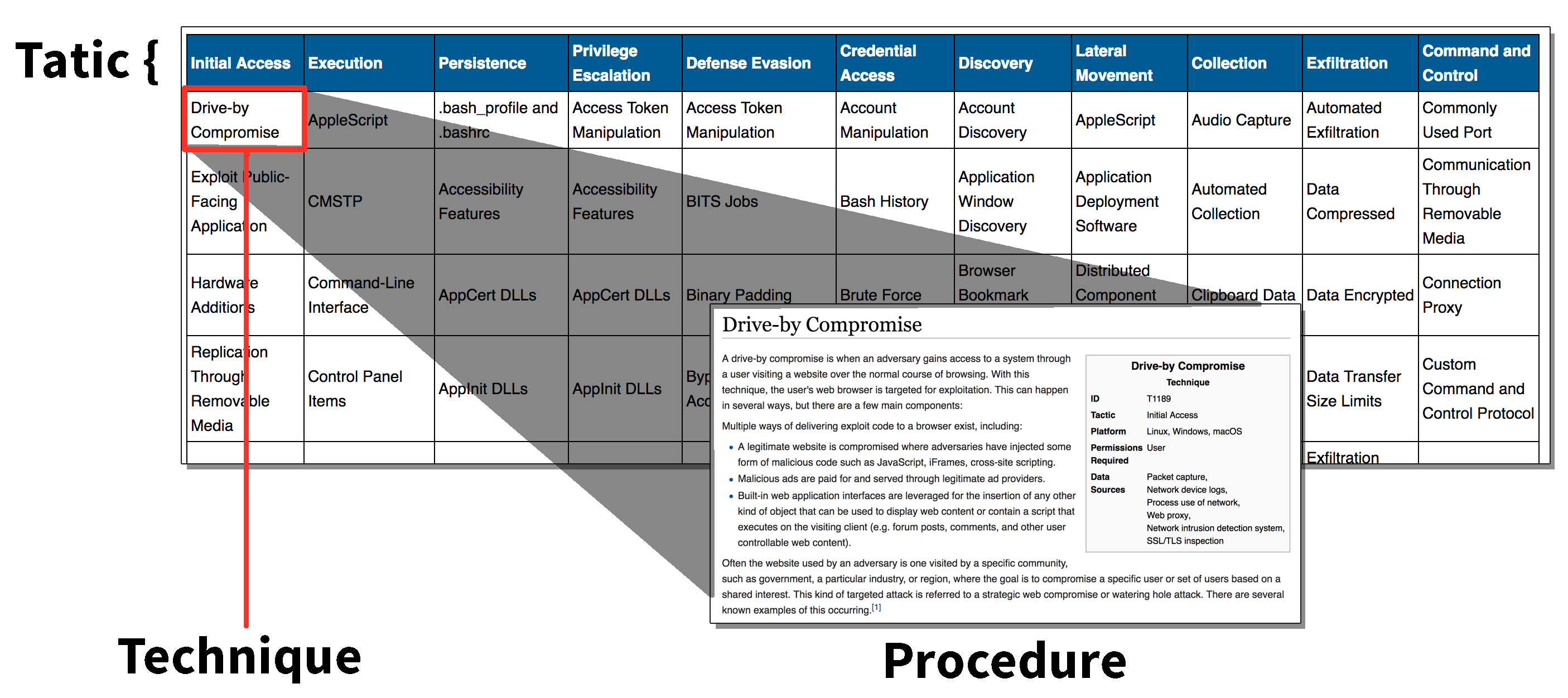
戰術是在行動中對目標可能使用的戰術目標。
技術描述了為實現其目標所採取的行動。
過程是執行操作所需的技術步驟
不管潛在的漏洞是什麼,這個框架提供了所有威脅行為的分類
紅隊可以通過技術研究和經驗來模擬真實的TTP攻擊。這些信息中的大部分都已提交給ATTCK。 TTCK可以被認為是TTP的菜單。紅隊可以利用這一點來確保他們有一套全面的攻擊戰術、技術和過程,藍隊可以利用這一點來建立一個計分卡,顯示他們在防禦各種戰術、技術和執行過程方面的能力。
參考:
描述地址TO&CC
PRE-TO&CC
ATT&CK Navigator
ATT&CK Navigator示例
4.红队备忘表
@harmj0yRed Team Cheat Sheets
CobaltStrike Beacon
PowerShell Empire
PowerSploit
PowerView
PowerUp
4.1Windows Active Directory
攻擊域信任指南http://www.harmj0y.net/blog/redteaming/a-guide-to-attacking-domain-trusts4.2.PowerView
Make PowerView Great Again4.3.SANS备忘表
PowerShellWindows Command Line
4.4.Blue Teaming Cheat Sheets
SANS Blue Team Wiki4.5.Powershell备忘表
PowerShell4.6.Bloodhound
5.红队建设清单
這套清單旨在幫助您規劃和建立一個紅隊。每種設計都可能有其他要求。使用此清單作為模板並根據需要進行修改。確定所需的知識和技能
確定並彌補知識所缺的方法
制定角色和責任指南
制定紅色團隊方法
為參與製定TTP指南
包括一些技巧
制定數據收集指南和工具
制定業務流程計劃
制定溝通計劃模板
制定ROE模板
制定技術簡報模板
制定報告模板
5.1.规划 - 红队建设核对清单
參與計劃RHE
事件溝通計劃
分散解決意見不一致過程
切入點/方法
範圍
目標(應至少解決以下一項問題)
保護
檢測
響應
恢復
目標限制
目標基礎設施/資產驗證/批准
場景利用
安全運營影響規劃
制定攻擊概況
網絡和主機活動
IOC生成(包括後續分析)和管理
規劃攻擊基礎設施
第1層
入侵防禦系統
系統
重定向器
PPS
第2層
入侵防禦系統
系統
重定向器
PPS
第3層
入侵防禦系統
系統
重定向器
PPS
將工具部署到基礎架構中
數據收集庫
5.2.执行 - 红队建设核对清单
每日完成和匯總確認獲取日誌信息
獲取屏幕截圖
獲取系統變化
每日(或每日兩次)強制性內部RT SITREP
更新實時攻擊圖
5.3.收尾 - 红队建设核对清单
紅隊攻擊結束匯總數據
回滾系統更改
已收集驗證數據
描述關鍵攻擊圖
技術評審
執行摘要
報告
攻擊性報告闡述
攻擊總結
完成攻擊圖
完成報告

